The Chinese state-sponsored group regarded as UNC3886 has been discovered to exploit a zero-day flaw in VMware ESXi hosts to backdoor Windows and Linux programs.
The VMware Equipment authentication bypass vulnerability, tracked as CVE-2023-20867 (CVSS rating: 3.9), “enabled the execution of privileged instructions throughout Windows, Linux, and PhotonOS (vCenter) guest VMs with no authentication of visitor credentials from a compromised ESXi host and no default logging on guest VMs,” Mandiant reported.
UNC3886 was to begin with documented by the Google-owned danger intelligence company in September 2022 as a cyber espionage actor infecting VMware ESXi and vCenter servers with backdoors named VIRTUALPITA and VIRTUALPIE.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Previously this March, the team was connected to the exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating method to deploy implants on the network appliances and interact with the aforementioned malware.
The threat actor has been explained as a “very adept” adversarial collective concentrating on defense, technology, and telecommunication organizations in the U.S., Japan, and the Asia-Pacific region.
“The team has access to extensive analysis and help for comprehension the underlying technology of appliances becoming focused,” Mandiant scientists stated, calling out its sample of weaponizing flaws in firewall and virtualization application that do not guidance EDR alternatives.
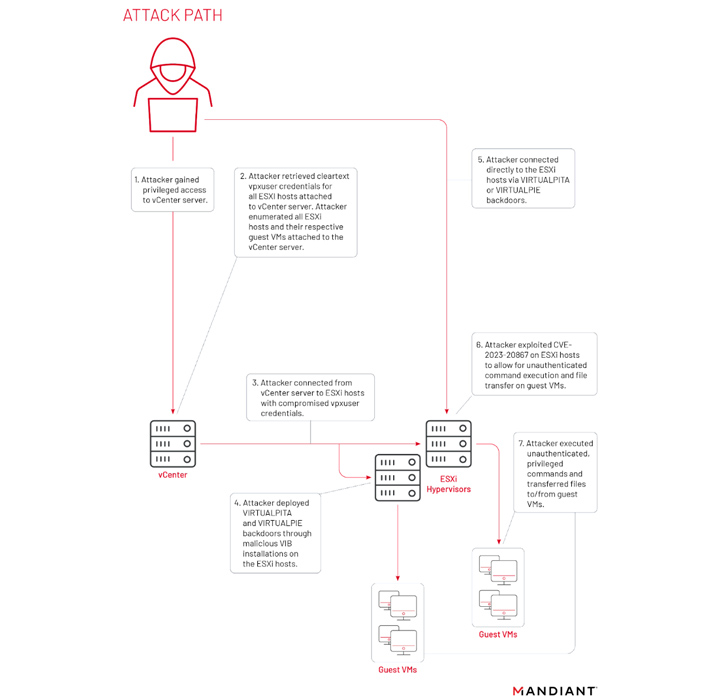
As section of its initiatives to exploit ESXi devices, the threat actor has also been observed harvesting credentials from vCenter servers as effectively as abusing CVE-2023-20867 to execute instructions and transfer information to and from guest VMs from a compromised ESXi host.
A noteworthy factor of UNC3886’s tradecraft is its use of Virtual Machine Interaction Interface (VMCI) sockets for lateral motion and ongoing persistence, thereby permitting it to create a covert channel among the ESXi host and its guest VMs.
Impending WEBINAR🔐 Mastering API Security: Knowledge Your Accurate Attack Floor
Learn the untapped vulnerabilities in your API ecosystem and take proactive ways in direction of ironclad security. Sign up for our insightful webinar!
Be part of the Session.wn-button,.wn-label,.wn-label:soon afterdisplay screen:inline-block.verify_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-sizing:13pxmargin:20px 0font-fat:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-leading:2px reliable #d9deffmargin: 8px.wn-titlefont-dimensions:21pxpadding:10px 0font-weight:900text-align:leftline-peak:33px.wn-descriptiontextual content-align:leftfont-dimensions:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-dimension:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-body weight:500letter-spacing:.2px
“This open up communication channel involving visitor and host, where by both function can act as consumer or server, has enabled a new indicates of persistence to get back entry on a backdoored ESXi host as prolonged as a backdoor is deployed and the attacker gains initial obtain to any guest equipment,” the corporation mentioned.
The advancement comes as Summoning Group researcher Sina Kheirkhah disclosed three different flaws in VMware Aria Operations for Networks (CVE-2023-20887, CVE-2023-20888, and CVE-2023-20889) that could consequence in distant code execution.
“UNC3886 carries on to present worries to investigators by disabling and tampering with logging expert services, selectively getting rid of log activities related to their exercise,” it even more added. “The risk actors’ retroactive cleanup performed in times of earlier general public disclosures on their action indicates how vigilant they are.”
Identified this write-up attention-grabbing? Observe us on Twitter and LinkedIn to browse much more exclusive written content we post.
Some parts of this post are sourced from:
thehackernews.com


 Malicious Actors Exploit GitHub to Distribute Fake Exploits
Malicious Actors Exploit GitHub to Distribute Fake Exploits