The U.S. government on Wednesday claimed the Chinese condition-sponsored hacking group known as Volt Typhoon experienced been embedded into some critical infrastructure networks in the country for at least 5 yrs.
Targets of the danger actor include things like communications, electricity, transportation, and drinking water and wastewater systems sectors in the U.S. and Guam.
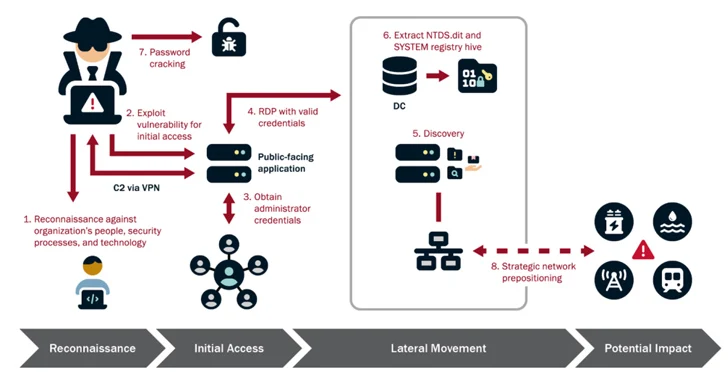
“Volt Typhoon’s option of targets and sample of actions is not dependable with regular cyber espionage or intelligence accumulating operations, and the U.S. authoring organizations assess with higher self-assurance that Volt Storm actors are pre-positioning themselves on IT networks to permit lateral movement to OT assets to disrupt functions,” the U.S. government explained.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The joint advisory, which was unveiled by the Cybersecurity and Infrastructure Security Agency (CISA), Countrywide Security Agency (NSA), and the Federal Bureau of Investigation (FBI), was also backed by other nations that are component of the 5 Eyes (FVEY) intelligence alliance comprising Australia, Canada, New Zealand, the U.K.
Volt Typhoon – which is also named Bronze Silhouette, Insidious Taurus, UNC3236, Vanguard Panda, or Voltzite – a stealthy China-based cyber espionage group that is thought to be active due to the fact June 2021.

It first arrived to gentle in May well 2023 when Microsoft uncovered that the hacking crew managed to set up a persistent foothold into critical infrastructure corporations in the U.S. and Guam for prolonged periods of time sans obtaining detected by principally leveraging living-off-the-land (LotL) procedures.
“This kind of tradecraft, recognized as ‘living off the land,’ makes it possible for attackers to function discreetly, with malicious exercise mixing in with authentic program and network actions making it tough to differentiate – even by businesses with additional experienced security postures,” the U.K. Nationwide Cyber Security Centre (NCSC) claimed.
A further hallmark tactic adopted by Volt Typhoon is the use of multi-hop proxies like KV-botnet to route destructive visitors by a network of compromised routers and firewalls in the U.S. to mask its correct origins.
Cybersecurity organization CrowdStrike, in a report printed in June 2023, known as out its reliance on an extensive arsenal of open up-supply tooling in opposition to a slender set of victims to reach its strategic ambitions.
“Volt Hurricane actors perform substantial pre-exploitation reconnaissance to study about the goal organization and its setting tailor their strategies, techniques, and treatments (TTPs) to the victim’s natural environment and devote ongoing assets to maintaining persistence and comprehension the focus on atmosphere in excess of time, even following preliminary compromise,” the organizations mentioned.

“The team also relies on valid accounts and leverages solid operational security, which put together, makes it possible for for long-phrase undiscovered persistence.”
Moreover, the nation-state has been noticed attempting to get hold of administrator credentials within the network by exploiting privilege escalation flaws, subsequently leveraging the elevated obtain to facilitate lateral motion, reconnaissance, and entire domain compromise.
The best purpose of the marketing campaign is to keep entry to the compromised environments, “methodically” re-targeting them above yrs to validate and expand their unauthorized accesses. This meticulous approach, per the organizations, is evidenced in scenarios in which they have frequently exfiltrated domain credentials to be certain obtain to current and valid accounts.
“In addition to leveraging stolen account credentials, the actors use LOTL procedures and keep away from leaving malware artifacts on units that would lead to alerts,” CISA, FBI, and NSA mentioned.

“Their robust aim on stealth and operational security makes it possible for them to retain prolonged-term, undiscovered persistence. More, Volt Typhoon’s operational security is increased by focused log deletion to conceal their actions inside of the compromised natural environment.”
The advancement will come as the Citizen Lab disclosed a network of at least 123 internet sites impersonating local information outlets spanning 30 nations in Europe, Asia, and Latin The usa that is pushing pro-China written content in a prevalent affect campaign linked to a Beijing public relations business named Shenzhen Haimaiyunxiang Media Co., Ltd.
The Toronto-centered digital watchdog, which dubbed the impact operation PAPERWALL, reported it shares similarities with HaiEnergy, albeit with diverse operators and exceptional TTPs.
“A central attribute of PAPERWALL, noticed throughout the network of web-sites, is the ephemeral nature of its most intense factors, whereby article content attacking Beijing’s critics are routinely taken off from these web sites some time after they are published,” the Citizen Lab stated.
In a assertion shared with Reuters, a spokesperson for China’s embassy in Washington explained “it is a typical bias and double typical to allege that the pro-China contents and reports are ‘disinformation,’ and to simply call the anti-China ones’ genuine information.'”
Found this report interesting? Comply with us on Twitter and LinkedIn to browse additional unique written content we article.
Some sections of this post are sourced from:
thehackernews.com

 Unified Identity – look for the meaning behind the hype!
Unified Identity – look for the meaning behind the hype!