If you’ve listened to computer software distributors in the identification area lately, you will have found that “unified” has quickly turn into the buzzword that everybody is adopting to describe their portfolio. And this is good! Unified identification has some astounding advantages!
Even so (there is often a nevertheless, suitable?) not each “unified” “identification” “security” “platform” is built equivalent. Some vendors simply call the combination of workforce IDaaS and client IDaaS a unified identification solution, even though many others present a glorified 2FA provider – unified only in the head of their entrepreneurs.
Your landscape matters!
So ignore for a minute what the vendors claim, and assume back to your group and your identity security landscape. Consider this new definition: “unified” is what has the skill to consolidate your identity challenges with a full identification solution.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Here’s an instance: you are liable for the id infrastructure of a big healthcare facility. Frontline workers, administrative workers, audit/compliance requires and a massive number of exterior customers. You are employing Lively Listing, and your LOB application will not do id. For this medical center, unified identity suggests robust access management for clients and frontline workers, powerful joiner-leaver-mover handling, Ad hardening and business-quality reporting. Just about anything a lot less fails the unified promise and suggests their internal identification landscape stays fractured.
Yet another case in point: a tiny software package dev studio. They want further sturdy controls on Privileged Accessibility Administration (PAM) to protect the enhancement pipeline and make certain they would not grow to be the first attack vector in a supply chain attack. But they also require Id Governance and Administration (IGA) for device entities and their house owners, operating on the quite a few automatic duties they are functioning. A resolution which addresses PAM and IGA independently from each and every other is not unified.
What is the value of unified identity in any case?
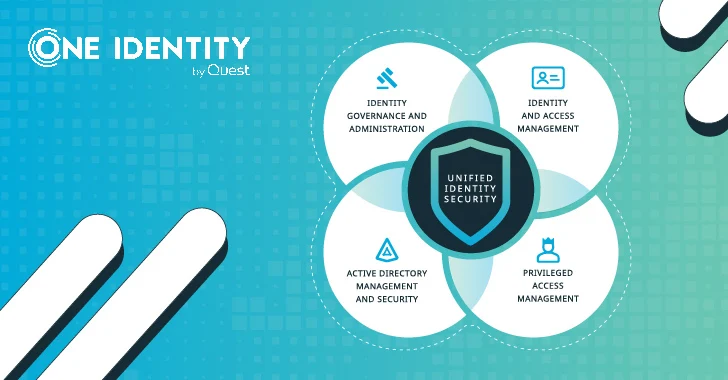
So why has “unified identity ” come to be these kinds of a incredibly hot buzzword? Well, there are some genuinely great arguments for it. Historically, the id space was quite fractured, with several authorities not even contemplating it a singular current market until eventually rather a short while ago. Identity Governance and Administration (IGA), Entry Management (AM), and Privileged Entry Administration (PAM) had been the essential sub-markets, with a extensive array of adjacent areas these types of as Advertisement bridging and endpoint privilege management.
The key driver for unified identity is this excessive fragmentation: a huge corporation has on typical 45 various security resources. Include to this the identification sprawl, a pattern the place businesses keep finding additional and a lot more identity silos in-house – a A single Identification study displays half the companies are employing additional than 25 various techniques to regulate entry legal rights. This is only not sustainable, and incorporating a new tool just about every time a new risk approaches is totally unworkable. So corporations are hunting to consolidate vendors, decrease complexity and trim down the number of suppliers they work with. The benefits of a Unified Id Platform are a improved cybersecurity posture and better resilience in the facial area of security threats, even though expanding simplicity and enabling agility.
An additional reason is top rated line price: bundles, quantity discounts and ELAs are a simple way to lessen charges. Seller consolidation also brings some fewer evident financial savings as well: a solitary tech stack helps the skills gap, easing the pressure on selecting and coaching, which in turn indicates sizeable discounts on headcount and may lessen the necessity for remarkably qualified senior staff, creating additional value from security with a lot less means or set an additional way, functioning smarter not more challenging.
Integration is a critical aspect of the identity landscape – and just one of the greatest head aches. Security resources want to do the job jointly efficiently, but which is rarely a provided. The sector is not keen on popular specifications, which can make interoperability really really hard to accomplish. With some hard work (this means customization, help several hours and overhead) id solutions can work jointly pairwise, but producing a complete ecosystem of identity applications that operate flawless together is a unusual achievement. It’s effortless to see the value a unified identification platform brings here. The tools are pre-examined, pre-validated to do the job jointly, usually with out any customization demanded, and the platform parts are supported as one by the seller.
This provides us to the remaining advantage: more quickly time to value, an expression deserving of any MBA graduate. Identity and entry management (IAM) initiatives are renowned for getting a prolonged time to carry out, as professionals meticulously formalize small business processes and put into action them in code or configuration. In massive businesses, this is an extremely sophisticated undertaking, as the IAM setup wants to mirror every component (and quirk) the organization has constructed up – at times over many years. Implementations turn out to be so sophisticated that they just fail – the charge and time overruns exceeding the patience of business leaders. In a nutshell: time to price matters in IAM. And a unified id solution gets rid of the complexity of the multi-vendor approach, getting rid of at minimum a person factor.
After these added benefits, let’s talk a downside: vendor lock-in. Unified identity appears amazing but betting the house on a one seller is a high request. And what if you already have some remedies in location that you are happy with? It can be essential to keep in mind that not all unified identity distributors are the exact same Some distributors provide modular identity platforms which allow you to keep what you want and unify what you want. This technique enables prospects to start off the unification at any stage (for illustration with PAM) with no the have to have to embrace and put into action all places in one large leap. When selecting suppliers, glance for this adaptable strategy.
Located this report appealing? Stick to us on Twitter and LinkedIn to browse far more special content we post.
Some parts of this report are sourced from:
thehackernews.com

 HijackLoader Evolves: Researchers Decode the Latest Evasion Methods
HijackLoader Evolves: Researchers Decode the Latest Evasion Methods