A Chinese-talking danger actor codenamed GoldFactory has been attributed to the growth of hugely subtle banking trojans, which includes a formerly undocumented iOS malware named GoldPickaxe that is able of harvesting identity files, facial recognition facts, and intercepting SMS.
“The GoldPickaxe relatives is readily available for both equally iOS and Android platforms,” Singapore-headquartered Group-IB claimed in an intensive report shared with The Hacker Information. “GoldFactory is believed to be a well-structured Chinese-talking cybercrime team with shut connections to Gigabud.”
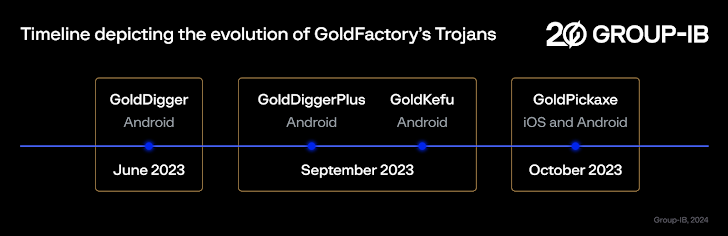
Active considering the fact that at minimum mid-2023, GoldFactory is also responsible for an additional Android-primarily based banking malware identified as GoldDigger and its increased variant GoldDiggerPlus as nicely as GoldKefu, an embedded trojan inside GoldDiggerPlus.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
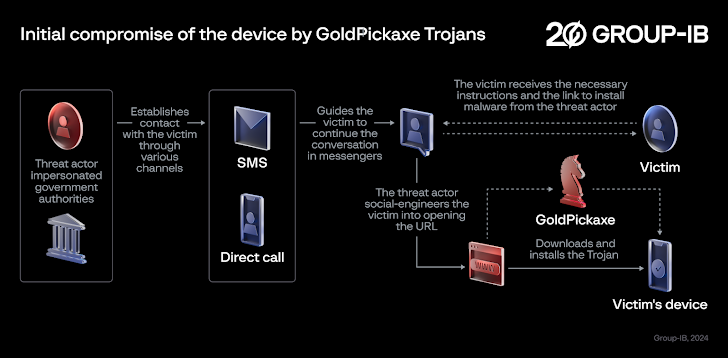
Social engineering strategies distributing the malware have been discovered to goal the Asia-Pacific region, specifically Thailand and Vietnam, by masquerading as local banks and govt organizations.
In these attacks, potential victims are despatched smishing and phishing messages and guided to change the discussion to prompt messaging apps like LINE, prior to sending bogus URLs that direct to the deployment of GoldPickaxe on the equipment.
Some of these malicious applications targeting Android are hosted on counterfeit sites resembling Google Participate in Retail outlet internet pages or bogus corporate sites to entire the installation approach.

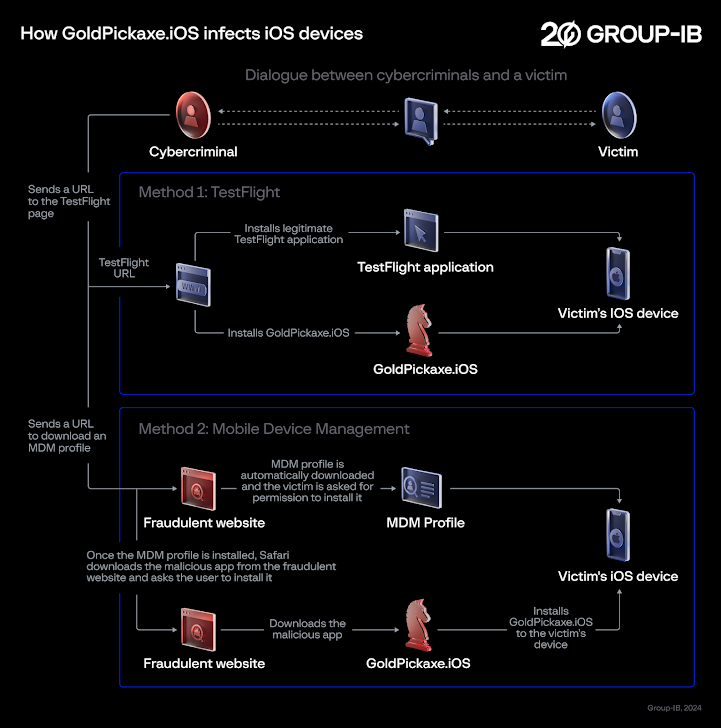
GoldPickaxe for iOS, nevertheless, employs a various distribution scheme, with successive iterations leveraging Apple’s TestFlight system and booby-trapped URLs that prompt buyers to download an Mobile Gadget Management (MDM) profile to grant entire handle around the iOS gadgets and put in the rogue app.
Both equally these propagation mechanisms were disclosed by the Thailand Banking Sector CERT (TB-CERT) and the Cyber Crime Investigation Bureau (CCIB), respectively, in November 2023.
The sophistication of GoldPickaxe is also obvious in the truth that it is really created to get all over security steps imposed by Thailand that demand end users to ensure larger sized transactions using facial recognition to protect against fraud.
“GoldPickaxe prompts the target to history a online video as a affirmation method in the faux software,” security researchers Andrey Polovinkin and Sharmine Small mentioned. “The recorded video is then employed as raw materials for the development of deepfake films facilitated by encounter-swapping synthetic intelligence services.”
In addition, the Android and iOS flavors of the malware are geared up to accumulate the victim’s ID files and photos, intercept incoming SMS messages, and proxy targeted traffic as a result of the compromised system. It truly is suspected that the GoldFactory actors use their personal units to sign-in to the bank application and execute unauthorized fund transfers.
That acquiring stated, the iOS variant exhibits less functionalities when in comparison to its Android counterpart owing to the closed mother nature of the iOS running method and rather stricter character of iOS permissions.
The Android edition – viewed as an evolutionary successor of GoldDiggerPlus – also poses as around 20 unique programs from Thailand’s authorities, the monetary sector, and utility corporations to steal login qualifications from these expert services. On the other hand, it can be currently not crystal clear what the danger actors do with this data.
A different noteworthy facet of the malware is its abuse of Android’s accessibility expert services to log keystrokes and extract on-monitor material.

GoldDigger also shares code-degree similarities to GoldPickaxe, although it is mainly developed to steal banking qualifications, though the latter is geared additional to accumulating of private information and facts from victims. No GoldDigger artifacts aimed at iOS products have been recognized to date.
“The primary function of GoldDigger is that it targets in excess of 50 apps from Vietnamese economic businesses, together with their packages’ names in the trojan,” the scientists claimed. “Each time the focused programs open, it will help you save the text shown or composed on the UI, including passwords, when they are entered.”
The base edition of GoldDigger, which was initially found in June 2023 and continues to be even now in circulation, has due to the fact paved the way for a lot more upgraded variants, like GoldDiggerPlus, which comes embedded with another trojan APK ingredient dubbed GoldKefu, to unleash the malicious steps.
GoldDiggerPlus is mentioned to have emerged in September 2023, with GoldKefu impersonating a popular Vietnamese messaging application to siphon banking qualifications involved with 10 monetary establishments.

Goldkefu also integrates with the Agora Application Enhancement Kit (SDK) to facilitate interactive voice and video clip calls and trick victims into contacting a bogus bank buyer provider by sending pretend alerts that induce a bogus perception of urgency by proclaiming that a fund transfer to the tune of 3 million Thai Baht has taken place on their accounts.
If something, the progress is a indicator that the cellular malware landscape stays a worthwhile industry for cybercriminals hunting for fast economical gain, even as they obtain strategies to circumvent defensive measures erected by banking institutions to counter this kind of threats. It also demonstrates the ever-shifting and dynamic nature of social engineering techniques that purpose to provide malware to victims’ products.
To mitigate the dangers posed by GoldFactory and its suite of mobile banking malware, it really is strongly recommended not to click on on suspicious backlinks, set up any app from untrusted web-sites, as they are a widespread vector for malware, and periodically evaluation the permissions specified to apps, particularly individuals requesting for Android’s accessibility providers.
“GoldFactory is a resourceful crew adept at a variety of ways, like impersonation, accessibility keylogging, pretend banking websites, phony financial institution alerts, bogus contact screens, id, and facial recognition facts assortment,” the researchers stated. “The staff contains different growth and operator teams focused to specific locations.”
“The gang has effectively-defined procedures and operational maturity and frequently improves its toolset to align with the qualified setting showcasing a high proficiency in malware improvement.”
Found this post attention-grabbing? Stick to us on Twitter and LinkedIn to read extra exclusive material we publish.
Some areas of this short article are sourced from:
thehackernews.com


 Critical Exchange Server Flaw (CVE-2024-21410) Under Active Exploitation
Critical Exchange Server Flaw (CVE-2024-21410) Under Active Exploitation