With numerous of the highly publicized 2023 cyber attacks revolving all around a single or far more SaaS programs, SaaS has turn into a induce for genuine issue in a lot of boardroom discussions. Extra so than ever, considering that GenAI programs are, in point, SaaS programs.
Wing Security (Wing), a SaaS security business, performed an evaluation of 493 SaaS-using businesses in Q4 of 2023. Their study reveals how providers use SaaS nowadays, and the large assortment of threats that final result from that usage. This distinctive evaluation presents uncommon and essential insights into the breadth and depth of SaaS-similar hazards, but also delivers useful tips to mitigate them and guarantee SaaS can be extensively applied devoid of compromising security posture.
The TLDR Version Of SaaS Security
2023 introduced some now infamous examples of destructive gamers leveraging or right targeting SaaS, which include the North Korean group UNC4899, 0ktapus ransomware group, and Russian Midnight Blizzard APT, which specific nicely-recognized companies these types of as JumpCloud, MGM Resorts, and Microsoft (respectively), and likely a lot of many others that generally go unannounced.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The 1st perception from this analysis cements the concept that SaaS is the new supply chain, offering an practically intuitive framework to the worth of securing SaaS usage. These applications are plainly an integral portion of the present day organization’s established of resources and suppliers. That said, prolonged gone are the days when every single 3rd party with accessibility to company information had to go by means of security or IT approval. Even in the most arduous organizations, when a diligent employee wants a swift and economical resolution, they will search it up and use it to get their jobs’ done more quickly and far better. Once again, think of the prevalent use of GenAI, and the picture is distinct.
As such, any corporation concerned about the security of its supply chain have to undertake SaaS security actions. According to the MITRE ATT&CK procedure ‘Trusted Relationships’ (T1199), a supply chain attack occurs when an attacker targets a vendor to exploit it as a suggests to infiltrate a broader network of companies. By entrusting sensitive info to external SaaS sellers, corporations subject matter them selves to supply chain hazards that reach beyond quick security problems.
4 Widespread SaaS Dangers
There are various reasons and techniques in which SaaS is becoming specific. The excellent information is that most of the pitfalls can be significantly mitigated when monitored and managed. Fundamental SaaS security abilities are even cost-free, suited for businesses that are just starting to build their SaaS security posture or need to have to review it to their present-day answer.
1) Shadow SaaS
The very first dilemma with SaaS utilization is the reality that it normally goes fully unnoticed: The amount of programs made use of by companies is usually 250% greater than what a primary and typically-utilized question of the workspace reveals.
Among the companies analyzed:
- 41% of programs were being made use of by only a single person, ensuing in a really long tail of unsanctioned apps.
- 1 out of 5 end users have been employing programs not utilised by everyone else in their organization, creating security and resource strains.
- 63% of solitary-user programs ended up not even accessed inside a 3-month period of time, begging the query – why preserve them related to enterprise details?
- 96.7% of businesses applied at least one application that had a security incident in the earlier yr, solidifying the continuous risk and have to have for proper mitigation.
2) MFA Bypassing
Wing’s analysis signifies a trend where by users choose to use a username/password to accessibility the products and services they want, bypassing the security measures in position (see impression 1).
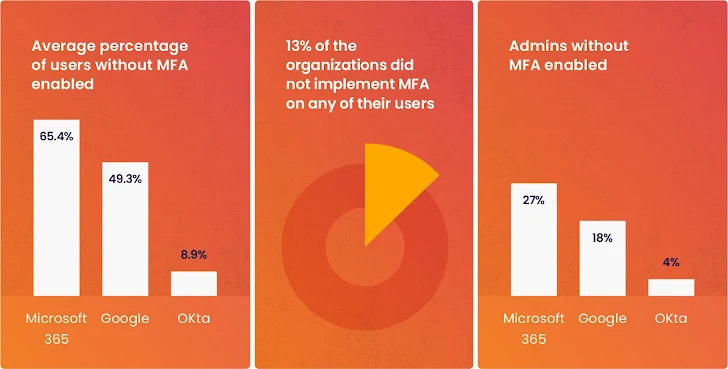 Graphic 1: From Wing Security’s investigate, bypassing MFA.
Graphic 1: From Wing Security’s investigate, bypassing MFA.
3) Overlooked tokens
Consumers grant the apps they need to have tokens this is necessary for the SaaS applications to provide their purpose. The difficulty is that these tokens are normally neglected about after a several or just one particular use. Wing’s investigate unveiled a big existence of unused tokens over a interval of 3 months, making an unnecessarily huge attack surface for many consumers (Picture 2).
4) The new risk of Shadow AI
In the starting of 2023, security teams generally concentrated on a pick out couple renowned products and services providing access to AI-based mostly styles. Having said that, as the calendar year progressed, thousands of common SaaS purposes adopted AI products. The exploration shows that 99.7% of providers have been employing programs with integrated AI abilities.
Corporations have been needed to agree to updated terms and circumstances permitting these purposes to employ and refine their versions working with the organizations’ most private information. Often, these revised terms and circumstances slipped beneath the radar, alongside with the use of AI itself.
There are unique means in which AI programs could use your information for their instruction designs. This can occur in the type of understanding your facts, storing your data and even obtaining a human manually go in excess of your knowledge to boost the AI product. In accordance to Wing, this capability is generally configurable and fully avoidable, presented it is not missed.
Solving SaaS Security Difficulties In 2024
The report finishes on a good be aware, listing 8 techniques in which companies can mitigate the increasing danger of the SaaS source chain. Such as:
For the whole record of results, ideas on making certain harmless SaaS usage and a 2024 SaaS security forecast, down load the comprehensive report right here.
Observed this post fascinating? This post is a contributed piece from 1 of our valued associates. Adhere to us on Twitter and LinkedIn to read extra exceptional content we article.
Some components of this article are sourced from:
thehackernews.com

 Chinese Hackers Using Deepfakes in Advanced Mobile Banking Malware Attacks
Chinese Hackers Using Deepfakes in Advanced Mobile Banking Malware Attacks