The sophisticated persistent threat (APT) team referred to as Evasive Panda has been observed focusing on an global non-governmental business (NGO) in Mainland China with malware shipped by way of update channels of legit programs like Tencent QQ.
The attack chains are developed to distribute a Windows installer for MgBot malware, ESET security researcher Facundo Muñoz reported in a new report revealed today. The exercise commenced in November 2020 and continued in the course of 2021.
Evasive Panda, also known as Bronze Highland and Daggerfly, is a Chinese-speaking APT team that has been attributed to a collection of cyber espionage attacks focusing on several entities in China, Hong Kong, and other nations around the world located in East and South Asia because at the very least late December 2012.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The group’s hallmark is the use of the customized MgBot modular malware framework, which is able of obtaining supplemental elements on the fly to expand on its intelligence-collecting capabilities.
Some of the prominent abilities of the malware include things like stealing files, logging keystrokes, harvesting clipboard facts, recording audio streams, and credential theft from web browsers.
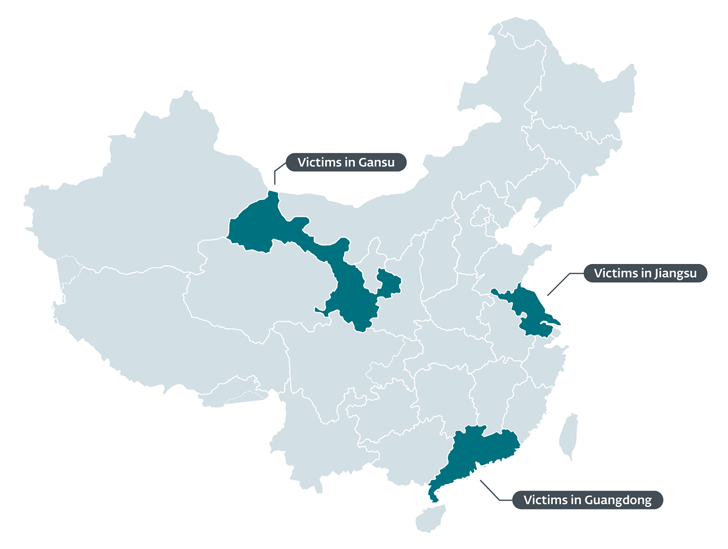
ESET, which learned the marketing campaign in January 2022 following a reputable Chinese application was applied to deploy an installer for the MgBot backdoor, stated the qualified people ended up located in the Gansu, Guangdong, and Jiangsu provinces and are members of an unnamed global NGO.
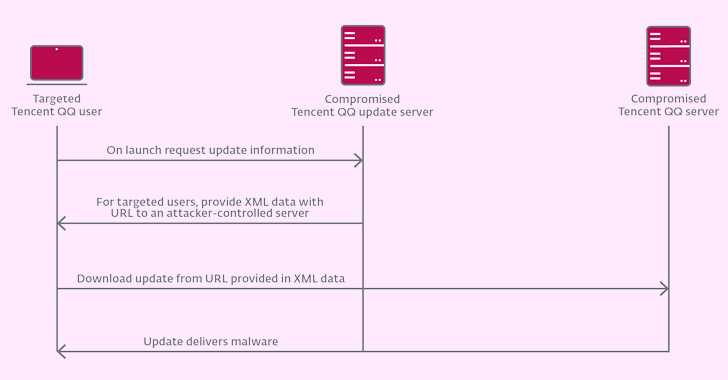
The trojanized application is the Tencent QQ Windows client software package updater (“QQUrlMgr.exe”) hosted on the area “update.browser.qq[.]com.” It can be not instantly distinct how the danger actor managed to deliver the implant via genuine updates.
But it points to either of the two eventualities, a source chain compromise of Tencent QQ’s update servers or a circumstance of an adversary-in-the-center (AitM) attack, as comprehensive by Kaspersky in June 2022 involving a Chinese hacking crew dubbed LuoYu.
In the latest a long time, many software package supply chain attack has been orchestrated by country-state teams from Russia, China, and North Korea. The ability to get a significant malicious footprint promptly has not been misplaced on these attackers, who are more and more focusing on the IT offer chain to breach company environments.
Impending WEBINARZero Have faith in + Deception: Discover How to Outsmart Attackers!
Find how Deception can detect state-of-the-art threats, halt lateral motion, and boost your Zero Belief method. Sign up for our insightful webinar!
Help you save My Seat!
“AitM kinds of interception would be achievable if the attackers – both LuoYu or Evasive Panda – had been equipped to compromise vulnerable gadgets these kinds of as routers or gateways,” Muñoz elaborated.
“With obtain to ISP spine infrastructure – via lawful or unlawful indicates – Evasive Panda would be capable to intercept and reply to the update requests performed by means of HTTP, or even modify packets.”
This is major as the conclusions appear significantly less than a 7 days following Broadcom-owned Symantec thorough attacks mounted by the menace actor in opposition to telecom provider vendors in Africa working with the MgBot malware framework.
Found this report exciting? Comply with us on Twitter and LinkedIn to go through additional distinctive information we publish.
Some pieces of this report are sourced from:
thehackernews.com

 Browser Security Survey: 87% of SaaS Adopters Exposed to Browser-borne Attacks
Browser Security Survey: 87% of SaaS Adopters Exposed to Browser-borne Attacks