A suspected Chinese-speaking danger actor has been attributed to a destructive marketing campaign that targets the Uzbekistan Ministry of Foreign Affairs and South Korean buyers with a distant entry trojan known as SugarGh0st RAT.
The action, which commenced no later on than August 2023, leverages two different an infection sequences to provide the malware, which is a customized variant of Gh0st RAT (aka Farfli).
It comes with options to “aid the remote administration duties as directed by the C2 and modified conversation protocol based mostly on the similarity of the command construction and the strings utilized in the code,” Cisco Talos researchers Ashley Shen and Chetan Raghuprasad said.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
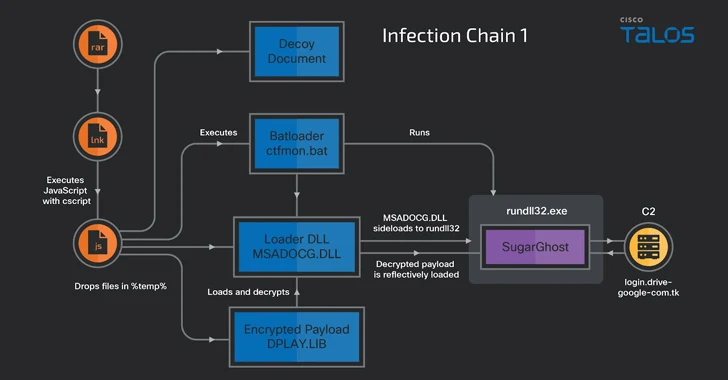
The attacks commence with a phishing email bearing decoy files, opening which activates a multi-phase procedure that sales opportunities to the deployment of SugarGh0st RAT.

The decoy documents are integrated inside a intensely obfuscated JavaScript dropper that is contained in a Windows Shortcut file embedded in the RAR archive email attachment.
“The JavaScript decodes and drops the embedded files into the %TEMP% folder, which include a batch script, a custom-made DLL loader, an encrypted SugarGh0st payload, and a decoy doc,” the researchers claimed.
The decoy doc is then exhibited to the victim, although, in the history, the batch script operates the DLL loader, which, in change, side-masses it with a copied variation of a respectable Windows executable termed rundll32.exe to decrypt and start the SugarGh0st payload.
A next variant of the attack also starts with a RAR archive that contains a malicious Windows Shortcut file that masquerades as a entice, with the big difference becoming that the JavaScript leverages DynamicWrapperX to operate shellcode that launches SugarGh0st.
SugarGh0st, a 32-little bit dynamic-website link library (DLL) created in C++, establishes get hold of with a tricky-coded command-and-regulate (C2) area, enabling it to transmit method metadata to the server, launch a reverse shell, and operate arbitrary commands.
It can also enumerate and terminate procedures, acquire screenshots, perform file functions, and even clear the machine’s function logs in an try to go over its tracks and evade detection.
The campaign’s back links to China stem from Gh0st RAT’s Chinese origins and the truth that the totally useful backdoor has been broadly adopted by Chinese menace actors over the decades, in part pushed by the release of its source code in 2008. A different smoking cigarettes gun evidence is the use of Chinese names in the “final modified by” area in the metadata of the decoy files.

“The Gh0st RAT malware is a mainstay in the Chinese threat actors’ arsenal and has been energetic due to the fact at least 2008,” the scientists said.
“Chinese actors also have a heritage of targeting Uzbekistan. The targeting of the Uzbekistan Ministry of Foreign Affairs also aligns with the scope of Chinese intelligence exercise abroad.”
The growth comes as Chinese state-sponsored groups have also increasingly specific Taiwan in the very last 6 months, with the attackers repurposing residential routers to mask their intrusions, in accordance to Google.
Identified this post interesting? Follow us on Twitter and LinkedIn to browse extra unique material we publish.
Some elements of this short article are sourced from:
thehackernews.com

 Discover How Gcore Thwarted Powerful 1.1Tbps and 1.6Tbps DDoS Attacks
Discover How Gcore Thwarted Powerful 1.1Tbps and 1.6Tbps DDoS Attacks