The most latest Gcore Radar report and its aftermath have highlighted a remarkable boost in DDoS attacks across multiple industries. At the commencing of 2023, the common toughness of attacks arrived at 800 Gbps, but now, even a peak as higher as 1.5+ Tbps is unsurprising. To consider and split via Gcore’s defenses, perpetrators created two tries with two distinct tactics. Browse on to learn what took place and understand how the security provider stopped the attackers in their tracks devoid of impacting end users’ activities.
A Impressive DDoS Attacks
In November 2023, one of Gcore’s clients from the gaming sector was focused by two enormous DDoS attacks, peaking at 1.1 and 1.6 Tbps respectively. The attackers deployed many methods in an unsuccessful attempt to compromise Gcore’s protecting mechanisms.
Attack #1: 1.1 Tbps UDP-primarily based DDoS
In the very first cyber assault, the attackers despatched a barrage of UDP targeted visitors to a concentrate on server, peaking at 1.1 Tbps. Two techniques were used:

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
- By using random UDP resource ports, they hoped to evade typical filtering mechanisms.
- The attackers hid their authentic identity by forging resource IP addresses.
This was a traditional flood (or volumetric) attack, whereby the attackers hoped to take in all readily available bandwidth of or to a details centre or network, too much to handle the goal servers with site visitors and generating them unavailable to reputable customers.
The graph under displays customer’s visitors in the course of the attack. The peak of 1.1 Tbps reveals an aggressive but limited-lived endeavor to flood the network with information. The green line (“total.normal.enter”) reveals all inbound site visitors. The other colored strains on the graph stand for the network’s responses, such as measures to filter and fall destructive traffic, as the procedure manages the deluge of facts.
 The attack comprised a shorter but extreme peak of 1.1 Tbps close to 22:55
The attack comprised a shorter but extreme peak of 1.1 Tbps close to 22:55
Attack #2: 1.6 Tbps TCP-centered DDoS
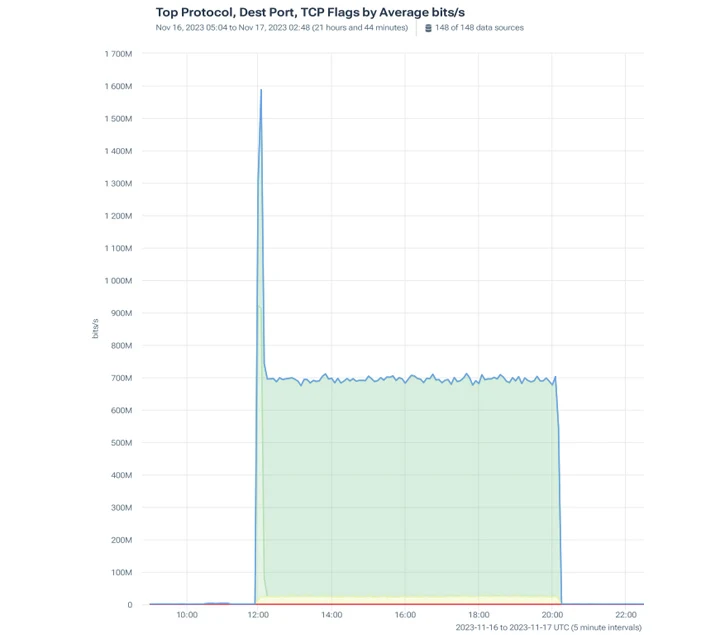 The attack’s reliable targeted visitors volume was 700 Mbps and at the onset peaked at 1600 Mbps
The attack’s reliable targeted visitors volume was 700 Mbps and at the onset peaked at 1600 Mbps
This time, the attackers attempted to exploit TCP protocol with a mix of SYN flood, PSH, and ACK targeted visitors.
In a SYN flood attack, various SYN packets are sent to the concentrate on server devoid of ACK packets. This means the server generates a fifty percent-open up link for every single SYN packet. If thriving, the server will finally operate out of methods and quit accepting connections.
The PSH, ACK period of the attack promptly sends information to the focus on program. The ACK flag signals that the server gained the preceding packet. This pushes the technique to cope with facts instantly, wasting means. A SYN flood assault making use of PSH, ACK packets is more challenging to protect in opposition to than a SYN flood, due to the fact the PSH flag leads to the server to process the packet contents straight away, consuming extra assets.
As prior to, the target was to overload the customer’s servers and make their services inaccessible to licensed people. This SYN flood had a peak quantity of 685.77 Mbps and the PSH, ACK experienced a magnitude of 906.73 Mbps.
Gcore’s Defensive Procedures
Gcore’s DDoS Defense correctly neutralized both equally attacks though preserving common provider for the customer’s finish buyers. The basic tactic of fending off DDoS security threats contains numerous procedures, these types of as Gcore’s entrance-line defenses:
- Dynamic website traffic shaping: Dynamically altered visitors costs efficiently mitigate the affect of the attack when making sure the continuity of critical services. In order to prioritize real traffic even though slowing damaging transmissions, adaptive thresholds and level restrictions are used.
- Anomaly detection and quarantine: Versions dependent on machine discovering examine actions to detect anomalies. When an anomaly occurs, automated quarantine mechanisms redirect erroneous visitors to isolated segments for added analysis.
- Normal expression filters: To block malicious payloads devoid of disrupting respectable website traffic, standard expression-based filter regulations are carried out. Their ongoing great-tuning assures optimum security without having fake positives.
- Collaborative risk intelligence: Gcore actively engages in the trade of risk intelligence with marketplace friends. Collective insights and real-time menace feeds information Gcore’s security techniques, enabling a immediate reaction to building attack vectors.
By utilizing these procedures, Gcore was equipped to properly mitigate the impact of DDoS attacks and shield their customer’s system from disruption, negating probable reputational and money losses.
Conclusion
DDoS attacks of 1.5+ Tbps quantity pose an rising danger throughout industries, with attackers using imaginative approaches to try and bypass defense solutions. Over the training course of 2023, Gcore has registered will increase in equally typical and greatest attack volumes, and these two related attacks demonstrate that trend.
In the attacks included in the short article, Gcore was equipped to protect against any problems via a combination of dynamic site visitors shaping, anomaly detection, normal expression filters, and collaborative menace intelligence. Discover DDoS Safety choices to secure your network against ever-evolving DDoS threats.
Uncovered this write-up appealing? Observe us on Twitter and LinkedIn to browse more distinctive content we post.
Some pieces of this write-up are sourced from:
thehackernews.com


 WhatsApp’s New Secret Code Feature Lets Users Protect Private Chats with Password
WhatsApp’s New Secret Code Feature Lets Users Protect Private Chats with Password