A Chinese condition-sponsored espionage team regarded as Override Panda has resurfaced in modern weeks with a new phishing attack with the target of thieving delicate data.
“The Chinese APT made use of a spear-phishing email to provide a beacon of a Red Staff framework known as ‘Viper,'” Cluster25 stated in a report revealed past week.
“The goal of this attack is now unidentified but with higher chance, specified the former history of the attack perpetrated by the team, it may well be a government establishment from a South Asian place.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Override Panda, also termed Naikon, Hellsing, and Bronze Geneva, is known to run on behalf of Chinese pursuits because at least 2005 to carry out intelligence-gathering functions targeting ASEAN nations around the world.
Attack chains unleashed by the menace actor have associated the use of decoy documents hooked up to spear-phishing e-mails that are developed to entice the meant victims to open and compromise by themselves with malware.
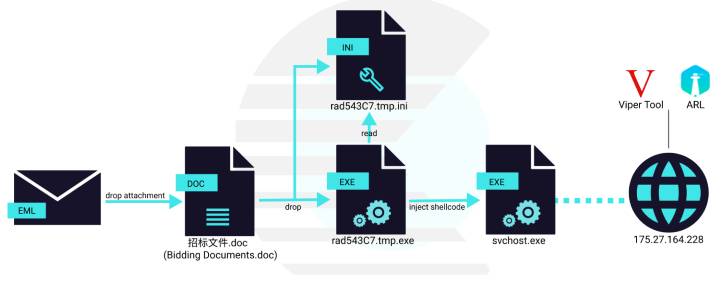
Last April, the group was connected to a broad-ranging cyberespionage marketing campaign directed versus army corporations in Southeast Asia. Then in August 2021, Naikon was implicated in cyberattacks focusing on the telecom sector in the area in late 2020.
The most up-to-date campaign noticed by Cluster25 is no different in that it leverages a weaponized Microsoft Office environment doc to kick-begin the an infection killchain that features a loader made to launch a shellcode, which, in change, injects a beacon for the Viper pink group software.

Offered for down load from GitHub, Viper is described as a “graphical intranet penetration device, which modularizes and weaponizes the practices and technologies usually used in the approach of Intranet penetration.”
The framework, identical to Cobalt Strike, is claimed to feature more than 80 modules to aid preliminary access, persistence, privilege escalation, credential Accessibility, lateral motion, and arbitrary command execution.
“By observing Naikon APT’s hacking arsenal, it was concluded that this team tends to conduct extensive-phrase intelligence and espionage functions, common for a group that aims to perform attacks on overseas governments and officers,” the researchers pointed out.
“To keep away from detection and improve the end result, it adjusted distinct [tactics, techniques, and procedures] and tools above time.”
Uncovered this post interesting? Adhere to THN on Fb, Twitter and LinkedIn to read extra exclusive written content we publish.
Some elements of this write-up are sourced from:
thehackernews.com


 Which Hole to Plug First? Solving Chronic Vulnerability Patching Overload
Which Hole to Plug First? Solving Chronic Vulnerability Patching Overload