Quite a few industries—including technology, fiscal products and services, vitality, healthcare, and government—are dashing to integrate cloud-centered and containerized web applications.
The benefits are undeniable on the other hand, this shift offers new security issues.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
OPSWAT’s 2023 Web Application Security report reveals:
- 75% of companies have modernized their infrastructure this calendar year.
- 78% have increased their security budgets.
- Nevertheless just 2% are self-assured in their security posture.
Let us take a look at why self confidence in security lags infrastructure upgrades and how OPSWAT closes that gap.
Evolving Infrastructure Outpaces Security Updates.
The tempo of security updates struggles to maintain up with technological improvements. This hole is primarily obvious in file upload security. Firms are updating their infrastructure by embracing distributed, scalable apps that leverage microservices and cloud solutions—creating new avenues of attack for criminals.
Cloud Hosting
Organizations are relocating to general public cloud hosting for its scalability and efficiency. Software package as a Services (SaaS) sees growing adoption when personal cloud and on-website hosting wane. Information is distribute above many cloud storage providers. However, this increases complexity and opens supplemental attack vectors.
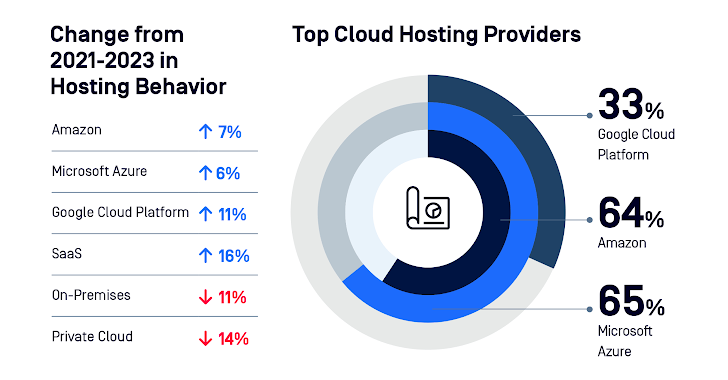 Determine 1: Breakdown of cloud hosting companies
Determine 1: Breakdown of cloud hosting companies
Corporations are Shifting to Containers
97% of corporations use containers or will deploy containers around 12 months in their web hosting environments. Azure Kubernetes, AWS Kubernetes, and Docker are leading selections. Misconfiguration and elevated updates essential for microservices open the doorway for file upload attacks leveraging vulnerable and out-of-date parts.
Unsecure File Uploads Worry
Our study highlights three principal considerations:
Information Breaches
Knowledge breaches are the #1 problem. Reputational injury, decline in company or income and regulatory fines, spherical out the listing. Cybercriminals can entry delicate knowledge, major to economic losses, regulatory fines, and reputational injury.
Compliance
General Info Defense Regulation (GDPR) prospects the way with the optimum proportion of respondents. 56% of organizations state that it was a driving factor in their security conclusions.
Malware
98% of respondents are involved about malware attacks from file uploads.
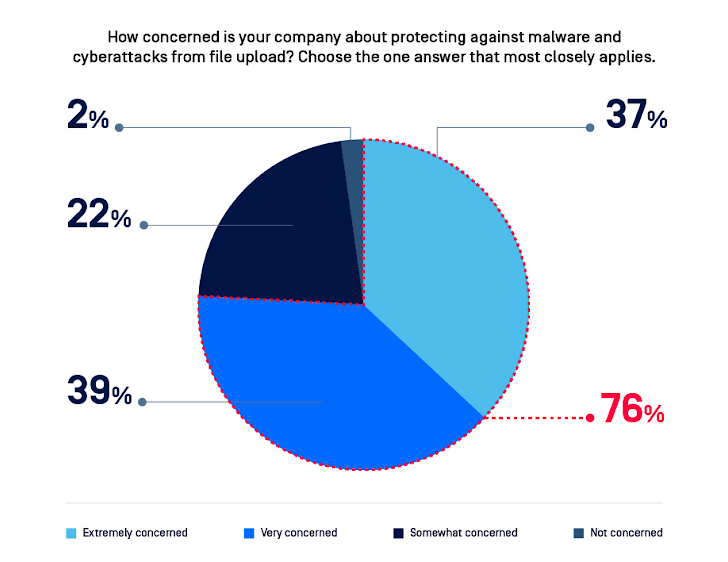 Figure 2: 3 quarters (76%) are “extremely” or “very anxious” about protecting against attacks.
Figure 2: 3 quarters (76%) are “extremely” or “very anxious” about protecting against attacks.
Simply click here to timetable a 15-moment demo of how OPSWAT can support safe your web applications from malicious file uploads.
File Upload Security Needs Correcting
As companies go on to change their operations to cloud hosting and containerized web programs, the have to have for powerful security steps has turn out to be even much more critical. This is primarily real when accepting file uploads, as cybercriminals exploit file add vulnerabilities to accessibility secure networks.
We located that:
- Only 63% use multi-engine scans for malware.
- Just 32% disarm files via Content material Disarm and Reconstruction (CDR) to tackle zero-day and embedded threats.
- Utilizing multiple anti-malware engines is essential. Scanning with around 30 engines hit a 99%+ accuracy rate.
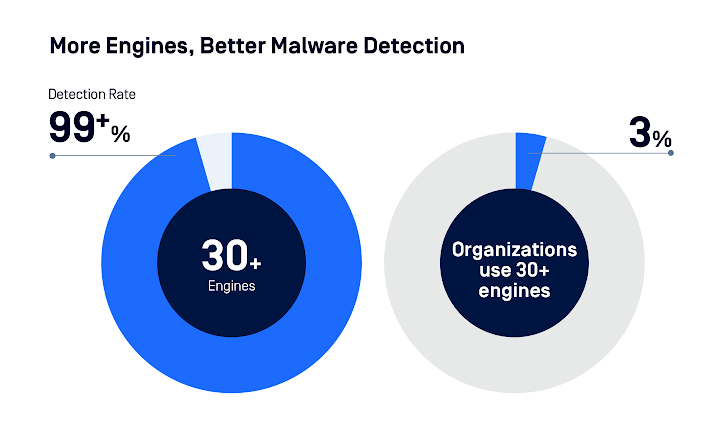 Figure 3: Anti-malware scanning efficacy.
Figure 3: Anti-malware scanning efficacy.
The Path Forward
To hold tempo with evolving infrastructure and increased attack floor, companies need to have an built-in option employing prevention- and detection-centered technologies.
Extra Antivirus Engines
Utilizing a number of antivirus (AV) engines to secure from malicious file uploads and malware can deliver extra levels of safety and boost the detection amount. Each individual antivirus motor has its have set of regulations and algorithms for detecting a extensive vary of threats.
Deep CDR Disarms Active Articles & Regenerates Harmless Documents
Our survey found that substantial businesses eliminate attainable threats from data files with Deep CDR to disarm energetic articles and regenerate harmless documents when alerting and blocking out-of-policy documents with embedded objects, these types of as JavaScript in PDFs or macros.
 Determine 4: CDR file regeneration course of action
Determine 4: CDR file regeneration course of action
One-Billion Information Details
It’s vital to continue to keep web applications vulnerability-free of charge. It really is highly recommended that corporations carry out File-Based Vulnerability Assessment technology to detect software and file-based vulnerabilities just before set up, closing any long term backdoors that hackers could exploit. We use our patented technology (U.S. 9749349 B1) to evaluate vulnerabilities collected from over a person billion facts points from in-the-wild gadgets and customers.
AI-Enabled Malware Analysis
OPSWAT Filescan performs rapidly adaptive threat examination on information to detect zero-working day malware and quickly discover Indicators of Compromise (IOCS) from many sources, like files and URLs. It takes advantage of fuzzy hashing and similarity scores powered by machine discovering to execute in-depth analysis.
Conclusion
As web application infrastructure progresses to the cloud, the attack surface area grows. OPSWAT MetaDefender is the proper route ahead to guard against malicious file uploads and information decline. You can hold pace with the evolving threat landscape by combining essential file upload security systems that seamlessly combine with your recent infrastructure.
All set to get a demo of our file upload security resolution? Reach out to just one of our security specialists currently.
Want more insights from the 2023 Web Application Security Report. Get it below.
Uncovered this post attention-grabbing? Comply with us on Twitter and LinkedIn to read through a lot more distinctive information we write-up.
Some parts of this posting are sourced from:
thehackernews.com


 Offensive and Defensive AI: Let’s Chat(GPT) About It
Offensive and Defensive AI: Let’s Chat(GPT) About It