A new variant of the GootLoader malware referred to as GootBot has been discovered to facilitate lateral movement on compromised programs and evade detection.
“The GootLoader group’s introduction of their possess personalized bot into the late stages of their attack chain is an endeavor to prevent detections when utilizing off-the-shelf equipment for C2 these as CobaltStrike or RDP,” IBM X-Power researchers Golo Mühr and Ole Villadsen stated.
“This new variant is a light-weight but powerful malware allowing attackers to speedily unfold all through the network and deploy further payloads.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
GootLoader, as the title indicates, is a malware able of downloading following-stage malware soon after luring likely victims making use of look for motor optimization (Seo) poisoning ways. It is really joined to a risk actor tracked as Hive0127 (aka UNC2565).

The use of GootBot points to a tactical change, with the implant downloaded as a payload soon after a Gootloader infection in lieu of submit-exploitation frameworks this kind of as CobaltStrike.”
Explained as an obfuscated PowerShell script, GootBot is designed to join to a compromised WordPress web site for command and control and obtain additional commands.
Complicating issues further is the use of a special hard-coded C2 server for every single deposited GootBot sample, building it tough to block malicious targeted visitors.
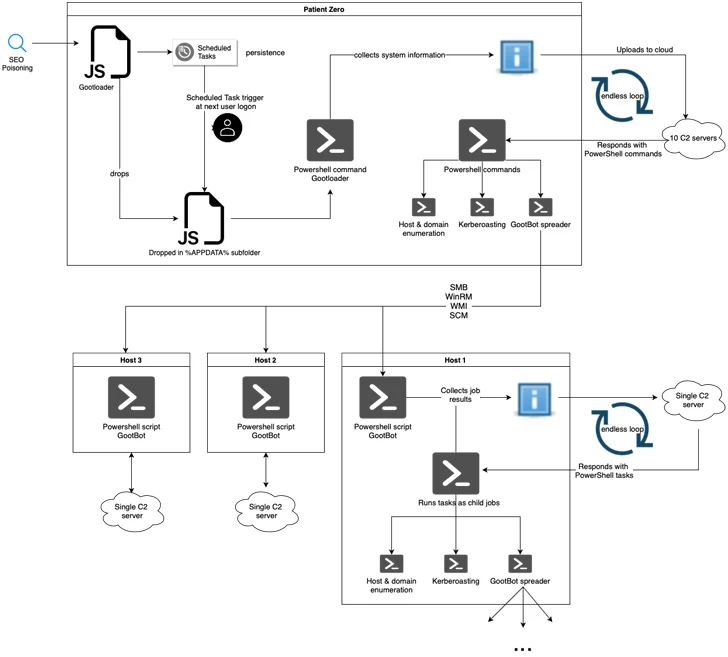
“At the moment observed campaigns leverage Search engine marketing-poisoned lookups for themes this sort of as contracts, authorized kinds, or other enterprise-similar paperwork, directing victims to compromised web pages intended to look like genuine community forums where by they are tricked into downloading the preliminary payload as an archive file,” the researchers claimed.
The archive file incorporates an obfuscated JavaScript file, which, upon execution, fetches one more JavaScript file that is triggered by using a scheduled job to reach persistence.

In the second phase, JavaScript is engineered to run a PowerShell script for gathering method information and exfiltrating it to a remote server, which, in change, responds with a PowerShell script that’s operate in an infinite loop and grants the danger actor to distribute various payloads.
This contains GootBot, which beacons out to its C2 server every single 60 seconds to fetch PowerShell tasks for execution and transmit the effects of the execution back to the server in the form of HTTP Post requests.
Some of the other capabilities of GootBot array from reconnaissance to carrying out lateral movement across the setting, proficiently increasing the scale of the attack.
“The discovery of the Gootbot variant highlights the lengths to which attackers will go to evade detection and run in stealth,” the scientists mentioned. “This change in TTPs and tooling heightens the risk of thriving put up-exploitation levels, this kind of as GootLoader-joined ransomware affiliate activity.”
Discovered this article interesting? Observe us on Twitter and LinkedIn to study much more distinctive content material we article.
Some elements of this article are sourced from:
thehackernews.com


 Confidence in File Upload Security is Alarmingly Low. Why?
Confidence in File Upload Security is Alarmingly Low. Why?