The danger actors guiding the CopperStealer malware resurfaced with two new strategies in March and April 2023 that are made to provide two novel payloads dubbed CopperStealth and CopperPhish.
Trend Micro is tracking the fiscally determined group beneath the title Water Orthrus. The adversary is also assessed to be powering a different marketing campaign identified as Scranos, which was specific by Bitdefender in 2019.
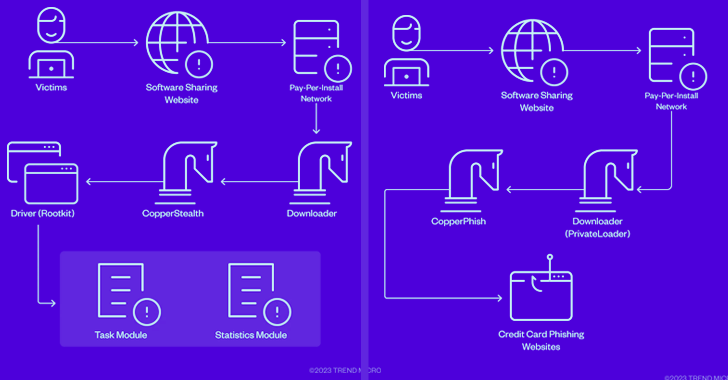
Active because at the very least 2021, Water Orthrus has a observe report of leveraging fork out-for every-put in (PPI) networks to redirect victims landing on cracked computer software down load internet sites to fall an facts stealer codenamed CopperStealer.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A different marketing campaign spotted in August 2022 entailed the use of CopperStealer to distribute Chromium-primarily based web browser extensions that are able of carrying out unauthorized transactions and transferring cryptocurrency from victims’ wallets to types underneath attackers’ manage.

The most recent attack sequences documented by Development Micro don’t mark a lot of a deviation, propagating CopperStealth by packaging it as installers for free of charge tools on Chinese computer software-sharing internet sites.
“CopperStealth’s infection chain consists of dropping and loading a rootkit, which later injects its payload into explorer.exe and a further process method,” security scientists Jaromir Horejsi and Joseph C Chen said in a specialized report.
“These payloads are responsible for downloading and running supplemental tasks. The rootkit also blocks entry to blocklisted registry keys and helps prevent selected executables and drivers from jogging.”
The driver denylist consists of byte sequences pertaining to Chinese security program firms like Huorong, Kingsoft, and Qihoo 360.
CopperStealth also incorporates a endeavor module that permits it to call out to a distant server and retrieve the command to be executed on the infected device, equipping the malware to drop much more payloads.
File Sharing Web sites Act as Conduit for CopperPhish Phishing Package
The CopperPhish campaign, detected throughout the world in April 2023, requires edge of an analogous course of action to deploy the malware by using PPI networks behind absolutely free nameless file-sharing internet websites.
“Site visitors will be redirected to a obtain webpage intended by the PPI network soon after clicking on its adverts, which pretended to be a obtain url,” the scientists explained. “The downloaded file is PrivateLoader, which downloads and operates numerous various malware.”
The downloader company, which is also available on a PPI foundation, is then employed to retrieve and start CopperPhish, a phishing package which is responsible for harvesting credit score card facts.
It achieves this by “starting a rundll32 procedure and injecting a easy application with a browser window (composed in Visible Simple) in it,” which hundreds a phishing web site urging victims to scan a QR code in purchase to verify their identity and enter a affirmation code to “restore your device’s network.”
“The window has no controls that can be utilised to reduce or shut it,” the researchers explained. “The sufferer could close the browser’s system in Task Supervisor or Course of action Explorer, but they would also need to terminate the most important payload approach, or else the browser approach will come about all over again owing to the persistence thread.”
When the sensitive facts are entered in the web page, the CopperPhish malware displays the information “the identification verification has handed” along with a confirmation code that the sufferer can enter on the aforementioned screen.
Forthcoming WEBINARLearn to Stop Ransomware with Authentic-Time Protection
Join our webinar and discover how to halt ransomware attacks in their tracks with true-time MFA and provider account defense.
Conserve My Seat!
Supplying the proper affirmation code also brings about the malware to uninstall by itself and delete all the dropped phishing data files from the device.
“The credential verification and confirmation code are two practical capabilities that make this phishing package far more effective, as the sufferer cannot just near the window or enter phony facts just to get rid of the window,” the researchers stated.
The attribution to Water Orthrus is based on the reality that both of those CopperStealth and CopperPhish share identical resource code features as that of CopperStealer, raising the probability that all a few strains might have been produced by the identical author.
The disparate aims of the strategies represent the evolution of the risk actor’s methods, indicating an endeavor to insert new abilities to its arsenal and grow its fiscal horizons.
The findings occur as malicious Google advertisements are becoming applied to entice end users into downloading bogus installers for AI instruments like Midjourney and OpenAI’s ChatGPT that finally fall stealers this kind of as Vidar and RedLine.
They also abide by the discovery of a new traffic-monetizing company termed TrafficStealer that leverages misconfigurations containers to redirect targeted traffic to sites and create faux ad clicks as portion of an illicit money-building scheme.
Found this report appealing? Observe us on Twitter and LinkedIn to go through far more unique content material we put up.
Some sections of this report are sourced from:
thehackernews.com

 Researchers Uncover New “RA Group” Ransomware
Researchers Uncover New “RA Group” Ransomware