Operational technology (OT) cybersecurity is a complicated but critical element of safeguarding organizations’ crucial systems and assets. Cybercriminals no extended break into devices, but alternatively log in – earning access security additional intricate and also a lot more important to handle and management than ever in advance of. In an effort to remedy the obtain-associated issues facing OT and critical infrastructure operators, the crew at Cyolo created a zero-have faith in entry system developed to meet the special protection, security, and uptime prerequisites of OT and industrial management techniques (ICS) environments.
Let’s appear below the hood:
The Cyolo resolution is a higher-powered blend of Zero Have faith in Network Obtain (ZTNA), Identification Service provider (IdP), and Privileged Entry Administration (PAM). What can make this technique stand out from the pack is that other ZTNA options do not supply IdP or PAM capabilities, while Id and Access Management resources (IdPs and PAMs) do not prolong connectivity. And not like other gamers in the protected distant obtain area, Cyolo does not involve a cloud link or the set up of an endpoint agent. This enables the platform to deal with some hard connectivity use circumstances that many companies struggle with.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
How the Cyolo System Is effective
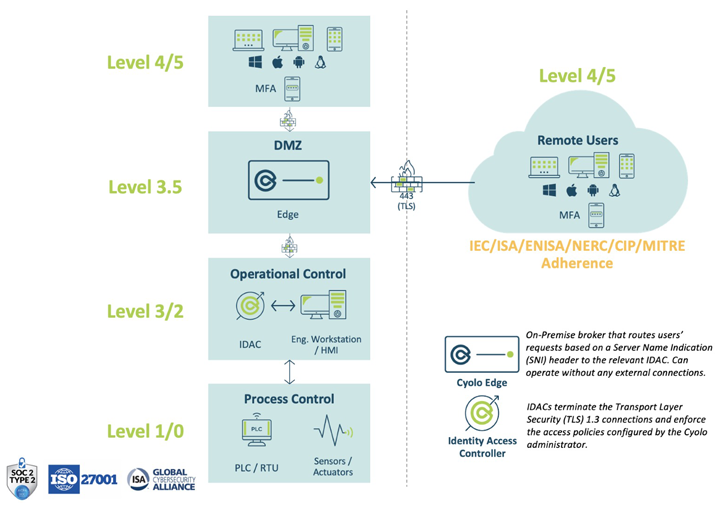 Determine 1: Architectural structure of a Cyolo deployment
Determine 1: Architectural structure of a Cyolo deployment
The main developing blocks of the Cyolo platform are Identification Access Controllers (IDACs) and Edges.
- Identity Accessibility Controller (IDAC): IDACs terminate the Transportation Layer Security (TLS) 1.3 connections and enforce the accessibility insurance policies configured by the Cyolo administrator. As a ‘reverse-proxy,’ all decryption and enforcement happen behind organizational firewalls.
- Edge Brokers: Edges are on-premises brokers that route users’ requests centered on a Server Name Indicator (SNI) header to the related IDAC. In all deployment versions, the Edge routes visitors from the users to the IDACs. Notably, Edges can operate without any exterior connections and never decrypt any site visitors, building Cyolo a unusual zero-trust entry remedy that in fact adheres to the concepts of zero rely on.
Cyolo can be deployed on-premises, in a SaaS design or, most commonly, in a hybrid model of the two. The on-premises parts can be fully isolated and non-IP related for more security, as necessary. These are the core factors desired for every deployment strategy:
- IdP Link: Identification suppliers (IdPs) guarantee the consumer searching for accessibility is who or what they claim to be across various platforms, purposes, and networks. Cyolo can combine with your current IdP, or you can use Cyolo’s community IdP that is integrated as portion of the IDAC set up. The IDAC connects straight to the IdP (not by means of the Edges).
- IDAC Outbound Conversation: IDACs always converse outbound, whether they join users’ classes coming from the Edges (on port 443) or no matter if they talk with the printed applications they serve (on their certain port).
Products Deep Dive and Differentiation
Now, let us consider a deeper seem into the Cyolo platform and see what distinguishes it from present ways to obtain security and other equipment on the current market.
At 1st look, the system has a cleanse and uncomplicated to navigate user interface. It is set up to regulate and administer the access of users to certain purposes, and it brokers this access through a set of zero-have confidence in procedures. Looking a bit additional, it logs lots of particulars about all consumer action and has a robust application programming interface (API).
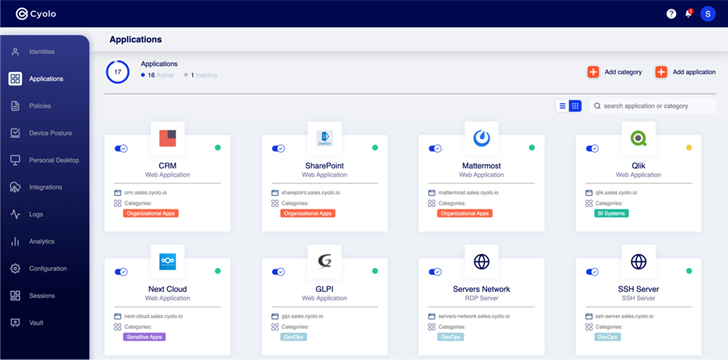 Determine 2: Main webpage on the Cyolo administrator dashboard
Determine 2: Main webpage on the Cyolo administrator dashboard
Id: The Cyolo platform can act as a standalone identity resource with users staying included through file import, Procedure for Cross-domain Identity Management (SCIM), or consumer self-enrollment. This is primarily advantageous when onboarding 3rd-party sellers and contractors who you may possibly not want to add to your company’s IdP. Each consumer can be included to unique teams, which are applied to grant accessibility to precise purposes or providers, dependent on insurance policies. The workflow to incorporate end users is quick and added authentication steps, these types of as multi-factor authentication (MFA), can be extra as a prerequisite.
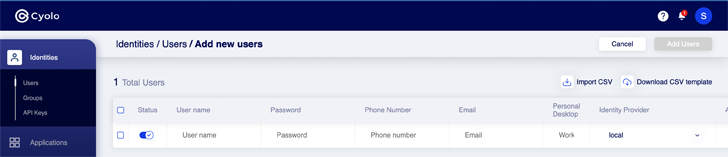 Figure 3: Adding a new user in the Cyolo dashboard
Figure 3: Adding a new user in the Cyolo dashboard
Cyolo can also perform with all typical IdPs, this kind of as Okta, Active Directory, Azure Advert, Ping, and many others. If corporations have numerous IdPs, Cyolo can federate them and allow the most proper IdP for a specific entry ask for to be applied.
Applications: Cyolo delivers connectivity to all apps dependent on valid id, and then inserts credentials on behalf of the person to enable a whole Solitary Indicator-On (SSO) experience. This simplifies the log in system for buyers and assists remove the need for generic accounts or shared passwords, which can build added risk.
Cyolo can also extend protected accessibility to legacy and custom-created apps to help MFA and SSO for these hard sources. This ability is most beneficial in the OT sector, which relies upon heavily on older devices and devices that do talk with Security Assertion Markup Language (SAML) or OpenID Connect (OIDC).
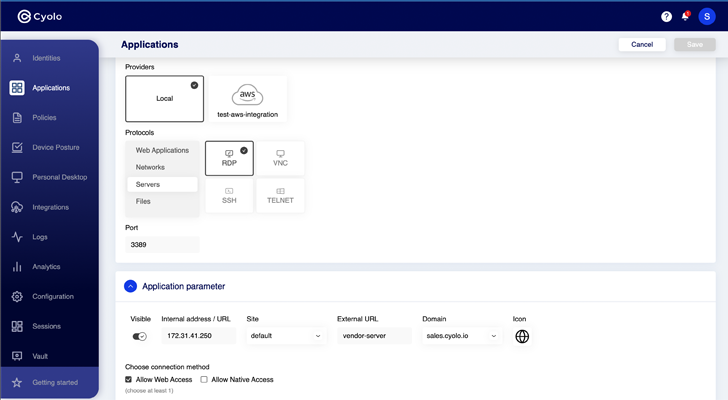 Determine 4: Configuring apps in the Cyolo platform
Determine 4: Configuring apps in the Cyolo platform
Procedures: Each individual application is configured to involve specific entry parameters that account for individual consumers and groups, along with contextual details this kind of as time of working day or spot. Two interesting features are the skill to require approval prior to obtain and the enforcement of recording for every access session.
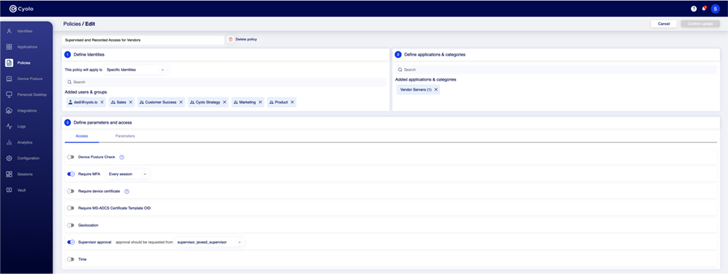 Figure 5: Configuring guidelines in between identities and purposes in the Cyolo platform
Figure 5: Configuring guidelines in between identities and purposes in the Cyolo platform
Logs: All activity on the platform is tracked in an easily exportable log. This is particularly beneficial when the Cyolo instrument is supplying SSO for an application that typically takes advantage of a generic username and password. In addition, for the reason that Cyolo features a password vault, it can securely retail outlet and rotate the shared password, with the log monitoring just which person accessed the software or assistance.
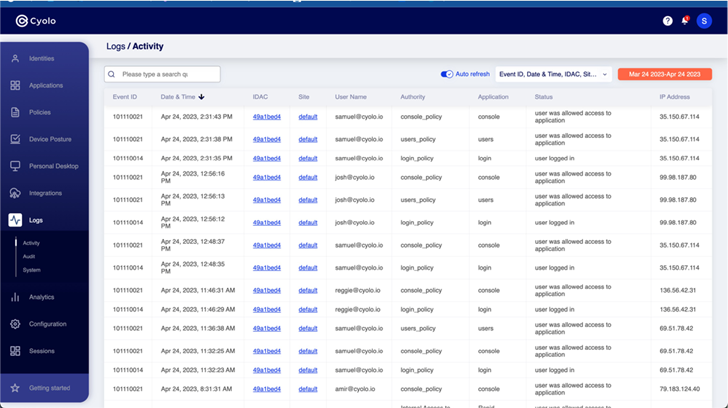 Determine 6: Action log inside of the Cyolo system
Determine 6: Action log inside of the Cyolo system
Supplemental Observations:
- Since Cyolo does not involve a cloud link to work, the solution is perfect for corporations who have to have to isolate critical segments of their network and limit entry to them. This is prevalent for OT/ICS operators who want to tightly handle distant and 3rd-party entry into these areas.
- Distant entry is often hampered because the security instrument calls for an agent to be put in on an endpoint product. Cyolo does not involve an agent to function, earning it straightforward to use for third functions, exterior contractors, or business enterprise companions.
- Their IDACs and Edge are containerized software package programs (Docker containers), so they can be loaded on to a selection of kind aspects, such as digital machines or hardened servers. This helps make deployment straightforward and rapid, as there is no have to have to interrupt traffic to install.
Conclusions
It is clear that the Cyolo workforce recognizes the value of a fantastic, straightforward consumer encounter. Just after all, any security or accessibility software should be effortless for end users if it is to have any hope of achieving optimum adoption.
When an end person logs in to the Cyolo system, they see only the equipment, resources, and apps they have to have to perform their operate. This is configured based mostly on the polices for their id and the specific application they are accessing and is enforced at the IDAC degree in just the organization’s reliable boundary. Right after the consumer selects the application they want to obtain, the Cyolo platform will control all the connectivity and credential insertion for a speedy and complete SSO expertise. The splendor of this is that the user’s workflow is not impacted (in some established-ups, the consumer may perhaps not even know they are working with the Cyolo platform at all), but the gain to security posture is substantial.
 Figure 7: Cyolo Conclusion-User Purposes Portal
Figure 7: Cyolo Conclusion-User Purposes Portal
One particular supplemental function value noting is the Cyolo platform’s administration of Distant Desktop Protocol (RDP) connections into OT environments. With Cyolo’s potential to act as an IdP, including an external (3rd-party) person was very effortless. Layering supplemental security levels, like MFA, supervisor approval, and whole audio/visible recording, were being intuitive to set up and provide a valuable history of a user’s action while linked. These capabilities show the electric power of integrating connectivity with IAM insurance policies.
This quick demo reveals facet-by-facet person and admin screens to illustrate the workflow for a Indigenous (or Web) RDP session with supervised obtain and recording.
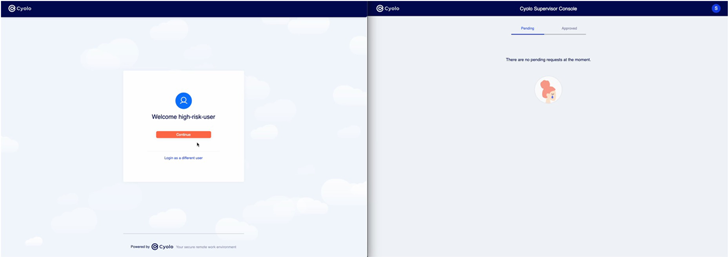 Online video 1: Swift demo of supervised access, without having an agent, to a remote desktop via RDP
Online video 1: Swift demo of supervised access, without having an agent, to a remote desktop via RDP
General, the Cyolo platform is a flexible software that can assistance clear up some of the more tricky use conditions plaguing quite a few security operators these days. By focusing on connectivity, identity validation, and accessibility administration, Cyolo provides a ton of horsepower to the table. And the most effective aspect is that they do not go away any application or support out and they focus in tough scenarios, these as seller obtain to OT environments. If you have a challenge that has been tough to clear up, it may possibly be time to give Cyolo a nearer glance.
To master far more about Cyolo, click on in this article.
Observed this short article interesting? Follow us on Twitter and LinkedIn to read through more unique articles we submit.
Some sections of this post are sourced from:
thehackernews.com


 CopperStealer Malware Crew Resurfaces with New Rootkit and Phishing Kit Modules
CopperStealer Malware Crew Resurfaces with New Rootkit and Phishing Kit Modules