Ransomware affiliates affiliated with the Qilin ransomware-as-a-company (RaaS) scheme make wherever concerning 80% to 85% of the ransom payments, in accordance to new conclusions from Group-IB.
The cybersecurity agency reported it was ready to infiltrate the team in March 2023, uncovering information about the affiliates’ payment composition and the internal workings of the RaaS system following a private dialogue with a Qilin recruiter who goes by the on the internet alias Haise.
“Several Qilin ransomware attacks are custom-made for each and every sufferer to improve their impression,” the Singapore-headquartered organization reported in a new report. “To do this, the threat actors can leverage this kind of ways as altering the filename extensions of encrypted data files and terminating distinct processes and solutions.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Qilin, also recognised as Agenda, was very first documented by Craze Micro in August 2022, beginning off a Go-based ransomware prior to switching to Rust in December 2022.
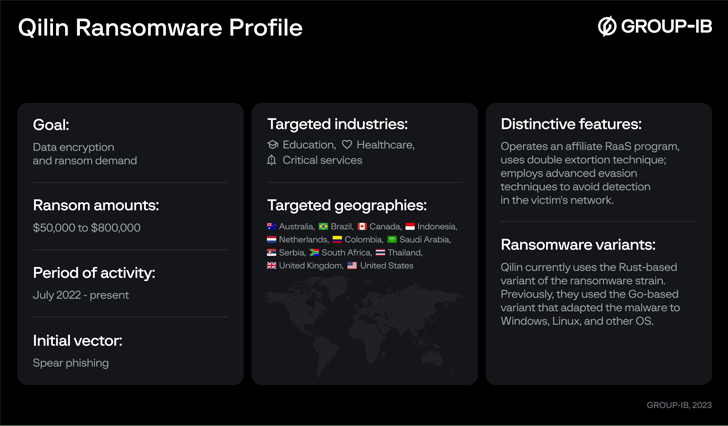
The adoption of Rust is also substantial not only since of evasion detection abilities, but also for the simple fact that it lets the threat actors to target Windows, Linux, and VMware ESXi servers.
Attacks mounted by the team make use of phishing e-mail made up of destructive backlinks as a signifies to attain initial entry and encrypt sensitive details, but not just before exfiltrating it as part of a double extortion design.

Knowledge from as quite a few as 12 various providers have been posted on Qilin’s information leak portal on the dark web concerning July 2022 and Might 2023.
The victims, which mainly span critical infrastructure, training, and health care sectors, are located in Australia, Brazil, Canada, Colombia, France, Japan, Netherlands, Serbia, the U.K., and the U.S.
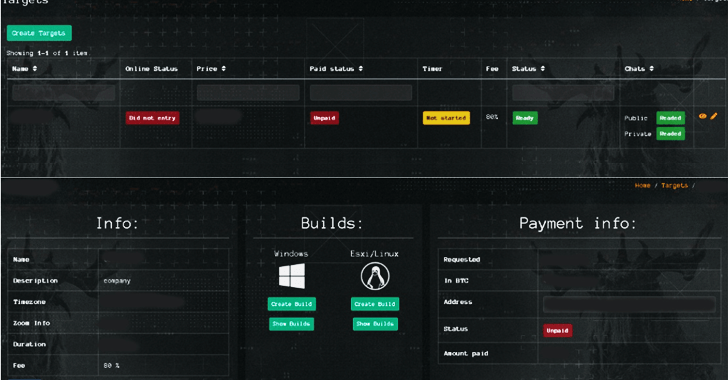
Team-IB mentioned the Qilin actors also supply affiliate marketers – who are recruited to detect targets of fascination and stage the attacks – with an administrative panel to successfully oversee different components of their operations.
“Qilin ransomware team has an affiliate panel divided into sections these types of as Targets, Weblogs, Stuffers, Information, Payments, and FAQs to deal with and coordinate its network of affiliate marketers,” security researcher Nikolay Kichatov explained.
- Targets – A segment to configure ransom notes, data files, directories, and extensions to be skipped, extensions to be encrypted, procedures to be terminated, and the method of encryption, between others
- Blogs – A segment for affiliates to create weblog posts with details about attacked corporations that have not paid out the ransom
- Stuffers – A section for the danger actors to develop accounts for other associates of the crew and deal with their privileges
- News – A part to submit updates associated to their ransomware partnerships (presently blank)
- Payments – A portion that is made up of transaction aspects, affiliate wallet balances, and choices to withdraw illicit proceeds
- FAQs – A segment showcasing aid and documentation information and facts that information the methods to use the ransomware
“Though Qilin ransomware received notoriety for targeting critical sector providers, they are a risk to corporations throughout all verticals,” Kichatov said.
“What’s more, the ransomware operator’s affiliate software is not only introducing new users to its network, but it is weaponizing them with upgraded resources, approaches, and even support delivery.”
Discovered this write-up attention-grabbing? Observe us on Twitter and LinkedIn to browse a lot more unique content material we write-up.
Some sections of this write-up are sourced from:
thehackernews.com

 Cyolo Product Overview: Secure Remote Access to All Environments
Cyolo Product Overview: Secure Remote Access to All Environments