Two security vulnerabilities have been found in F5 Following Central Supervisor that could be exploited by a risk actor to seize handle of the equipment and produce hidden rogue administrator accounts for persistence.
The remotely exploitable flaws “can give attackers full administrative management of the system, and subsequently allow attackers to produce accounts on any F5 assets managed by the Up coming Central Manager,” security organization Eclypsium stated in a new report.
A description of the two issues is as follows –

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
- CVE-2024-21793 (CVSS rating: 7.5) – An OData injection vulnerability that could allow an unauthenticated attacker to execute destructive SQL statements as a result of the Large-IP Future Central Manager API
- CVE-2024-26026 (CVSS score: 7.5) – An SQL injection vulnerability that could let an unauthenticated attacker to execute malicious SQL statements as a result of the Huge-IP Upcoming Central Manager API
Both equally the flaws influence Following Central Supervisor variations from 20..1 to 20.1.. The shortcomings have been tackled in model 20.2..

Productive exploitation of the bugs can outcome in entire administrative control of the system, enabling attackers to incorporate it with other flaws to make new accounts on any Significant-IP Up coming asset managed by the Central Manager.
What’s additional, these destructive accounts would continue being concealed from the Central Manager by itself. This is made doable by a server-aspect request forgery (SSRF) vulnerability that can make it achievable to invoke an undocumented API and build the accounts.
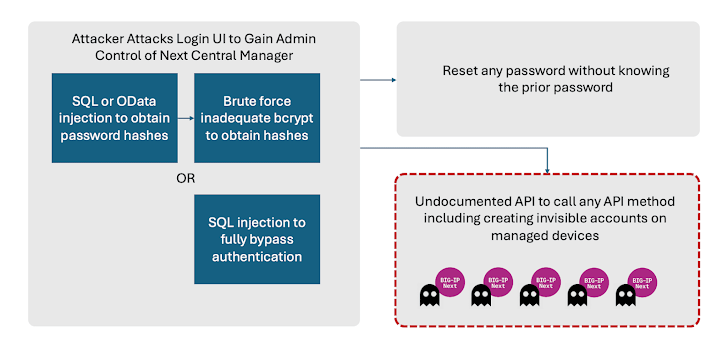
“This implies that even if the admin password is reset in the Central Manager, and the technique is patched, attacker accessibility may well even now keep on being,” the supply chain security firm stated.
Also identified by Eclypsium are two more weaknesses that could just brute-force attacks from the admin passwords and permit an administrator to reset their passwords devoid of information of the prior one particular. An attacker could weaponize this issue to block legitimate accessibility to the product from every account.
When there are no indications that the vulnerabilities have come under active exploitation in the wild, it is really recommended that consumers update their scenarios to the most current variation to mitigate potential threats.
“Networking and software infrastructure have come to be a critical focus on of attackers in new several years,” Eclypsium stated. “Exploiting these highly privileged systems can give adversaries an ideal way to achieve entry, unfold, and manage persistence within an surroundings.”
Identified this write-up intriguing? Adhere to us on Twitter and LinkedIn to browse far more exclusive content material we article.
Some elements of this post are sourced from:
thehackernews.com

 A SaaS Security Challenge: Getting Permissions All in One Place
A SaaS Security Challenge: Getting Permissions All in One Place 