Security researchers at Microsoft have found a flaw in Apple’s macOS that can hackers could use to bypass the Process Integrity Protection (SIP) feature and execute arbitrary code.
Dubbed Shrootless, the flaw has been discovered as CVE-2021-30892 and was provided in the security updates released by Apple on 26 October.
The flaw lies in how Apple symptoms the software package and how the publish-installation scripts are installed in it. The scientists identified that attackers can use this mechanism for destructive uses by developing a customized bundle that can intercept the set up system. Following SIP bypass, an attacker can put in rootkits and undetectable malware, and even overwrite technique information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A structure flaw suggests that in some situations application packages have to have access to directories guarded by SIP, as is the case with program updates. Data files with the extended attribute ‘com.apple.rootless’ are likewise SIP-secured. Of program, there’s no way to include that extended attribute to a file legitimately, or else malware could use SIP for its possess defense.
While examining macOS procedures to bypass SIP, scientists came throughout the ‘system_installd’ daemon with strong ‘com.apple.rootless.put in.inheritable’ rights. With these legal rights, any ‘system_installd’ kid system can steer clear of all SIP-established file procedure constraints.
The researchers made a decision to look at all the child procedures of ‘system_installd’ and had been astonished to find several situations that let hackers to abuse this operation to bypass SIP.
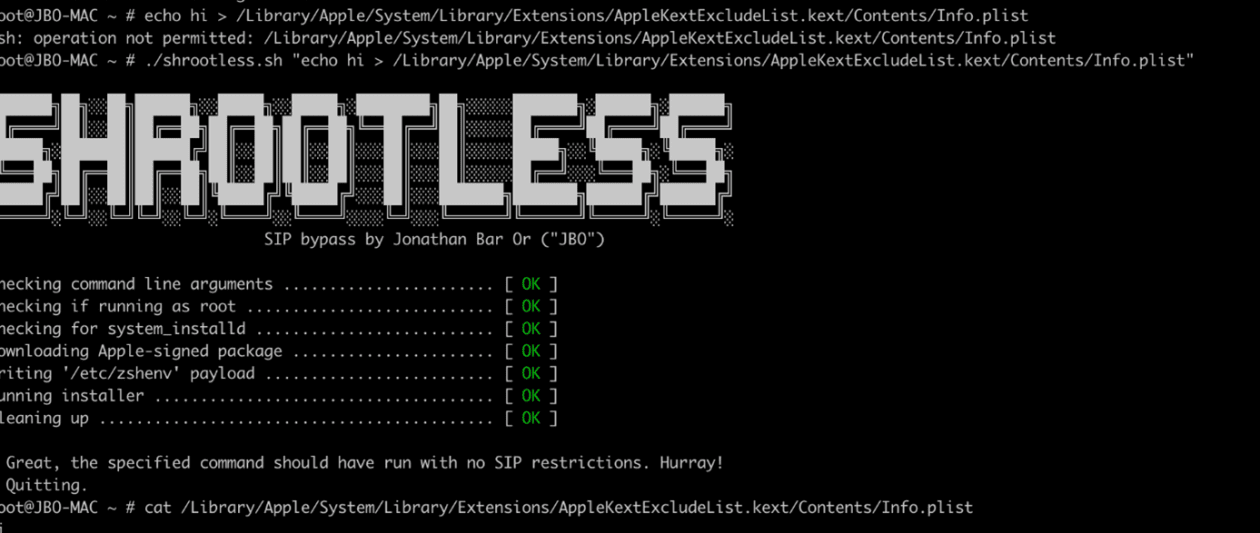
For case in point, if an Apple-signed deal (.pkg file) is mounted, the deal will start off the ‘system_installd’ approach, which is dependable for putting in it. If the deal incorporates any write-up-set up scripts, ‘system_installd’ starts them by initiating the default shell (on macOS, this is zsh).
It can be vital to take note that just after setting up zsh, it then seems for the ‘/and so on/zshenv’ file and, if discovered, automatically runs commands from it, even in a non-interactive mode. Hence, to conduct arbitrary operations on the device, attackers can produce a malicious ‘/and so on/zshenv’ file and then wait around for ‘system_installd’ to invoke zsh.
Scientists mentioned that the exploration underscores the relevance of collaboration among the security scientists, software suppliers, and the larger sized security neighborhood.
“As cross-system threats go on to maximize, vulnerability discoveries, coordinated reaction, and other kinds of risk intelligence sharing enable enrich our defense technologies that safe users’ computing practical experience irrespective of the platform or product they’re using,” stated Jonathan Bar Or, senior security researcher at Microsoft’s 365 Defender Investigation Staff.
Some components of this short article are sourced from:
www.itpro.co.uk

 New ‘Shrootless’ Bug Could Let Attackers Install Rootkit on macOS Systems
New ‘Shrootless’ Bug Could Let Attackers Install Rootkit on macOS Systems