Cybersecurity researchers have disclosed a security flaw in the Linux Kernel’s Clear Inter Process Conversation (TIPC) module that could probably be leveraged equally regionally as effectively as remotely to execute arbitrary code inside the kernel and consider command of vulnerable equipment.
The heap overflow vulnerability “can be exploited locally or remotely in a network to acquire kernel privileges, and would allow for an attacker to compromise the overall method,” cybersecurity agency SentinelOne reported in a report revealed currently and shared with The Hacker Information.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
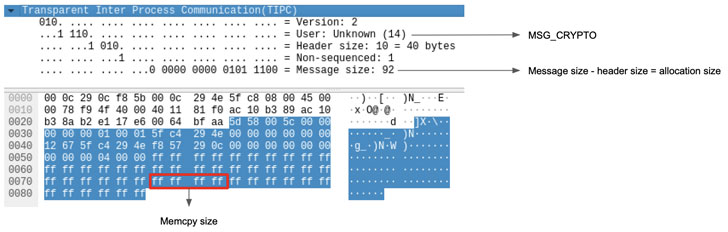
TIPC is a transportation layer protocol intended for nodes operating in dynamic cluster environments to reliably converse with each individual other in a way that is much more successful and fault-tolerant than other protocols this kind of as TCP. The vulnerability recognized by SentinelOne has to do with a new concept form named “MSG_CRYPTO” that was released in September 2020 and enables peer nodes in the cluster to deliver cryptographic keys.
Though the protocol has checks in spot to validate these types of messages after decryption to be certain that a packet’s genuine payload dimensions isn’t going to exceed that of the highest user information dimensions and that the latter is higher than the concept header size, no restrictions have been located to be placed on the length of the crucial (aka ‘keylen’) by itself, ensuing in a circumstance where by “an attacker can create a packet with a modest human body measurement to allocate heap memory, and then use an arbitrary size in the ‘keylen’ attribute to produce outside the bounds of this site.”
There is no proof that the flaw has been abused in authentic-planet attacks to day, and pursuing liable disclosure on October 19, the issue has been resolved in Linux Kernel version 5.15 produced on October 31, 2021.

“The functionality tipc_crypto_important_rcv is utilised to parse MSG_CRYPTO messages to obtain keys from other nodes in the cluster in buy to decrypt any further messages from them,” Linux kernel maintainers reported in a take care of pushed late previous thirty day period. “This patch verifies that any equipped sizes in the information entire body are legitimate for the been given information.”
“Although TIPC by itself isn’t loaded instantly by the technique but by conclude customers, the ability to configure it from an unprivileged area viewpoint and the probability of distant exploitation makes this a perilous vulnerability for individuals that use it in their networks,” SentinelOne researcher Max Van Amerongen stated.
Identified this posting interesting? Adhere to THN on Fb, Twitter and LinkedIn to examine a lot more distinctive written content we write-up.
Some pieces of this write-up are sourced from:
thehackernews.com


 Our journey to API security at Raiffeisen Bank International
Our journey to API security at Raiffeisen Bank International