CODESYS has produced patches to deal with as several as 11 security flaws that, if successfully exploited, could outcome in information and facts disclosure and a denial-of-provider (DoS) ailment, among the many others.
“These vulnerabilities are very simple to exploit, and they can be properly exploited to bring about implications this kind of as sensitive info leakage, PLCs getting into a critical fault state, and arbitrary code execution,” Chinese cybersecurity business NSFOCUS mentioned. “In mixture with industrial situations on the area, these vulnerabilities could expose industrial manufacturing to stagnation, machines injury, and so forth.”
CODESYS is a application suite applied by automation specialists as a growth natural environment for programmable logic controller programs (PLCs).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
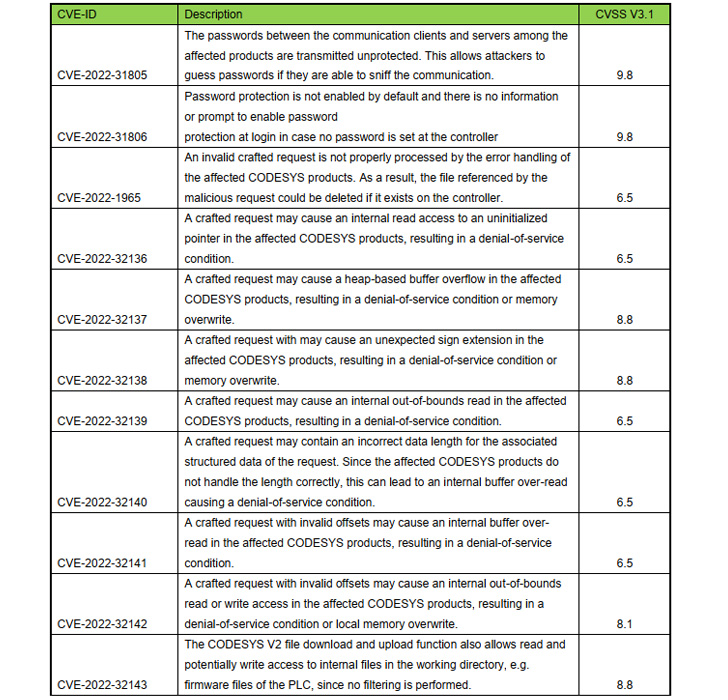
Adhering to liable disclosure between September 2021 and January 2022, fixes were transported by the German program corporation very last 7 days on June 23, 2022. Two of the bugs are rated as Critical, 7 as Significant, and two as Medium in severity. The issues collectively impact the pursuing products and solutions –
- CODESYS Improvement Method prior to variation V2.3.9.69
- CODESYS Gateway Shopper prior to model V2.3.9.38
- CODESYS Gateway Server prior to version V2.3.9.38
- CODESYS Web server prior to edition V1.1.9.23
- CODESYS SP Realtime NT prior to edition V2.3.7.30
- CODESYS PLCWinNT prior to edition V2.4.7.57, and
- CODESYS Runtime Toolkit 32 bit comprehensive prior to model V2.4.7.57
Chief among the flaws are CVE-2022-31805 and CVE-2022-31806 (CVSS scores: 9.8), which relate to the cleartext use of passwords utilised to authenticate right before carrying out operations on the PLCs and a failure to empower password security by default in the CODESYS Management runtime system respectively.
Exploiting the weaknesses could not only enable a malicious actor to seize handle of the concentrate on PLC machine, but also download a rogue task to a PLC and execute arbitrary code.

A the greater part of the other vulnerabilities (from CVE-2022-32136 to CVE-2022-32142) could be weaponized by a beforehand authenticated attacker on the controller to guide to a denial-of-services situation.
In a separate advisory revealed on June 23, CODESYS stated it also remediated a few other flaws in CODESYS Gateway Server (CVE-2022-31802, CVE-2022-31803, and CVE-2022-31804) that could be leveraged to send crafted requests to bypass authentication and crash the server.
Moreover implementing patches in a well timed style, it is encouraged to “find the impacted items driving the security protection equipment and accomplish a defense-in-depth method for network security.”
Observed this report attention-grabbing? Observe THN on Facebook, Twitter and LinkedIn to read additional distinctive content material we submit.
Some sections of this post are sourced from:
thehackernews.com

 What Are Shadow IDs, and How Are They Crucial in 2022?
What Are Shadow IDs, and How Are They Crucial in 2022?