Just right before final Xmas, in a initially-of-a-sort case, JPMorgan was fined $200M for workforce employing non-sanctioned purposes for speaking about money method. No mention of insider investing, naked shorting, or any malevolence. Just workers circumventing regulation making use of, effectively, Shadow IT. Not for the reason that they experimented with to obfuscate or disguise nearly anything, simply due to the fact it was a convenient instrument that they most popular in excess of any other sanctioned products (which JPMorgan undoubtedly has pretty a number of of.)
Visibility into unfamiliar and unsanctioned apps has been essential by regulators and also recommended by the Centre for Internet Security community for a very long time. But it seems like new and improved ways are even now in desire. Gartner has discovered External Attack Area Administration, Digital Supply Chain Risk, and Identity Danger Detection as the prime 3 trends to focus on in 2022, all of which are carefully intertwined with Shadow IT.
“Shadow IDs,” or in other phrases, unmanaged worker identities and accounts in 3rd-party services are typically designed working with a simple email-and-password-based registration. CASBs and company SSO remedies are restricted to a few sanctioned apps and are not extensively adopted on most sites and services possibly. This usually means, that a huge section of an organization’s external surface –as very well as its user identities– could be entirely invisible.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Higher than all, these Shadow IDs stay unmanaged even right after workers leave the organization. This might consequence in unauthorized entry to sensitive consumer facts or other cloud-primarily based solutions. Staff-established, but company-linked identities are unseen for most IDM/IAM tools also. The graveyard of overlooked accounts belonging to ex-workers or deserted purposes is developing just about every working day, to infinity.
And often, the dead increase from their graves, as with the Joint Commission On General public Ethics, whose legacy system was breached this 12 months, even although it is been out of use given that 2015. They rightfully notified their legacy end users because they understand that password reuse may perhaps extend over numerous several years, and in accordance to Verizon, stolen qualifications are still the major contributor to all kinds of breaches and attacks. So when Shadow IDs are left guiding, they produce an everlasting risk unseen and unmanaged by everyone.
How to Report on Shadow IT and Shadow IDs?
Unfortunately, network monitoring misses the mark, as those people tools are created to filter destructive targeted visitors, present knowledge leakage protection and develop group-centered policies for browsing. Nevertheless, they are absolutely blind to true logins, and thus are unable to differentiate browsing, private accounts, and corporate application signups, (or phishing web-sites for that make a difference). To discover and manage Shadow IDs and Shadow IT, there requirements to be software and account-level checking in position, that can develop a trusted, international source of truth of the matter across the business.
Discovering these property by means of monitoring small business-linked credential utilization on any website allows a unified look at of unsanctioned or undesirable programs. Inventories of applications and accounts give visibility of the accurate scope of exterior companies and identities made use of throughout the corporation. Also, they let the examining of 3rd-party providers about their guidelines, security and authentication steps, and how they are handling and retaining your info.
It is not possible to appropriately categorize all of the quarter-million new domains that are registered every day throughout the globe, so checking those that clearly show up on our endpoints is the correct tactic. As a facet-influence, revealing logins on suspicious or new applications will give visibility into effective phishing attacks that ended up not prevented on a gateway or customer-aspect, and wherever workforce gave absent critical qualifications.
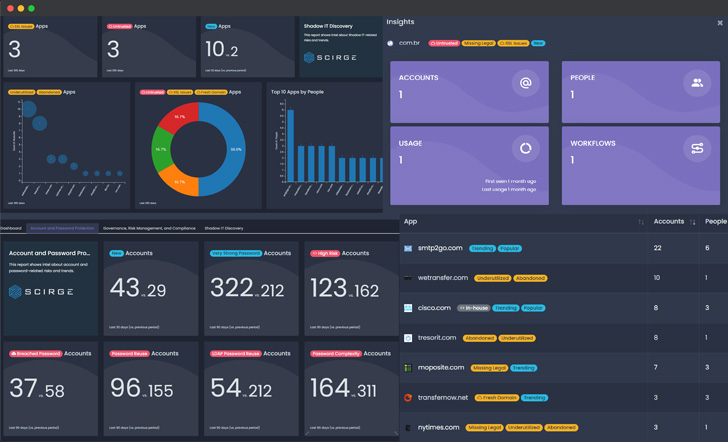
Scirge is a browser-centered instrument that presents comprehensive visibility into Shadow IDs and Shadow IT, password cleanliness for corporate and 3rd-party company web accounts, and even genuine-time personnel education and learning and awareness. And it also has a wholly free of charge variation for auditing your cloud footprint, so you can get an instant check out of the extent of Shadow IT amongst your employees.
Observed this article intriguing? Follow THN on Facebook, Twitter and LinkedIn to study far more unique written content we article.
Some components of this write-up are sourced from:
thehackernews.com


 Italy Data Protection Authority Warns Websites Against Use of Google Analytics
Italy Data Protection Authority Warns Websites Against Use of Google Analytics