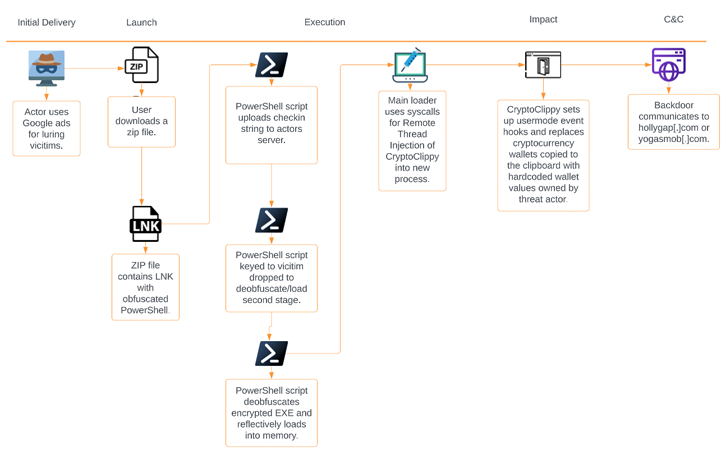
Portuguese consumers are remaining targeted by a new malware codenamed CryptoClippy that is able of stealing cryptocurrency as portion of a malvertising campaign.
The exercise leverages Search engine optimisation poisoning approaches to entice customers hunting for “WhatsApp web” to rogue domains hosting the malware, Palo Alto Networks Unit 42 reported in a new report posted currently.
CryptoClippy, a C-dependent executable, is a sort of cryware identified as clipper malware that screens a victim’s clipboard for written content matching cryptocurrency addresses and substituting them with a wallet tackle underneath the danger actor’s management.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The clipper malware takes advantage of common expressions (regexes) to discover what sort of cryptocurrency the handle pertains to,” Unit 42 scientists claimed.
“It then replaces the clipboard entry with a visually similar but adversary-controlled wallet address for the acceptable cryptocurrency. Later, when the victim pastes the tackle from the clipboard to carry out a transaction, they actually are sending cryptocurrency immediately to the danger actor.”
The illicit plan is approximated to have netted its operators about $983 so much, with victims identified throughout producing, IT providers, and actual estate industries.
It’s worth noting that the use of poisoned lookup results to provide malware has been adopted by threat actors affiliated with the GootLoader malware.
Forthcoming WEBINARLearn to Secure the Identity Perimeter – Established Procedures
Improve your enterprise security with our impending professional-led cybersecurity webinar: Examine Id Perimeter techniques!
Will not Miss Out – Save Your Seat!
An additional method applied to determine suited targets is a website traffic direction process (TDS), which checks if the desired browser language is Portuguese, and if so, requires the consumer to a rogue landing webpage.
Consumers who do not meet the requisite criteria are redirected to the genuine WhatsApp Web area with no any even further malicious activity, thereby averting detection.
The results get there times right after SecurityScorecard detailed an details stealer referred to as Lumma that’s able of harvesting knowledge from web browsers, cryptocurrency wallets, and a variety of applications this kind of as AnyDesk, FileZilla, KeePass, Steam, and Telegram.
Observed this post fascinating? Abide by us on Twitter and LinkedIn to examine additional special content material we submit.
Some elements of this report are sourced from:
thehackernews.com

 UK Discloses Offensive Cyber Capabilities Principles
UK Discloses Offensive Cyber Capabilities Principles