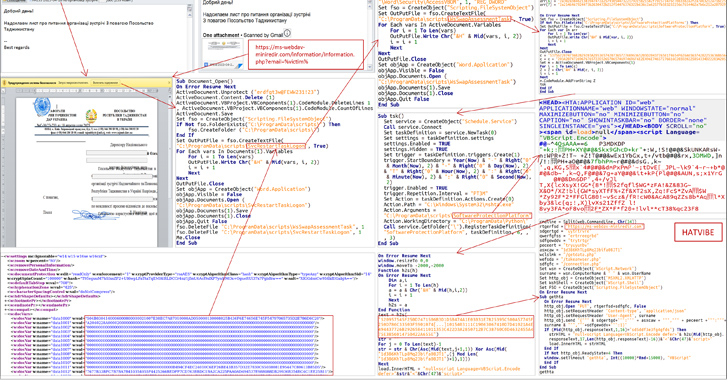
The Pc Emergency Reaction Team of Ukraine (CERT-UA) has warned of cyber attacks targeting condition bodies in the region as portion of an espionage campaign.
The intrusion set, attributed to a threat actor tracked by the authority as UAC-0063 because 2021, leverages phishing lures to deploy a wide variety of malicious tools on infected devices. The origins of the hacking crew are presently mysterious.
In the attack chain explained by the agency, the emails focused an unspecified ministry and purported to be from the Embassy of Tajikistan in Ukraine. It’s suspected that the messages were being despatched from a previously compromised mailbox.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The emails arrive connected with a Microsoft Term doc that, on enabling macros, launches an encoded VBScript known as HATVIBE, which is then utilised to drop additional malware.
This features a keylogger (LOGPIE), a Python-based backdoor able of working commands despatched from a remote server (CHERRYSPY), and a instrument targeted on exfiltrating data files with specific extensions (STILLARCH or DownEx).
It’s worthy of noting that DownEx was just lately documented by Bitdefender as becoming utilized by an unfamiliar actor in highly focused attacks aimed at governing administration entities in Kazakhstan and Afghanistan.
“Extra analyze of the infrastructure and associated data files manufactured it achievable to conclude that amid the objects of interest of the team are corporations from Mongolia, Kazakhstan, Kyrgyzstan, Israel, [and] India,” CERT-UA claimed.
The results present that some menace actors are nevertheless utilizing macro-based malware despite Microsoft disabling the element by default in Workplace files downloaded from the web.
That said, Microsoft’s limits have led quite a few attack groups to experiment and adapt their attack chains and payload delivery mechanisms to involve uncommon file sorts (CHM, ISO, LNK, VHD, XLL, and WSF) and strategies like HTML smuggling.
Approaching WEBINARZero Rely on + Deception: Understand How to Outsmart Attackers!
Find how Deception can detect state-of-the-art threats, cease lateral movement, and increase your Zero Trust tactic. Join our insightful webinar!
Conserve My Seat!
Organization security firm Proofpoint claimed it noticed various initial obtain brokers (IABs) – actors who infiltrate big targets and then market that access to other cybercriminals for profit – using PDF and OneNote files starting up in December 2022.
“The experimentation with and normal pivoting to new payload shipping and delivery strategies by tracked risk actors, primarily IABs, is vastly distinctive from attack chains observed prior to 2022 and heralds a new ordinary of threat action,” the corporation stated.
“No lengthier are the most skilled cybercriminal actors relying on one particular or a couple tactics, but somewhat are regularly developing and iterating new TTPs. The rapid level of adjust for lots of threat actors suggests they have the time, capability, and knowledge of the risk landscape to rapidly acquire and execute new strategies.”
Located this article intriguing? Observe us on Twitter and LinkedIn to examine far more unique material we put up.
Some pieces of this article are sourced from:
thehackernews.com

 Google Unveils Bug Bounty Program For Android Apps
Google Unveils Bug Bounty Program For Android Apps