The infamous Lazarus Group actor has been focusing on vulnerable variations of Microsoft Internet Data Companies (IIS) servers as an initial breach route to deploy malware on qualified systems.
The results come from the AhnLab Security Crisis response Heart (ASEC), which thorough the highly developed persistent threat’s (APT) continued abuse of DLL side-loading methods to deploy malware.
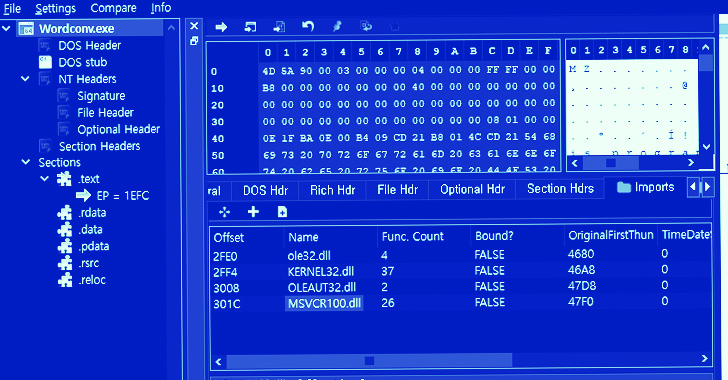
“The risk actor destinations a destructive DLL (msvcr100.dll) in the identical folder route as a ordinary software (Wordconv.exe) by using the Windows IIS web server approach, w3wp.exe,” ASEC explained. “They then execute the normal software to initiate the execution of the destructive DLL.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
DLL side-loading, very similar to DLL search-order hijacking, refers to the proxy execution of a rogue DLL by means of a benign binary planted in the same listing.
Lazarus, a really-capable and relentless country-condition group connected to North Korea, was most just lately spotted leveraging the exact system in relationship with the cascading provide chain attack on enterprise communications assistance provider 3CX.
The destructive msvcr100.dll library, for its aspect, is designed to decrypt an encoded payload that’s then executed in memory. The malware is stated to be a variant of a comparable artifact that was uncovered by ASEC final year and which acted as a backdoor to converse with an actor-managed server.
The attack chain even more entailed the exploitation of a discontinued open supply Notepad++ plugin referred to as Brief Shade Picker to deliver additional malware in get to aid credential theft and lateral movement.
The latest enhancement demonstrates the variety of Lazarus attacks and its means to make use of an comprehensive established of applications against victims to carry out long-term espionage operations.
“In unique, given that the danger group mainly makes use of the DLL facet-loading system throughout their original infiltrations, providers really should proactively keep an eye on abnormal process execution relationships and consider preemptive measures to reduce the threat team from carrying out things to do such as facts exfiltration and lateral movement,” ASEC claimed.
U.S. Treasury Sanctions North Korean Entities
The findings also appear as the U.S. Treasury Office sanctioned 4 entities and a single personal concerned in destructive cyber pursuits and fundraising strategies that purpose to help North Korea’s strategic priorities.
Upcoming WEBINARZero Have faith in + Deception: Find out How to Outsmart Attackers!
Discover how Deception can detect highly developed threats, stop lateral motion, and greatly enhance your Zero Rely on technique. Join our insightful webinar!
Save My Seat!
This incorporates the Pyongyang University of Automation, the Complex Reconnaissance Bureau and its subordinate cyber device, the 110th Research Heart, Chinyong Facts Technology Cooperation Business, and a North Korean national named Kim Sang Person.
The Lazarus Group and its a variety of clusters are believed to be operated by the Complex Reconnaissance Bureau, which oversees North Korea’s development of offensive cyber techniques and equipment.
The sanctions-hit country, moreover engaging in crypto currency theft and espionage operations, is known to create illicit revenue from a workforce of experienced IT personnel who pose beneath fictitious identities to obtain positions in the technology and digital currency sectors across the earth.
“The DPRK conducts malicious cyber routines and deploys details technology (IT) employees who fraudulently get hold of work to generate earnings, together with in virtual forex, to help the Kim routine and its priorities, this kind of as its unlawful weapons of mass destruction and ballistic missile programs,” the department claimed.
“These workers intentionally obfuscate their identities, destinations, and nationalities, usually utilizing phony personas, proxy accounts, stolen identities, and falsified or forged documentation to use for careers at these companies.”
“They gain hundreds of thousands and thousands of bucks a year by participating in a extensive assortment of IT development operate, such as freelance get the job done platforms (internet sites/purposes) and cryptocurrency enhancement, right after acquiring freelance work contracts from providers all over the entire world,” the South Korean authorities warned in December 2022.
Found this short article fascinating? Abide by us on Twitter and LinkedIn to examine a lot more unique content material we write-up.
Some pieces of this article are sourced from:
thehackernews.com

 Cyber Attacks Strike Ukraine’s State Bodies in Espionage Operation
Cyber Attacks Strike Ukraine’s State Bodies in Espionage Operation