The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor termed WhiskerSpy as portion of a social engineering marketing campaign.
Earth Kitsune, active given that at minimum 2019, is recognised to largely goal people today interested in North Korea with self-formulated malware such as dneSpy and agfSpy. Beforehand documented intrusions have entailed the use of watering holes that leverage browser exploits in Google Chrome and Internet Explorer to activate the infection chain.
The differentiating factor in the hottest attacks is a shift to social engineering to trick people into checking out compromised web sites linked to North Korea, according to a new report from Pattern Micro introduced final 7 days.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
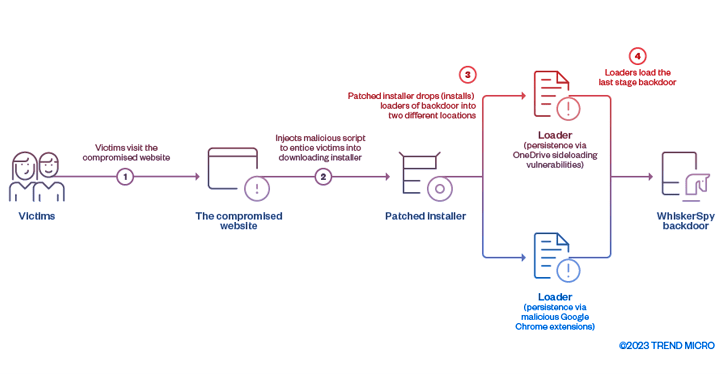
The cybersecurity firm said the web page of an unnamed pro-North Korean business was hacked and modified to distribute the WhiskerSpy implant. The compromise was uncovered at the conclude of final 12 months.
“When a qualified visitor tries to observe videos on the internet site, a destructive script injected by the attacker shows a concept prompt notifying the victims with a online video codec error to entice them to download and put in a trojanized codec installer,” researchers Joseph C Chen and Jaromir Horejsi claimed.
The booby-trapped script is mentioned to have been injected into the website’s video clip internet pages, with the installer (“Codec-AVC1.msi”) subsequently used to load WhiskerSpy.
But the attack also reveals some clever tips in an try to sidestep detection. This includes providing the destructive script only to all those site visitors whose IP addresses match distinct standards –
- An IP handle subnet positioned in Shenyang, China
- A particular IP handle situated in Nagoya, Japan, and
- An IP address subnet found in Brazil
Craze Micro observed that the specific IP addresses in Brazil belong to a commercial VPN company and that the danger actor could have “employed this VPN services to test the deployment of their watering hole attacks.”
Persistence is reached by both abusing a Dynamic Library Connection (DLL) hijacking vulnerability in OneDrive or by way of a malicious Google Chrome extension that employs indigenous messaging APIs to execute the payload every time the web browser is launched.
The WhiskerSpy backdoor, like other malware of its type, arrives with abilities to delete, enumerate, down load and add data files, consider screenshots, inject shellcode, load arbitrary executables.
“Earth Kitsune are proficient with their technological abilities and are continuously evolving their applications, tactics, and processes,” the researchers mentioned.
Earth Yako Strikes Educational and Investigate Sectors in Japan
Earth Kitsune is not the only risk actor to go following Japanese targets, for the cybersecurity enterprise also comprehensive an additional intrusion established codenamed Earth Yako placing research companies and believe tanks in the place.
The action, noticed as a short while ago as January 2023, is a continuation of a formerly acknowledged marketing campaign referred to as Operation RestyLink. A subset of the attacks also targeted entities found in Taiwan.
“The intrusion set released new instruments and malware in just a shorter interval of time, routinely changing and growing its attack targets,” Pattern Micro explained, pointing out Earth Yako’s modus operandi of “actively shifting their targets and techniques.”
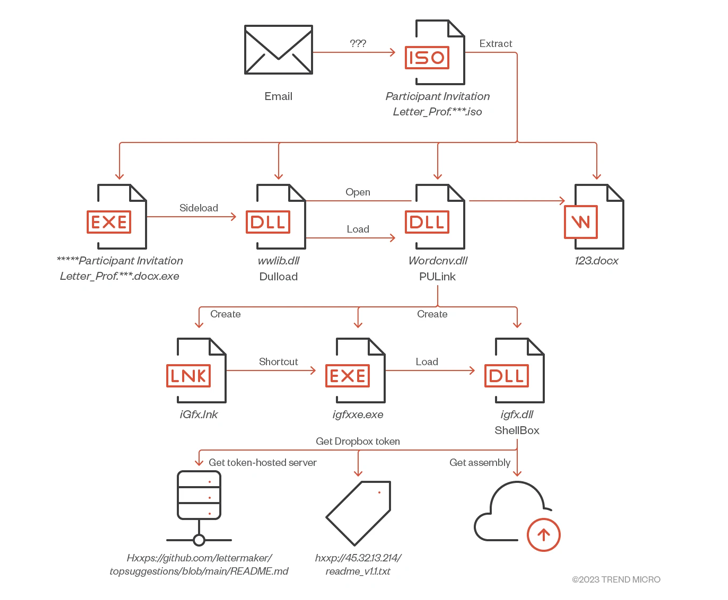
The beginning position is a spear-phishing email that masquerades as invitations to general public functions. The messages include a malicious URL that factors to a payload, which, in turn, is responsible for downloading the malware on to the method.
The attacks are also characterized by a trove of custom made tools comprising droppers (PULink), loaders (Dulload, MirrorKey), stagers (ShellBox), and backdoors (PlugBox, TransBox).
PlugBox, ShellBox, and TransBox, as the names imply, choose benefit of Dropbox APIs to retrieve up coming-phase malware from a distant server difficult-coded in a GitHub repository, acquire commands, and harvest and exfiltrate facts.
The exact origins of Earth Yako continue being unknown, but Craze Micro said it discovered partial technological overlaps between the group and other danger actors like Darkhotel, APT10 (aka Stone Panda), and APT29 (aka Cozy Bear or Nobelium).
“A person of the features of the the latest qualified attacks is that they shifted to concentrating on the folks viewed as to have somewhat weak security actions as opposed to corporations and other companies,” the company mentioned.
“This shift to targeting folks more than enterprises is highlighted by the concentrating on and abuse of Dropbox as it is deemed a well-known company in the location amid customers for personalized use, but not for corporations.”
Uncovered this article interesting? Observe us on Twitter and LinkedIn to examine additional distinctive material we write-up.
Some pieces of this posting are sourced from:
thehackernews.com

 Police Bust $41m Email Scam Gang
Police Bust $41m Email Scam Gang