Russia’s cyber attacks against Ukraine surged by 250% in 2022 when when compared to two many years ago, Google’s Risk Assessment Group (TAG) and Mandiant disclosed in a new joint report.
The concentrating on, which coincided and has due to the fact persisted next the country’s military invasion of Ukraine in February 2022, focused heavily on the Ukrainian federal government and military entities, together with critical infrastructure, utilities, general public companies, and media sectors.
Mandiant mentioned it noticed, “more damaging cyber attacks in Ukraine through the initially 4 months of 2022 than in the preceding 8 several years with attacks peaking around the get started of the invasion.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
As numerous as 6 distinctive wiper strains – together with WhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, Industroyer2, and SDelete – have been deployed towards Ukrainian networks, suggesting a willingness on the component of Russian threat actors to forgo persistent obtain.
Phishing attacks aimed at NATO countries witnessed a 300% spike in excess of the program of the identical time period. These initiatives have been pushed by a Belarusian federal government-backed team dubbed PUSHCHA (aka Ghostwriter or UNC1151) that is aligned with Russia.
“Russian authorities-backed attackers have engaged in an intense, multi-pronged exertion to achieve a decisive wartime edge in cyberspace, typically with blended results,” TAG’s Shane Huntley famous.
Some of the crucial actors concerned in the attempts include FROZENBARENTS (aka Sandworm or Voodoo Bear), FROZENLAKE (aka APT28 or Extravagant Bear), COLDRIVER (aka Callisto Team), FROZENVISTA (aka DEV-0586 or UNC2589), and SUMMIT (aka Turla or Venomous Bear).
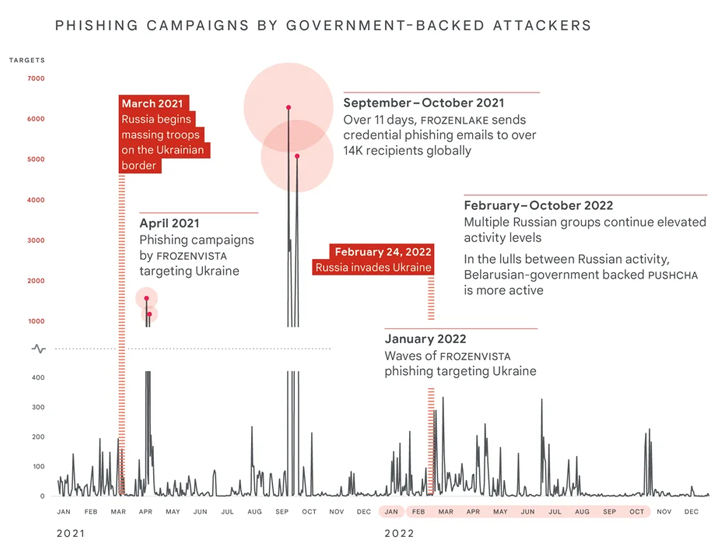
The uptick in the intensity and frequency of the operations apart, the invasion has also been accompanied by the Kremlin partaking in covert and overt information and facts functions intended to form public perception with the purpose of undermining the Ukrainian governing administration, fracturing intercontinental guidance for Ukraine, and preserve domestic assistance for Russia.
“GRU-sponsored actors have used their accessibility to steal delicate information and release it to the general public to more a narrative, or use that identical obtain to carry out destructive cyber attacks or info operations strategies,” the tech huge stated.
With the war splintering hacking groups about political allegiances, and in some instances, even resulting in them to shut shop, the enhancement further factors to a “noteworthy change in the Japanese European cybercriminal ecosystem” in a manner that blurs the traces between monetarily inspired actors and state-sponsored attackers.
This is evidenced by the point that UAC-0098, a danger actor that has traditionally shipped the IcedID malware, was noticed repurposing its strategies to assault Ukraine as component of a established of ransomware attacks.
Some associates of UAC-0098 are assessed to be previous members of the now-defunct Conti cybercrime group. TrickBot, which was absorbed into the Conti procedure final 12 months prior to the latter’s shutdown, has also resorted to systematically focusing on Ukraine.
It truly is not just Russia, as the ongoing conflict has led Chinese federal government-backed attackers these kinds of as CURIOUS GORGE (aka UNC3742) and BASIN (aka Mustang Panda) to shift their concentrate in direction of Ukrainian and Western European targets for intelligence collecting.
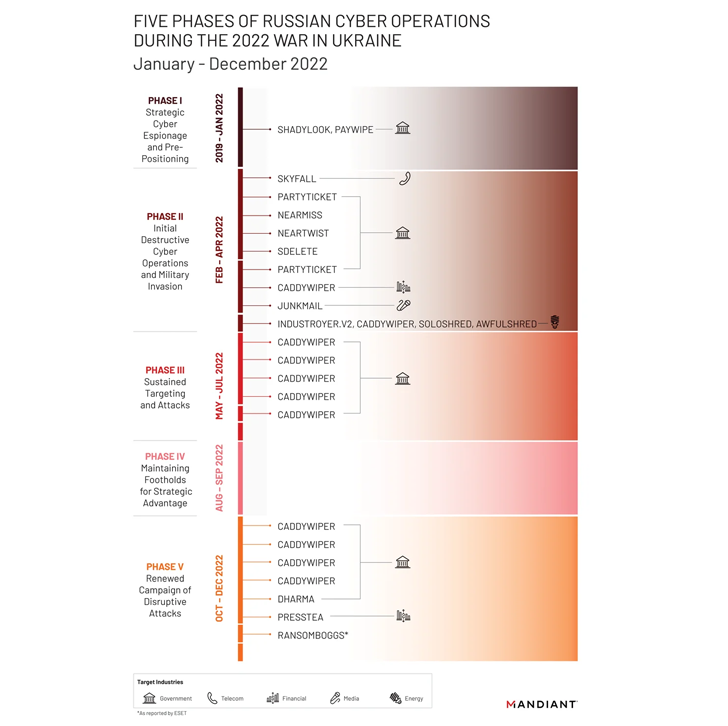
“It is distinct cyber will continue to perform an integral part in upcoming armed conflict, supplementing common kinds of warfare,” Huntley reported.
The disclosure will come as the Computer Unexpected emergency Response Workforce of Ukraine (CERT-UA) warned of phishing e-mail concentrating on corporations and establishments that purport to be critical security updates but actually incorporate executables that lead to the deployment of remote desktop control software package on the contaminated units.
CERT-UA attributed the operation to a risk actor it tracks beneath the moniker UAC-0096, which was earlier detected adopting the exact modus operandi again in late January 2022 in the weeks main to the war.
“A calendar year following Russia released its full-scale invasion of Ukraine, Russia remains unsuccessful in bringing Ukraine underneath its manage as it struggles to defeat months of compounding strategic and tactical failures,” cybersecurity business Recorded Upcoming claimed in a report released this month.
“Irrespective of Russia’s common military services setbacks and its failure to substantively progress its agenda via cyber operations, Russia maintains its intent to convey Ukraine below Russian management,” it additional, while also highlighting its “burgeoning navy cooperation with Iran and North Korea.”
Observed this write-up interesting? Comply with us on Twitter and LinkedIn to read through a lot more exceptional articles we put up.
Some parts of this report are sourced from:
thehackernews.com


 Cyber Espionage Group Earth Kitsune Deploys WhiskerSpy Backdoor in Latest Attacks
Cyber Espionage Group Earth Kitsune Deploys WhiskerSpy Backdoor in Latest Attacks