Unknown malware offers a significant cybersecurity menace and can result in major destruction to organizations and individuals alike. When left undetected, malicious code can acquire accessibility to confidential data, corrupt facts, and enable attackers to acquire manage of programs. Come across out how to keep away from these situation and detect not known malicious habits successfully.
Issues of new threats’ detection
While known malware family members are much more predictable and can be detected extra effortlessly, unfamiliar threats can take on a wide range of sorts, causing a bunch of troubles for their detection:
Detection of new threats
When analyzing recognised malware households, scientists can just take advantage of current information about the malware, this kind of as its actions, payloads, and known vulnerabilities, in order to detect and answer to it.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
But working with new threats, scientists have to begin from scratch, making use of the subsequent manual:
Action 1. Use reverse engineering to assess the code of the malware to detect its intent and destructive nature.
Stage 2. Use static investigation to examine the malware’s code to discover its habits, payloads, and vulnerabilities.
Phase 3. Use dynamic assessment to observe the actions of the malware in the course of execution.
Step 4. Use sandboxing to run the malware in an isolated setting to notice its actions with no harming the technique.
Action 5. Use heuristics to determine likely malicious code primarily based on observable designs and behaviors.
Stage 6. Review the outcomes of reverse engineering, static investigation, dynamic analysis, sandboxing, and heuristics to figure out if the code is malicious.
There are loads of instruments from Procedure Observe and Wireshark to ANY.Run to support you go by the 1st 5 steps. But how to attract a specific conclusion, what should you fork out interest to when getting all this knowledge?
The answer is easy – aim on indicators of destructive behavior.
Keep track of suspicious actions for successful detection
Distinct signatures are used to detect threats. In laptop security terminology, a signature is a usual footprint or sample associated with a malicious attack on a personal computer network or system.
Aspect of these signatures is behavioral ones. It can be unachievable to do a little something in the OS and go away no tracing at the rear of. We can discover what software package or script it was by using their suspicious activities.
You can run a suspicious program in a sandbox to observe the actions of the malware and detect any destructive behavior, such as:
- abnormal file system action,
- suspicious system generation and termination
- abnormal networking action
- looking through or modifying process files
- entry program sources
- make new people
- hook up to distant servers
- execute other destructive instructions
- exploit identified vulnerabilities in the program
Microsoft Business office is launching PowerShell – appears to be suspicious, right? An application adds itself to the scheduled tasks – definitely pay back attention to it. A svchost course of action operates from the temp registry – some thing is absolutely mistaken.
You can often detect any risk by its behavior, even with out signatures.
Let’s confirm it.
Use scenario #1
In this article is a sample of the stealer. What does it do? Steals user info, cookies, wallets, and so on. How can we detect it? For illustration, it reveals by itself when the application opens the Chrome browser’s Login Information file.
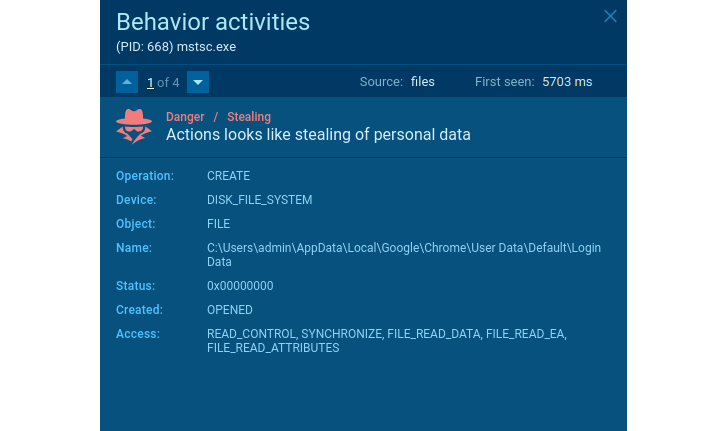 Stealer’s suspicious behavior
Stealer’s suspicious behavior
The action in the network traffic also announces the threat’s malicious intentions. A reputable application would by no means ship qualifications, OS attributes, and other delicate facts gathered locally.
In the case of targeted traffic, malware can be detected by well-recognised options. Agent Tesla in some circumstances does not encrypt information despatched from an infected technique like in this sample.
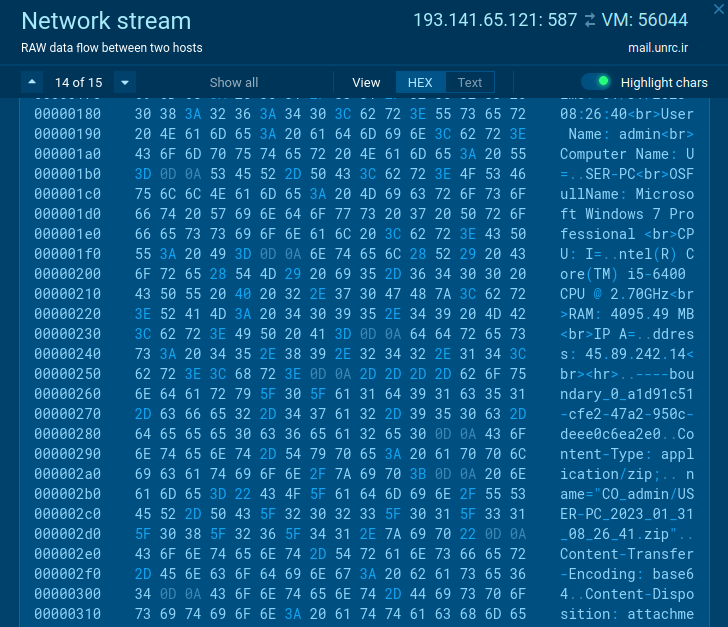 Suspicious action in the network website traffic
Suspicious action in the network website traffic
Use circumstance #2
There are not a lot of authentic applications that will need to end Windows Defender or other applications to shield the OS or make an exclusion for alone. Each and every time you face this type of conduct – that’s a indication of suspicious action.
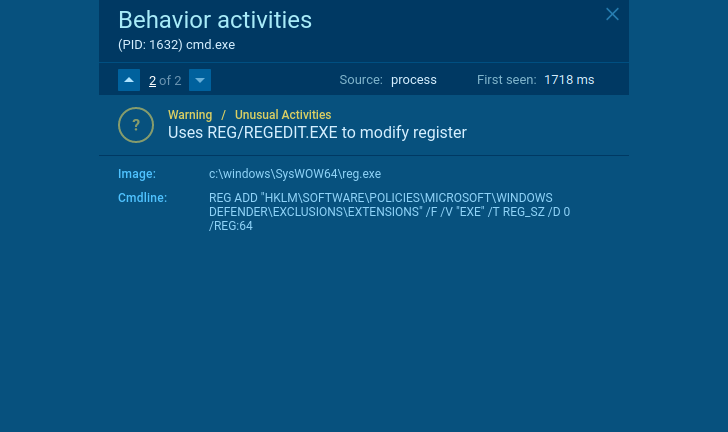 Suspicious habits
Suspicious habits
Does the software delete shadow copies? Seems to be like ransomware. Does it take out shadow copies and produce a TXT/HTML file with readme textual content in every single directory? It’s just one additional proof of it.
If the user facts is encrypted in the system, we can be guaranteed it is ransomware. Like what occurred in this malicious case in point. Even if we do not know the family, we can establish what variety of security danger this computer software poses and then act accordingly and consider measures to guard operating stations and the organization’s network.
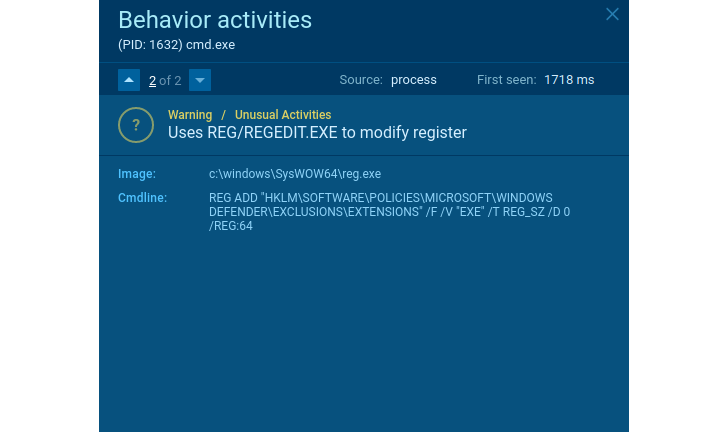 Suspicious conduct
Suspicious conduct
We can attract conclusions about just about all kinds of malware dependent on the actions observed in the sandbox. Consider ANY.Run on the net interactive support to monitor it – you can get the first results right away and see all malware’s motion in true time. Particularly what we will need to catch any suspicious things to do.
Write the “HACKERNEWS2” promo code at [email protected] employing your business email handle and get 14 days of ANY.Run top quality subscription for free of charge!
Wrapping up
Cybercriminals can use mysterious threats to extort organizations for dollars and start large-scale cyberattacks. Even if the malware family is not detected – we can often conclude the threat’s features by thinking about its habits. Applying this data, you can make data security to avoid any new threats. Conduct examination improves your means to reply to new and not known threats and strengthens your organization’s safety without more expenses.
Identified this post appealing? Follow us on Twitter and LinkedIn to read through a lot more distinctive content we publish.
Some parts of this article are sourced from:
thehackernews.com

 Google Reveals Alarming Surge in Russian Cyber Attacks Against Ukraine
Google Reveals Alarming Surge in Russian Cyber Attacks Against Ukraine