Risk actors’ use of Cloudflare R2 to host phishing internet pages has witnessed a 61-fold increase about the previous six months.
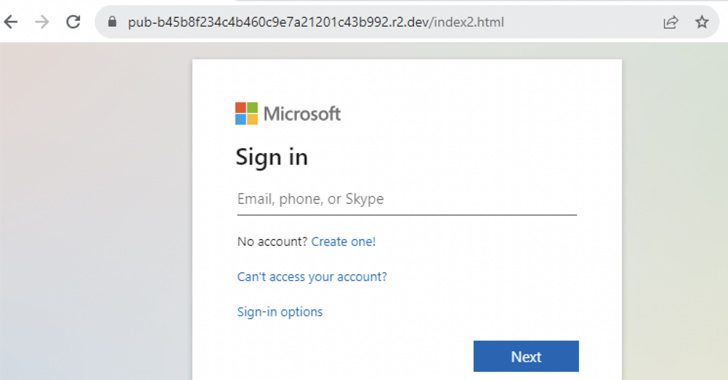
“The greater part of the phishing strategies focus on Microsoft login credentials, although there are some web pages concentrating on Adobe, Dropbox, and other cloud apps,” Netskope security researcher Jan Michael explained.
Cloudflare R2, analogous to Amazon Web Service S3, Google Cloud Storage, and Azure Blob Storage, is a data storage company for the cloud.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The advancement will come as the full selection of cloud applications from which malware downloads originate has increased to 167, with Microsoft OneDrive, Squarespace, GitHub, SharePoint, and Weebly taking the top five spots.

The phishing campaigns discovered by Netskope not only abuse Cloudflare R2 to distribute static phishing internet pages, but also leverage the company’s Turnstile providing, a CAPTCHA replacement, to area these types of pages at the rear of anti-bot barriers to evade detection.
In performing so, it helps prevent online scanners like urlscan.io from achieving the actual phishing internet site, as the CAPTCHA exam results in a failure.
As an more layer of detection evasion, the malicious web sites are created to load the written content only when sure situations are met.
“The malicious internet site necessitates a referring site to incorporate a timestamp following a hash image in the URL to display the real phishing website page,” Michael reported. “On the other hand, the referring internet site calls for a phishing internet site passed on to it as a parameter.”
In the party no URL parameter is passed to the referring site, guests are redirected to www.google[.]com.
The improvement arrives a thirty day period soon after the cybersecurity firm disclosed information of a phishing marketing campaign that was uncovered hosting its bogus login internet pages in AWS Amplify to steal users’ banking and Microsoft 365 credentials, together with card payment specifics by means of Telegram’s Bot API.
Discovered this posting interesting? Observe us on Twitter and LinkedIn to browse more exceptional written content we publish.
Some pieces of this posting are sourced from:
thehackernews.com

 Multiple Flaws Found in ScrutisWeb Software Exposes ATMs to Remote Hacking
Multiple Flaws Found in ScrutisWeb Software Exposes ATMs to Remote Hacking