Practically 2,000 Citrix NetScaler circumstances have been compromised with a backdoor by weaponizing a not too long ago disclosed critical security vulnerability as component of a large-scale attack.
“An adversary appears to have exploited CVE-2023-3519 in an automatic vogue, inserting web shells on susceptible NetScalers to attain persistent obtain,” NCC Team mentioned in an advisory released Tuesday.
“The adversary can execute arbitrary instructions with this webshell, even when a NetScaler is patched and/or rebooted.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
CVE-2023-3519 refers to a critical code injection vulnerability impacting NetScaler ADC and Gateway servers that could guide to unauthenticated distant code execution. It was patched by Citrix last thirty day period.

The enhancement arrives a 7 days immediately after the Shadowserver Foundation said it determined near to 7,000 susceptible, unpatched NetScaler ADC and Gateway scenarios on the net and the flaw is getting abused to fall PHP web shells on susceptible servers for remote entry.
A comply with-up investigation by NCC Team has now disclosed that 1,828 NetScaler servers continue being backdoored, out of which roughly 1,248 are already patched against the flaw.
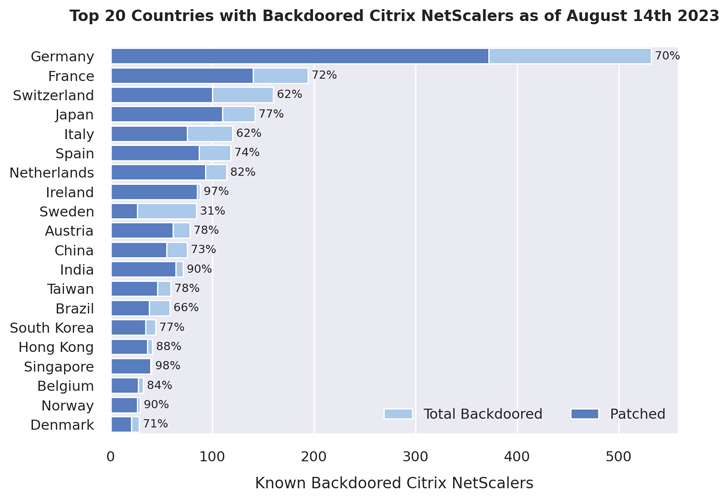
“This suggests that even though most directors were being knowledgeable of the vulnerability and have considering the fact that patched their NetScalers to a non-vulnerable edition, they have not been (thoroughly) checked for indications of profitable exploitation,” the business claimed.
In whole, as quite a few as 2,491 web shells have been identified throughout 1,952 unique NetScaler appliances. A bulk of the compromised cases are positioned in Germany, France, Switzerland, Japan, Italy, Spain, the Netherlands, Ireland, Sweden, and Austria.

The European aim aside, a different notable element is that when Canada, Russia, and the U.S. experienced countless numbers of vulnerable NetScaler servers late very last thirty day period, no web shells had been located on any of them.
The mass exploitation campaign is estimated to have compromised 6.3% of the 31,127 NetScaler circumstances that had been inclined to CVE-2023-3519 as of July 21, 2023.
The disclosure also comes as Mandiant has unveiled an open up-supply software to assistance companies scan their Citrix appliances for evidence of write-up-exploitation action associated to CVE-2023-3519.
Found this short article exciting? Abide by us on Twitter and LinkedIn to study a lot more exceptional articles we submit.
Some components of this article are sourced from:
thehackernews.com


 Cybercriminals Abusing Cloudflare R2 for Hosting Phishing Pages, Experts Warn
Cybercriminals Abusing Cloudflare R2 for Hosting Phishing Pages, Experts Warn