Danger actors are significantly employing a phishing-as-a-assistance (PhaaS) toolkit dubbed EvilProxy to pull off account takeover attacks aimed at substantial-rating executives at well known organizations.
In accordance to Proofpoint, an ongoing hybrid campaign has leveraged the service to concentrate on countless numbers of Microsoft 365 consumer accounts, sending about 120,000 phishing email messages to hundreds of businesses around the globe involving March and June 2023.
Just about 39% of the hundreds of compromised consumers are explained to be C-stage executives, including CEOs (9%) and CFOs (17%). The attacks have also singled out personnel with access to monetary belongings or delicate info. At minimum 35% of all compromised end users had additional account protections enabled.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The campaigns are viewed as a response to the improved adoption of multi-factor authentication (MFA) in enterprises, prompting risk actors to evolve their practices to bypass new security levels by incorporating adversary-in-the-center (AitM) phishing kits to siphon credentials, session cookies, and one-time passwords.
“Attackers use new innovative automation to correctly establish in serious-time regardless of whether a phished person is a higher-amount profile, and right away obtain obtain to the account, whilst disregarding a lot less beneficial phished profiles,” the organization security agency said.
EvilProxy was initial documented by Resecurity in September 2022, detailing its skill to compromise person accounts associated with Apple iCloud, Facebook, GoDaddy, GitHub, Google, Dropbox, Instagram, Microsoft, NPM, PyPI, RubyGems, Twitter, Yahoo, and Yandex, among other individuals.
It is really marketed as a membership for $400 a month, a determine that can climb up to $600 for Google accounts.

PhaaS toolkits are an evolution of the cybercrime economic system, decreasing the barrier for criminals with decrease technical expertise to carry out subtle phishing attacks at scale in a seamless and value-efficient manner.
“Nowadays, all an attacker desires is to set up a campaign using a level-and-simply click interface with customizable options, this sort of as bot detection, proxy detection, and geofencing,” security scientists Shachar Gritzman, Moshe Avraham, Tim Kromphardt, Jake Gionet, and Eilon Bendet explained.
“This comparatively straightforward and lower-charge interface has opened a floodgate of successful MFA phishing action.”
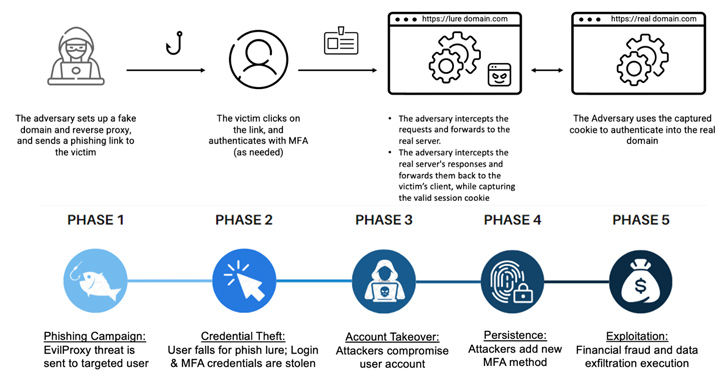
The hottest wave of attacks commences with phishing email messages that masquerade as dependable expert services like Adobe and DocuSign to trick recipients into clicking on malicious URLs that activate a multi-phase redirection chain to acquire them to a lookalike Microsoft 365 login website page, which functions as a reverse proxy to stealthily capture the information and facts entered in the sort.
But in a curious twist, the attacks deliberately skip person targeted visitors originating from Turkish IP addresses by redirecting them to legitimate web sites, indicating that the campaign operators could be based out of the place.

A effective account takeover is adopted by the danger actor using ways to “cement their foothold” in the organization’s cloud setting by incorporating their very own MFA technique, these as a two-factor authenticator app, so as to attain persistent remote access and carry out lateral movement and malware proliferation.
The entry is further more monetized to either perform money fraud, exfiltrate private data, or provide the compromised consumer accounts to other attackers.
“Reverse proxy threats (and EvilProxy in certain) are a powerful menace in present day dynamic landscape and are outcompeting the much less able phish kits of the past,” the scientists reported, pointing out that “not even MFA is a silver bullet towards subtle cloud-centered threats.”
“While these attacks’ original menace vector is email-dependent, their last objective is to compromise and exploit useful cloud person accounts, assets, and knowledge.”

The growth comes as Imperva unveiled information of an ongoing Russian-origin phishing marketing campaign that aims to deceive likely targets and steal their credit history card and bank data considering that at least Could 2022 by means of booby-trapped inbound links shared by means of WhatsApp messages.
The action spans 800 diverse scam domains, impersonating more than 340 firms across 48 languages. This includes nicely-identified financial institutions, postal products and services, deal shipping and delivery solutions, social media, and e-commerce web pages.
“By leveraging a large-excellent, solitary-website page software, the scammers have been ready to dynamically generate a convincing website that impersonated a legitimate website, fooling customers into a bogus sense of security,” Imperva mentioned.
In nonetheless a further variation of a social engineering attack discovered by eSentire, destructive actors have been noticed getting in touch with advertising gurus on LinkedIn in an try to distribute a .NET-based loader malware codenamed HawkEyes that, in turn, is made use of to launch Ducktail, an information stealer with a specific concentrate on accumulating Fb Business account data.
“Ducktail is acknowledged to focus on Facebook Advert and Small business accounts,” eSentire scientists claimed. “Operators will use stolen login info to incorporate email addresses to Facebook Small business accounts. When email messages are extra, a registration backlink is produced by which the threat actor can grant themselves obtain.”
Identified this article exciting? Abide by us on Twitter and LinkedIn to study much more unique written content we submit.
Some pieces of this write-up are sourced from:
thehackernews.com

 Interpol Busts Phishing-as-a-Service Platform ’16Shop,’ Leading to 3 Arrests
Interpol Busts Phishing-as-a-Service Platform ’16Shop,’ Leading to 3 Arrests