Destructive loader courses capable of trojanizing Android applications are remaining traded on the legal underground for up to $20,000 as a way to evade Google Engage in Store defenses.
“The most well-liked software classes to cover malware and undesirable software contain cryptocurrency trackers, economical applications, QR-code scanners, and even dating applications,” Kaspersky reported in a new report based on messages posted on on the net discussion boards concerning 2019 and 2023.
Dropper applications are the most important means for danger actors on the lookout to sneak malware by means of the Google Enjoy Keep. These kinds of apps frequently masquerade as seemingly innocuous apps, with destructive updates introduced on clearing the critique process and the purposes have amassed a considerable consumer base.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This is reached by utilizing a loader application that’s liable for injecting malware into a cleanse application, which is then designed offered for down load from the app marketplace. Customers who install the tampered application are prompted to grant it intrusive permissions to facilitate destructive things to do.
The apps, in some instances, also integrate anti-evaluation functions to detect if they are being debugged or installed in a sandboxed atmosphere, and if so, halt their functions on the compromised gadgets.
As an additional possibility, danger actors can invest in a Google Engage in developer account – possibly hacked or newly produced by the sellers – for any where in between $60 and $200, depending on the number of previously published apps and obtain counts.
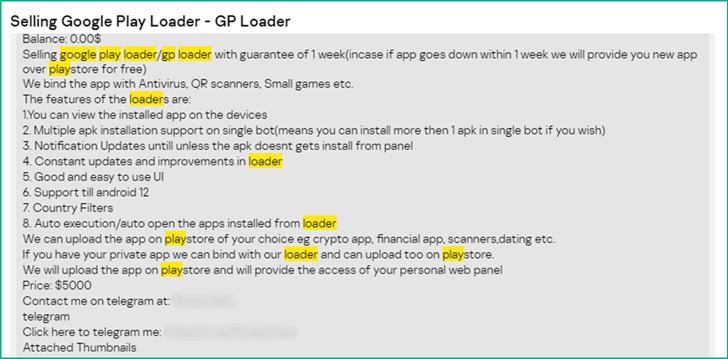
App developer accounts lacking in robust password or two-factor authentication (2FA) protections can be trivially cracked and set up for sale, thereby allowing for other actors to add malware to current apps.
A third alternate is the use of APK binding solutions, which are dependable for hiding a destructive APK file in a respectable application, for distributing the malware by means of phishing texts and doubtful web-sites advertising and marketing cracked online games and program.
Binding companies, as opposed to loaders, value fewer owing to the actuality that the poisoned apps are not obtainable through the Google Participate in Retailer. Notably, the technique has been made use of to provide Android banking trojans like SOVA and Xenomorph in the earlier.
Upcoming WEBINARLearn to Protected the Id Perimeter – Proven Techniques
Strengthen your company security with our impending professional-led cybersecurity webinar: Examine Id Perimeter methods!
Really don’t Pass up Out – Preserve Your Seat!
Some other illicit products and services supplied for sale on cybercrime markets consist of malware obfuscation ($30), web injects ($25-$80), and digital non-public servers ($300), the latter of which can be employed to management contaminated equipment or to redirect user traffic.
On top of that, attackers can obtain installs for their Android apps (authentic or or else) through Google Adverts for $.5 on normal. Set up costs change based mostly on the targeted place.
To mitigate hazards posed by Android malware, end users are advised to refrain from setting up applications from unidentified resources, scrutinize app permissions, and maintain their equipment up-to-day.
Found this post intriguing? Comply with us on Twitter and LinkedIn to go through a lot more distinctive content material we put up.
Some areas of this post are sourced from:
thehackernews.com


![[ebook] a step by step guide to cyber risk assessment](https://thecybersecurity.news/data/2023/04/eBook-A-Step-by-Step-Guide-to-Cyber-Risk-Assessment-80x80.png) [eBook] A Step-by-Step Guide to Cyber Risk Assessment
[eBook] A Step-by-Step Guide to Cyber Risk Assessment