A “by-style flaw” uncovered in Microsoft Azure could be exploited by attackers to attain obtain to storage accounts, shift laterally in the environment, and even execute distant code.
“It is possible to abuse and leverage Microsoft Storage Accounts by manipulating Azure Features to steal entry-tokens of bigger privilege identities, go laterally, possibly accessibility critical business belongings, and execute distant code (RCE),” Orca explained in a new report shared with The Hacker Information.
The exploitation route that underpins this attack is a mechanism identified as Shared Crucial authorization, which is enabled by default on storage accounts.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
According to Microsoft, Azure generates two 512-bit storage account accessibility keys when building a storage account. These keys can be utilised to authorize obtain to info by using Shared Important authorization, or by way of SAS tokens that are signed with the shared crucial.
“Storage account access keys present comprehensive access to the configuration of a storage account, as properly as the knowledge,” Microsoft notes in its documentation. “Access to the shared vital grants a consumer full obtain to a storage account’s configuration and its knowledge.”
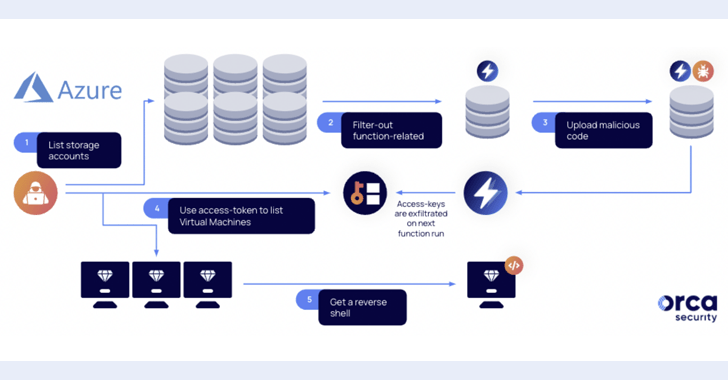
The cloud security company mentioned these entry tokens can be stolen by manipulating Azure Functions, likely enabling a menace actor with accessibility to an account with Storage Account Contributor position to escalate privileges and take over methods.
Particularly, ought to a managed identity be made use of to invoke the Functionality app, it could be abused to execute any command. This, in transform, is produced doable owing to the actuality that a committed storage account is made when deploying an Azure Operate app.
“Once an attacker locates the storage account of a Function app that is assigned with a sturdy managed identification, it can operate code on its behalf and as a outcome receive a subscription privilege escalation (PE),” Orca researcher Roi Nisimi explained.
Future WEBINARLearn to Safe the Identification Perimeter – Proven Procedures
Improve your enterprise security with our forthcoming expert-led cybersecurity webinar: Check out Id Perimeter procedures!
Don’t Miss out on Out – Save Your Seat!
In other terms, by exfiltrating the access-token of the Azure Purpose app’s assigned managed id to a remote server, a risk actor can elevate privileges, go laterally, accessibility new sources, and execute a reverse shell on digital equipment.
“By overriding functionality documents in storage accounts, an attacker can steal and exfiltrate a bigger-privileged identity and use it to move laterally, exploit and compromise victims’ most worthwhile crown jewels,” Nisimi stated.
As mitigations, it is really recommended that businesses consider disabling Azure Shared Vital authorization and applying Azure Active Listing authentication alternatively. In a coordinated disclosure, Microsoft claimed it “plans to update how Capabilities consumer equipment operate with storage accounts.”
“This features modifications to much better support situations employing id. After identification-centered connections for AzureWebJobsStorage are normally available and the new encounters are validated, identification will come to be the default manner for AzureWebJobsStorage, which is supposed to shift absent from shared important authorization,” the tech giant additional additional.
The conclusions arrive weeks soon after Microsoft patched a misconfiguration issue impacting Azure Active Directory that created it probable to tamper with Bing research success and a reflected XSS vulnerability in Azure Support Fabric Explorer (SFX) that could guide to unauthenticated remote code execution.
Uncovered this short article interesting? Abide by us on Twitter and LinkedIn to read through additional unique articles we submit.
Some parts of this posting are sourced from:
thehackernews.com

 Cybercriminals Turn to Android Loaders on Dark Web to Evade Google Play Security
Cybercriminals Turn to Android Loaders on Dark Web to Evade Google Play Security