Senior executives doing the job in U.S.-centered corporations are remaining qualified by a new phishing campaign that leverages a well-liked adversary-in-the-middle (AiTM) phishing toolkit named EvilProxy to conduct credential harvesting and account takeover attacks.
Menlo Security stated the action started off in July 2023, generally singling out banking and economic expert services, insurance plan, house management and actual estate, and production sectors.
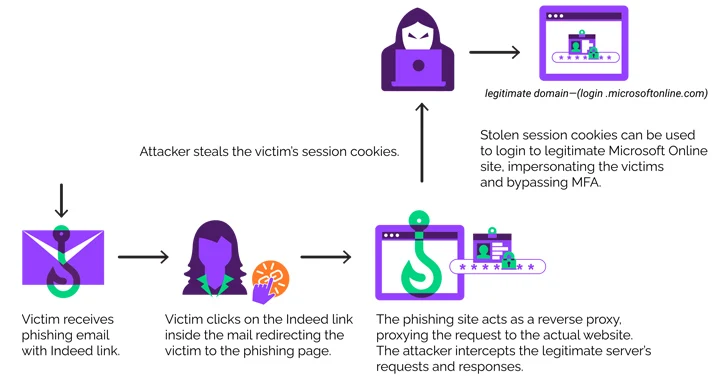
“The threat actors leveraged an open up redirection vulnerability on the position look for system ‘indeed.com,’redirecting victims to malicious phishing web pages impersonating Microsoft,” security researcher Ravisankar Ramprasad said in a report published very last 7 days.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
EvilProxy, initial documented by Resecurity in September 2022, functions as a reverse proxy that is set up in between the goal and a legitimate login page to intercept qualifications, two-factor authentication (2FA) codes, and session cookies to hijack accounts of fascination.

The risk actors driving the AiTM phishing package are tracked by Microsoft beneath the moniker Storm-0835 and are approximated to have hundreds of customers.
“These cyber criminals fork out regular license expenses ranging from $200 to $1,000 USD and have out everyday phishing campaigns,” the tech large said. “Since so many threat actors use these expert services, it is impractical to attribute campaigns to certain actors.”
In the most recent established of attacks documented by Menlo Security, victims are despatched phishing emails with a misleading hyperlink pointing to In fact, which, in switch, redirects the individual to an EvilProxy web site to harvest the credentials entered.
This is completed by getting edge of an open redirect flaw, which takes place when a failure to validate user enter triggers a susceptible web site to redirect users to arbitrary web internet pages, bypassing security guardrails.

“The subdomain ‘t.without a doubt.com’ is provided with parameters to redirect the shopper to one more target (example.com),” Ramprasad reported.
“The parameters in the URL that comply with the ‘?’ are a combination of parameters exclusive to in truth.com and the goal parameter whose argument consists of the vacation spot URL. Consequently the user on clicking the URL ends up receiving redirected to illustration.com. In an precise attack, the user would be redirected to a phishing web page.”
The development arrives as menace actors are leveraging Dropbox to build faux login pages with embedded URLs that, when clicked, redirect customers to bogus sites that are designed to steal Microsoft account credentials as part of a business enterprise email compromise (BEC) plan.

“It really is still a different illustration of how hackers are using genuine solutions in what we contact BEC 3. attacks,” Test Place stated. “These attacks are incredibly tricky to stop and determine, for both of those security services and end users.”
Microsoft, in its Digital Protection Report, observed how “menace actors are adapting their social engineering strategies and use of technology to carry out much more subtle and high priced BEC attacks” by abusing cloud-dependent infrastructure and exploiting trustworthy organization interactions.
It also will come as the Police Service of Northern Ireland warned of an uptick in qishing e-mails, which contain sending an email with a PDF doc or a PNG impression file containing a QR code in an endeavor to sidestep detection and trick victims into visiting destructive web pages and credential harvesting internet pages.
Found this posting attention-grabbing? Stick to us on Twitter and LinkedIn to read extra distinctive material we put up.
Some components of this short article are sourced from:
thehackernews.com

 Webinar: How vCISOs Can Navigating the Complex World of AI and LLM Security
Webinar: How vCISOs Can Navigating the Complex World of AI and LLM Security