An advertisement fraud botnet dubbed PEACHPIT leveraged an army of hundreds of countless numbers of Android and iOS equipment to create illicit income for the danger actors powering the plan.
The botnet is aspect of a much larger China-centered operation codenamed BADBOX, which also involves advertising off-brand name cell and linked Television (CTV) units on common on the net merchants and resale web sites that are backdoored with an Android malware strain named Triada.
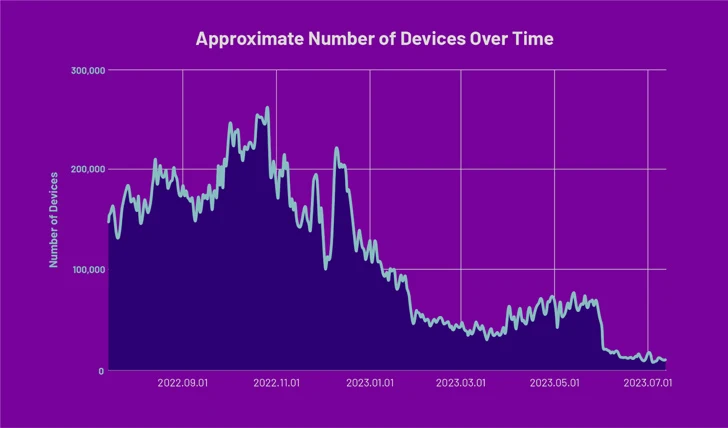
“The PEACHPIT botnet’s conglomerate of connected applications have been observed in 227 international locations and territories, with an estimated peak of 121,000 gadgets a day on Android and 159,000 devices a working day on iOS,” HUMAN stated.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The bacterial infections are stated to have been understood as a result of a collection of 39 apps that ended up put in a lot more than 15 million moments. Devices equipped with the malware allowed the operators to steal delicate knowledge, build household proxy exit friends, and commit advert fraud through the bogus apps.

It really is at this time not very clear how the Android equipment are compromised with a firmware backdoor, but proof factors to a hardware supply chain attack.
“Risk actors can also use the backdoored units to produce WhatsApp messaging accounts by stealing one-time passwords from the units,” the enterprise said.
“Also, risk actors can use the devices to build Gmail accounts, evading common bot detection due to the fact the account looks like it was established from a standard tablet or smartphone, by a true person.”
Aspects about the legal business were being initially documented by Craze Micro in May perhaps 2023, attributing it to an adversary it tracks as Lemon Team.
HUMAN stated that it identified at minimum 200 distinctive Android product types, including cellular phones, tablets, and CTV goods, that have exhibited indications of BADBOX infection, suggesting a common procedure.
A noteworthy element of the ad fraud is the use of counterfeit apps on Android and iOS manufactured readily available on main application marketplaces these kinds of as the Apple App Retailer and Google Engage in Retail outlet as very well as those people that are automatically downloaded to backdoored BADBOX gadgets.

Current in the Android apps is a module liable for creating hidden WebViews that are then utilized to request, render, and simply click on adverts, and masquerading the advertisement requests as originating from authentic apps, a method beforehand noticed in the case of VASTFLUX.
The fraud prevention firm mentioned that it labored with Apple and Google to disrupt the operation, including “the remainder of BADBOX should really be regarded as dormant: the C2 servers powering the BADBOX firmware backdoor infection have been taken down by the danger actors.”
What’s much more, an update pushed out earlier this yr has been discovered to get rid of the modules powering PEACHPIT on BADBOX-contaminated devices in response to mitigation measures deployed in November 2022.
That getting explained, it truly is suspected the attackers are changing their tactics in a very likely try to circumvent the defenses.
“What will make issues worse is the degree of obfuscation the operators went as a result of to go undetected, a sign of their improved sophistication,” HUMAN said. “Anybody can unintentionally buy a BADBOX machine on-line without the need of at any time figuring out it was faux, plugging it in, and unknowingly opening this backdoor malware.”
Observed this report fascinating? Abide by us on Twitter and LinkedIn to read extra special information we put up.
Some components of this write-up are sourced from:
thehackernews.com


 Cybercriminals Using EvilProxy Phishing Kit to Target Senior Executives in U.S. Firms
Cybercriminals Using EvilProxy Phishing Kit to Target Senior Executives in U.S. Firms