Menace actors are marketing a new crypter and loader called ASMCrypt, which has been described as an “progressed variation” of a different loader malware recognized as DoubleFinger.
“The plan behind this style of malware is to load the final payload with no the loading procedure or the payload itself becoming detected by AV/EDR, and many others.,” Kaspersky claimed in an analysis posted this week.
DoubleFinger was initial documented by the Russian cybersecurity corporation, detailing an infection chains leveraging the malware to propagate a cryptocurrency stealer dubbed GreetingGhoul to victims in Europe, the U.S., and Latin The us.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
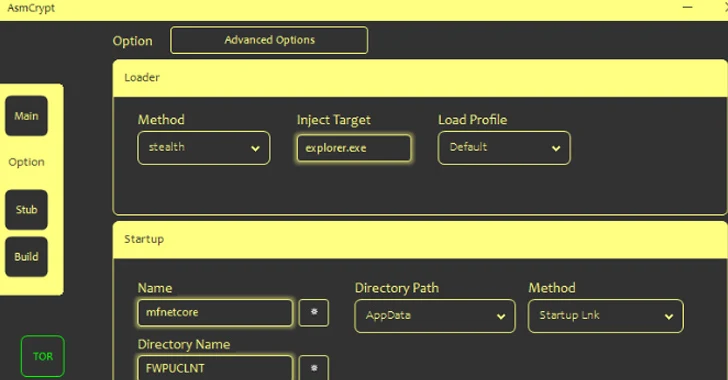
ASMCrypt, as soon as acquired and introduced by the customers, is built to build make contact with with a backend service more than the TOR network working with difficult-coded qualifications, therefore enabling the buyers to establish payloads of their decision for use in their strategies.
“The application produces an encrypted blob hidden inside a .PNG file,” Kaspersky claimed. “This graphic will have to be uploaded to an graphic hosting internet site.”
Loaders have turn into more and more common for their ability to act as a malware shipping service that can be used by other menace actors to attain initial accessibility to networks for conducting ransomware attacks, info theft, and other destructive cyber actions.

This includes gamers new and established, these types of as Bumblebee, CustomerLoader, and GuLoader, which have been applied to supply a variety of malicious software. Curiously, all payloads downloaded by CustomerLoader are dotRunpeX artifacts, which, in transform, deploys the remaining-phase malware.
“CustomerLoader is highly probable associated with a Loader-as-a-Provider and made use of by several risk actors,” Sekoia.io stated. “It is possible that CustomerLoader is a new stage added in advance of the execution of the dotRunpeX injector by its developer.”
Bumblebee, on the other hand, reemerged in a new distribution campaign right after a two-thirty day period hiatus in the direction of the conclusion of August 2023 that employed Web Distributed Authoring and Versioning (WebDAV) servers to disseminate the loader, a tactic previously adopted in IcedID attacks.
“In this energy, risk actors used malicious spam e-mails to distribute Windows shortcut (.LNK) and compressed archive (.ZIP) files that contains .LNK files,” Intel 471 said. “When activated by the consumer, these LNK information execute a predetermined set of commands developed to obtain Bumblebee malware hosted on WebDAV servers.”
The loader is an current variant that has transitioned from working with the WebSocket protocol to TCP for command-and-regulate server (C2) communications as nicely as from a hard-coded list of C2 servers to a area technology algorithm (DGA) that aims to make it resilient in the face of area takedown.
In what is a signal of a maturing cybercrime economic system, threat actors previously assumed to be unique have partnered with other teams, as evidenced in the situation of a “dark alliance” among GuLoader and Remcos RAT.
Although ostensibly marketed as respectable program, a modern assessment from Examine Point uncovered the use of GuLoader to predominantly distribute Remcos RAT, even as the former is now currently being marketed as a crypter underneath a new name referred to as TheProtect that will make its payload absolutely undetectable by security software package.
Approaching WEBINARFight AI with AI — Battling Cyber Threats with Upcoming-Gen AI Resources
Prepared to tackle new AI-driven cybersecurity issues? Sign up for our insightful webinar with Zscaler to handle the expanding danger of generative AI in cybersecurity.
Supercharge Your Capabilities
“An particular person operating below the alias EMINэM administers both sites BreakingSecurity and VgoStore that overtly provide Remcos and GuLoader,” the cybersecurity company said.
“The people guiding these providers are deeply entwined within the cybercriminal local community, leveraging their platforms to facilitate unlawful routines and financial gain from the sale of malware-laden resources.”
The growth will come as new variations of an facts thieving malware referred to as Lumma Stealer have been spotted in the wild, with the malware dispersed by way of a phony internet site that mimics a respectable .DOCX to .PDF web site.
Therefore, when a file is uploaded, the site returns a malicious binary that masquerades as a PDF with a double extension “.pdf.exe” that, upon execution, harvests delicate information and facts from infected hosts.
It can be well worth noting that Lumma Stealer is the latest fork of a acknowledged stealer malware named Arkei, which has advanced into Vidar, Oski, and Mars around the past pair of a long time.
“Malware is continually evolving, as is illustrated by the Lumma Stealer, which has several variants with varying performance,” Kaspersky explained.
Found this short article attention-grabbing? Follow us on Twitter and LinkedIn to browse extra special material we publish.
Some sections of this write-up are sourced from:
thehackernews.com

 Lazarus Group Impersonates Recruiter from Meta to Target Spanish Aerospace Firm
Lazarus Group Impersonates Recruiter from Meta to Target Spanish Aerospace Firm