Cybercriminal actors earlier noticed delivering BazaLoader and IcedID as component of their malware strategies are said to have transitioned to a new loader called Bumblebee that is beneath active advancement.
“Based on the timing of its physical appearance in the threat landscape and use by multiple cybercriminal teams, it is most likely Bumblebee is, if not a immediate substitution for BazaLoader, then a new, multifunctional resource employed by actors that historically favored other malware,” enterprise security firm Proofpoint said in a report shared with The Hacker Information.
Campaigns distributing the new highly subtle loader are stated to have commenced in March 2022, even though sharing overlaps with destructive exercise top to the deployment of Conti and Diavol ransomware, raising the probability that the loader could act as a precursor for ransomware attacks.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Menace actors utilizing Bumblebee are connected with malware payloads that have been joined to stick to-on ransomware strategies,” the scientists said.
Apart from featuring anti-virtualization checks, Bumblebee is prepared in C++ and is engineered to act as a downloader for retrieving and executing up coming-phase payloads, such as Cobalt Strike, Sliver, Meterpreter, and shellcode.
Apparently, the elevated detection of the malware loader in the danger landscape corresponds to the disappearance of BazaLoader deployments due to the fact February 2022, a further preferred loader developed by the makers of the now-defunct TrickBot gang, which has considering that been absorbed into Conti.
Attack chains distributing Bumblebee have taken the sort of DocuSign-branded email phishing lures incorporating fraudulent inbound links or HTML attachments, leading probable victims to a compressed ISO file hosted on Microsoft OneDrive.
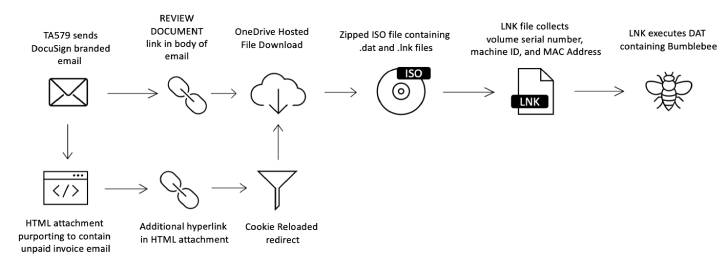
What is a lot more, the embedded URL in the HTML attachment can make use of a traffic path system (TDS) dubbed Prometheus — which is accessible for sale on underground platforms for $250 a month — to redirect the URLs to the archive data files primarily based on the time zone and cookies of the victims.
The ZIP files, in switch, include things like .LNK and .DAT data files, with the Windows shortcut file executing the latter that contains the Bumblebee downloader, before utilizing it to supply BazaLoader and IcedID malware.
A next marketing campaign in April 2022 concerned a thread-hijacking plan in which legitimate invoice-themed e-mail have been taken over to send out zipped ISO data files, which had been then applied to execute a DLL file to activate the loader.

Also observed is the abuse of the make contact with type present on the target’s web-site to send out a concept professing copyright violations of images, pointing the victim to a Google Cloud Storage link that final results in the download of a compressed ISO file, therefore continuing the aforementioned an infection sequence.
The changeover from BazarLoader to Bumblebee is further evidence that these threat actors — very likely first accessibility brokers who infiltrate targets and then promote that accessibility to many others — are acquiring the malware from a widespread source, whilst also signaling a departure immediately after the Conti group’s attack toolkit became public information all-around the similar time.
The enhancement also overlaps with Conti having about the notorious TrickBot botnet and shutting it down to concentration on the advancement of BazarLoader and Anchor malware. It can be not quickly very clear if Bumblebee is the get the job done of TrickBot actors and no matter if the leaks prompted the gang to abandon BazaLoader in favor of an entirely new malware.
“The introduction of the Bumblebee loader to the crimeware danger landscape and its evident alternative for BazaLoader demonstrates the flexibility threat actors have to speedily shift TTPs and adopt new malware,” Sherrod DeGrippo, vice president of risk study and detection at Proofpoint, claimed.
“Moreover, the malware is really refined, and demonstrates staying in ongoing, energetic development introducing new techniques of evading detection,” DeGrippo added.
Discovered this write-up fascinating? Stick to THN on Facebook, Twitter and LinkedIn to go through additional exceptional articles we publish.
Some parts of this short article are sourced from:
thehackernews.com


 Global Security Spending Set to Hit $198bn by 2025
Global Security Spending Set to Hit $198bn by 2025