You’ve been asked for a Vulnerability Evaluation Report for your organisation and for some of you examining this write-up, your 1st believed is most likely to be “What is that?”
Stress not. This short article will solution that really concern as very well as why you require a Vulnerability Assessment Report and wherever you can get 1 from.
As it is probable the ask for for this kind of a report came from an important source these as the Board, a companion, a shopper or an auditor, there is not a moment to squander. So let’s drive straight in.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
What is a Vulnerability Evaluation Report and why do you have to have one?
A Vulnerability Evaluation Report is only a document that illustrates how you are taking care of your organisation’s vulnerabilities. It can be crucial for the reason that, with tens of hundreds of new technology flaws currently being uncovered every single calendar year, you require to be capable to establish that your organisation does its finest to keep away from attack if you want to be trustworthy by associates and buyers.
A greatest security exercise suggested by governments throughout the entire world, a vulnerability assessment is an automated overview system that supplies insights into your recent security condition. The vulnerability evaluation report is the final result of this assessment. Utilised as a roadmap to a far better condition of security preparedness, it lays out the exclusive pitfalls your organisation is up versus owing to the technology you use, and reveals how very best to defeat them with minimum disruption to your core small business technique and functions.
The assistance it supplies is obvious but why do you will need 1? As outlined over, it is probably you had been requested for a Vulnerability Assessment Report by the Board, a companion, a client or an auditor as every of these groups desires reassurance that you happen to be on prime of any weaknesses in your infrastructure. Here’s why:
— Clients need to believe in you
Weaknesses in your IT devices could have an affect on your customers’ functions. With source chain attacks on the increase, a vulnerability in a solitary organization could depart the full assortment of organizations paralysed, as demonstrated by the notorious SolarWinds hack last 12 months.
It does not issue how compact your organization is if your buyers will be entrusting you with any of their knowledge, they may perhaps want for a Vulnerability Evaluation Report very first to affirm that your IT security practices are tiptop.
— The Board wants a improved comprehension of the business’ risk
Cyber security is a growing problem across several organizations, so likelihood are your board users want to take a improved grip of their risk, ahead of the lack of insights into vulnerabilities is turned into a a great deal far more major organization challenge. With ransomware attacks often generating headlines, obtaining appropriate vulnerability management in spot and presenting an “all obvious” report, can give your enterprise heads that necessary peace of mind.
— Your auditors are examining for compliance
Quite a few of the regulatory or compliance frameworks relevant to security and privacy, like SOC2, HIPAA, GDPR, ISO 27001, and PCI DSS, advise or outright require standard compliance scans and reporting, so if the ask for for a vulnerability assessment report was designed by your auditor, it is very likely to be for compliance purposes.
— Your CFO is renewing your cyber insurance policies
It could be the situation that your coverage supplier is in search of a vulnerability evaluation report as component of the underwriting process. If you will not want to run the risk of becoming denied your insurance policies payment or would not like to see your premiums increase, then you could benefit from supplying these studies frequently.
How often do you need to create a vulnerability assessment report?
Often. Consider of it like vulnerability scanning: For optimum efficacy, you have to have to carry out common, if not consistent, in depth evaluations of your entire technology stack, in any other case you could pass up anything that could deliver your small business to a high priced halt.
Cybercriminals do not stop exploring right until they discover some thing they can get benefit of. You need to scan your techniques continually and have up to date reporting to replicate your vigilance as and when it is really required.
Contemporary vulnerability scanning answers, like Intruder, will give you a cyber cleanliness score which enables you to monitor the progress of your vulnerability management attempts above time, proving that your security issues are currently being consistently solved in fantastic time.
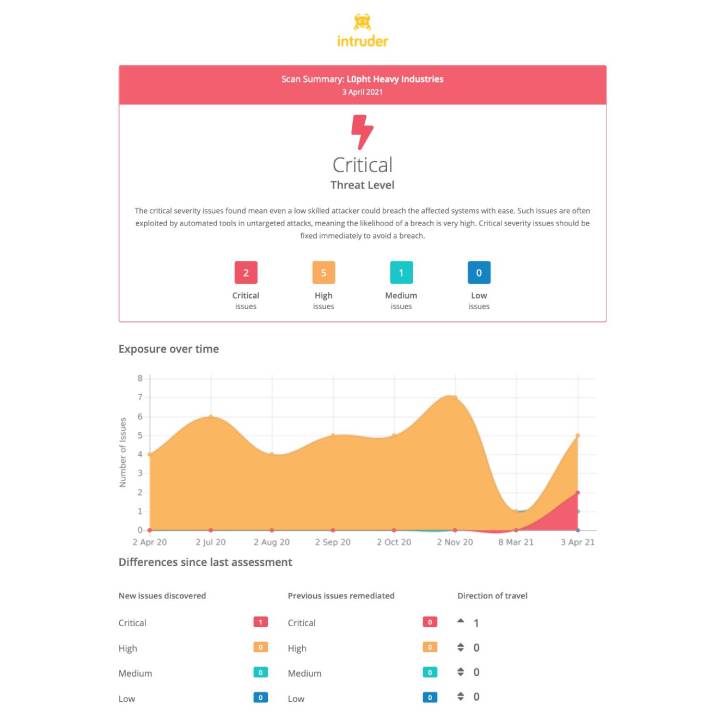 A vulnerability assessment report from Intruder, to offer evidence to your customers or regulators that a vulnerability scanning course of action is in spot.
A vulnerability assessment report from Intruder, to offer evidence to your customers or regulators that a vulnerability scanning course of action is in spot.
What should be involved in a vulnerability assessment report?
Regretably, there isn’t a a single dimensions fits all report. Whilst the contents are generally the amount of vulnerabilities detected in your programs at a issue in time, your various stakeholders will require varying stages of detail. Even for compliance uses, vulnerability evaluation reporting specifications can vary.
As a good rule of thumb, we advise creating an Executive Report made up of graph sights and composite cyber cleanliness scores for the Board and C-Suite that clue them in on wherever they stand at any specified second. And for your IT crew, their report wants increased detail these as how to utilize the suitable alternatives to existing issues and sidestep subsequent errors.
Exactly where can you get a Vulnerability Evaluation Report from?
Making certain your Vulnerability Evaluation Experiences consist of all the factors and information your stakeholders need can consider a whole lot of function and knowledge which can distract your security groups from other routines that will maintain your organisation safe. That is why it truly is proposed to choose an external company to create your reviews.
In advance of you start off evaluating individual suppliers, make certain you have a strong comprehension of your specialized atmosphere and of the precise results that the vulnerability assessment should existing. This is because vulnerability evaluation tools are not crafted the very same they verify for unique kinds of weaknesses, so you need to choose the solution that ideal satisfies your specifications. Look at the capabilities and checks you may need, as perfectly as the sector standards you will need to stick to and your spending plan.
Two crucial aspects to think about relate to reporting: for starters, how versatile the assessment supplier will be with how significantly detail is introduced (particularly if you have to have to current details to different audiences) and next, how obviously the benefits are communicated. Scanning success can be mind-boggling but the appropriate vendor will demystify sophisticated security facts to grant you a apparent, jargon-cost-free knowing of the dangers you facial area.
At Intruder, stories are built to be nicely-understood, although also preserving all the complex element expected by IT managers and DevOps groups. Regardless of whether you might be a enormous company or a fledgling startup, you can create swift reviews, generate compliance paper trails, stay secure, and talk with staff members and likely investors. Intruder delivers a free trial of its software, which you can activate in this article. Get vulnerability evaluation reporting in put now.
Located this short article fascinating? Adhere to THN on Fb, Twitter and LinkedIn to browse additional exceptional material we submit.
Some parts of this report are sourced from:
thehackernews.com


 Cybercriminals Using New Malware Loader ‘Bumblebee’ in the Wild
Cybercriminals Using New Malware Loader ‘Bumblebee’ in the Wild