A cyberespionage risk actor acknowledged for targeting a wide variety of critical infrastructure sectors in Africa, the Middle East, and the U.S. has been observed utilizing an upgraded model of a distant entry trojan with data thieving abilities.
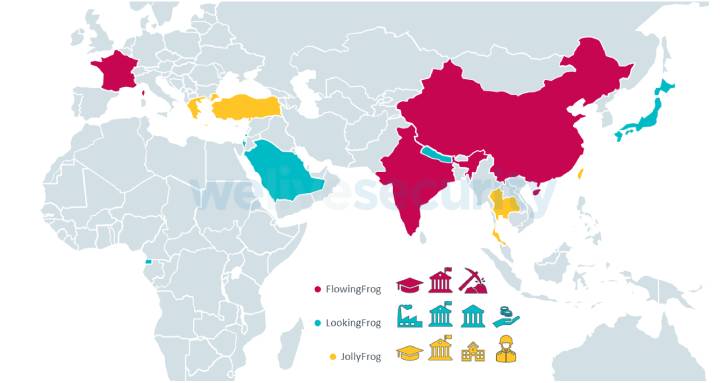
Contacting TA410 an umbrella team comprised of three teams dubbed FlowingFrog, LookingFrog and JollyFrog, Slovak cybersecurity firm ESET assessed that “these subgroups function somewhat independently, but that they may share intelligence specifications, an obtain crew that operates their spear-phishing campaigns, and also the group that deploys network infrastructure.”
TA410 — mentioned to share behavioral and tooling overlaps with APT10 (aka Stone Panda or TA429) — has a background of targeting U.S-centered corporations in the utilities sector as nicely as diplomatic entities in the Middle East and Africa.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Other victims of the hacker collective involve a production company in Japan, a mining business enterprise in India, and a charity in Israel, in addition to unnamed victims in the education and armed service verticals.
TA410 was initially documented by Proofpoint in August 2019 when the threat actor unleashed phishing strategies made up of macro-laden paperwork to compromise utility providers across the U.S. with a modular malware identified as LookBack.
Almost a 12 months later on, the team returned with a new backdoor codenamed FlowCloud, also shipped to U.S. utilities providers, that Proofpoint explained as malware that provides attackers complete manage about contaminated techniques.
“Its remote accessibility trojan (RAT) features involves the means to accessibility put in apps, the keyboard, mouse, display screen, data files, providers, and processes with the capability to exfiltrate details by way of command-and-control,” the firm noted in June 2020.
Industrial cybersecurity business Dragos, which tracks the exercise group less than the moniker TALONITE, pointed out the group’s penchant for blending approaches and tactics in purchase to ensure a effective intrusion.
“TALONITE focuses on subverting and getting gain of belief with phishing lures focusing on engineering-particular themes and concepts, malware that abuses normally respectable binaries or modifies this sort of binaries to contain more performance, and a mix of owned and compromised network infrastructure,” Dragos stated in April 2021.
ESET’s investigation into the hacking crew’s modus operandi and toolset has get rid of light on a new edition of FlowCloud, which will come with the means to report audio utilizing a computer’s microphone, observe clipboard events, and handle hooked up digital camera units to choose shots.
Exclusively, the audio recording purpose is developed to be routinely induced when audio stages in close proximity to the compromised computer system cross a 65-decibel threshold.
TA410 is also recognised to acquire benefit of each spear-phishing and vulnerable internet-facing applications this kind of as Microsoft Trade, SharePoint, and SQL Servers to achieve initial accessibility.

“This indicates to us that their victims are focused particularly, with the attackers selecting which entry system has the greatest likelihood of infiltrating the goal,” ESET malware researcher Alexandre Côté Cyr said.
Each team in just the TA410 umbrella is explained to use unique toolsets. Whilst JollyFrog depends on off-the-shelf malware such as QuasarRAT and Korplug (aka PlugX), LookingFrog takes advantage of X4, a barebones implant, and LookBack.
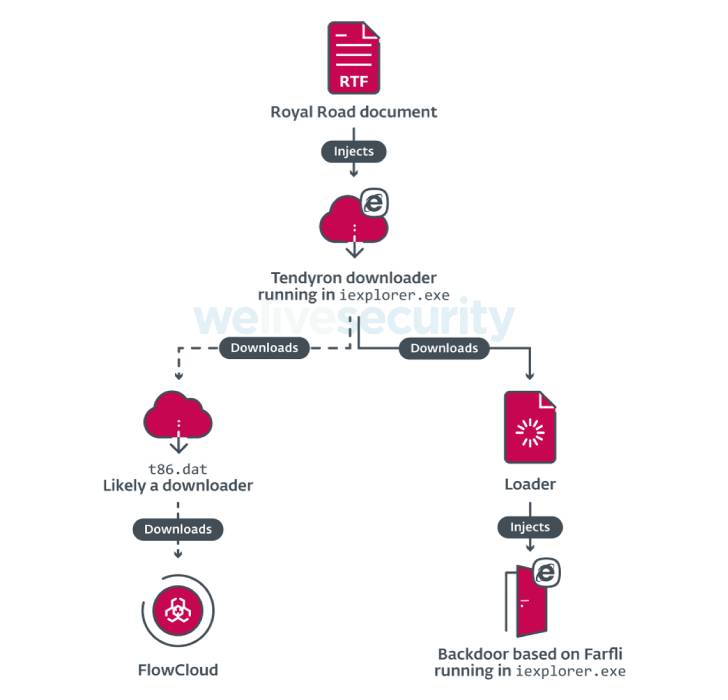
FlowingFrog, in distinction, employs a downloader identified as Tendyron that’s delivered by suggests of the Royal Street RTF weaponizer, utilizing it to down load FlowCloud as properly as a 2nd backdoor, which is dependent on Gh0stRAT (aka Farfli).
“TA410 is a cyberespionage umbrella concentrating on higher-profile entities these types of as governments and universities around the globe,” ESET claimed. “Even however the JollyFrog team utilizes generic tools, FlowingFrog and LookingFrog have entry to intricate implants these kinds of as FlowCloud and LookBack.”
Observed this write-up intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to examine extra exceptional articles we put up.
Some elements of this report are sourced from:
thehackernews.com



 Everything you need to know to create a Vulnerability Assessment Report
Everything you need to know to create a Vulnerability Assessment Report