A new DNS menace actor dubbed Savvy Seahorse is leveraging refined procedures to entice targets into fake investment decision platforms and steal funds.
“Savvy Seahorse is a DNS menace actor who convinces victims to create accounts on fake financial commitment platforms, make deposits to a own account, and then transfers individuals deposits to a lender in Russia,” Infoblox stated in a report posted past week.
Targets of the campaigns include things like Russian, Polish, Italian, German, Czech, Turkish, French, Spanish, and English speakers, indicating that the risk actors are casting a large net in their attacks.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Consumers are lured by means of advertisements on social media platforms like Fb, although also tricking them into parting with their own data in return for alleged large-return investment alternatives through bogus ChatGPT and WhatsApp bots.

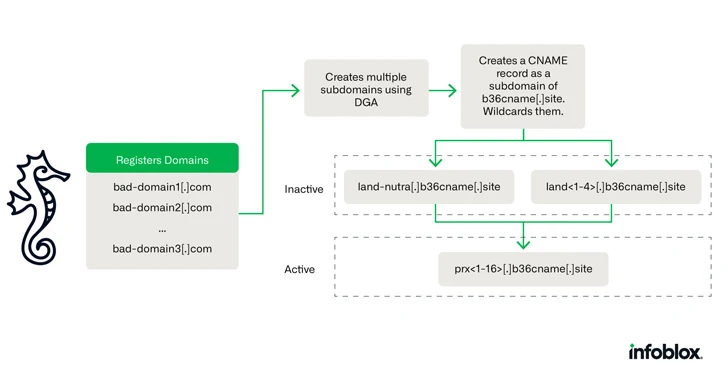
The economic fraud campaigns are noteworthy for making use of DNS canonical title (CNAME) records to build a targeted visitors distribution method (TDS), thereby allowing for danger actors to evade detection considering the fact that at least August 2021.
A CNAME record is made use of to map a domain or subdomain to yet another domain (i.e., an alias) in its place of pointing to an IP tackle. A person benefit with this tactic is that when the IP address of the host alterations, only the DNS A document for the root domain wants to be up to date.
Savvy Seahorse leverages this strategy to its edge by registering quite a few shorter-lived subdomains that share a CNAME record (and hence an IP handle). These particular subdomains are developed working with a area generation algorithm (DGA) and are associated with the key campaign domain.
The at any time-changing character of the domains and IP addresses also tends to make the infrastructure resistant to takedown endeavours, making it possible for the danger actors to continuously create new domains or alter their CNAME data to a different IP handle as their phishing websites are disrupted.
Although danger actors like VexTrio have employed DNS as a TDS, the discovery marks the 1st time CNAME information have been employed for such applications.

Victims who stop up clicking the links embedded on Facebook adverts are urged to present their names, email addresses, and phone quantities, after which they are redirected to the bogus investing system for introducing resources to their wallets.
“An vital element to notice is the actor validates the user’s facts to exclude site visitors from a predefined checklist of nations, which include Ukraine, India, Fiji, Tonga, Zambia, Afghanistan, and Moldova, though their reasoning for deciding upon these distinct nations around the world is unclear,” Infoblox pointed out.
The enhancement comes as Guardio Labs revealed that hundreds of domains belonging to reputable brands and establishments have been hijacked applying a system known as CNAME takeover to propagate spam strategies.
Observed this report attention-grabbing? Follow us on Twitter and LinkedIn to examine far more distinctive written content we post.
Some pieces of this post are sourced from:
thehackernews.com

 Over 225,000 Compromised ChatGPT Credentials Up for Sale on Dark Web Markets
Over 225,000 Compromised ChatGPT Credentials Up for Sale on Dark Web Markets