Startups and scales-ups are normally cloud-first organizations and not often have sprawling legacy on-prem environments. Likewise, knowing the agility and adaptability that cloud environments present, the mid-industry is predominantly running in a hybrid point out, partly in the cloud but with some on-prem assets.
While there has been a bit of a backswing in opposition to the pricing and lock-in presented when utilizing cloud infrastructure, cloud is however the preferred supplier for the the greater part of SMBs.
As a consequence, external attack surfaces are progressively advanced and distributed and, consequently, more difficult to keep an eye on and secure. This expanded attack surface area gives hackers plenty of blind spots and gaps to exploit. Security teams are on the back again, reacting, often way too slowly, to alterations in their have attack floor as engineering groups consistently spin up and expose new systems, companies, and information to the internet.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This is compounded by the point that the threat landscape is constantly shifting. 1000’s of new vulnerabilities are discovered each thirty day period, like vulnerabilities that allow for an attacker to attain complete handle above devices that have to be internet-struggling with and are intended to aid security teams or facilitate protected connections (consider the spate of Citrix and Ivanti vulnerabilities that have not long ago emerged). How can you respond to a new critical vulnerability that is currently being exploited by ransomware gangs if you will not even know if your firm is utilizing that technology and exposing it to the internet?
A single of the motives that security groups battle is since procedures are reactive and knowledge about the organization’s attack surface is siloed in the heads of those folks who are spinning up those people cloud techniques. Security groups depend on a sprawl of methods that create hundreds of fragmented details which is hard to realize, prioritize, and choose action. This is the place publicity administration suits in as an extension of exterior attack floor administration.
What is publicity administration in cybersecurity?
As environments evolve and become a lot more advanced, so do the tools and techniques necessary to safe and guard them. Publicity administration aims to cut down that complexity by supplying you visibility of all points in just your attack surface area that an attacker could use to breach your firm and eventually pose a risk to the small business.
Exposure administration aims to deliver a prioritized list of exposures, with context for each individual so that you can make an educated final decision on what to deal with first and how to deal with it to minimize your enterprise risk.
“Companies who put into practice a constant exposure management system will be 3 instances much less probable to be breached by 2026” (Gartner)
Publicity administration can also assist improve visibility of your whole attack floor, together with facts belongings these kinds of as code repositories like GitHub and GitLab, so you can additional properly locate alternatives for an attacker and shut them down just before they pose too good of a risk to your organization.
This signifies you can improved comprehend the threats you encounter, and prioritize the attacks that are not just more possible, but extra critical. At a time when security teams are confused with facts – around 25,000 vulnerabilities were being published in 2022, and we observed that boost to around 26,500 in 2023 – getting a apparent photo of in which to aim your time and effort is turning into important.
Publicity administration vs attack surface area management
Although both equally have the exact same purpose, there are essential distinctions concerning the two. External Attack Area Administration (ASM) is the ongoing method of finding and determining property which can be found by an attacker on the internet, displaying in which security gaps exist, where by they can be employed to carry out an attack, and where defenses are potent ample to repel an attack. If you can scan for it working with vulnerability scanning then it generally falls inside of attack surface management.
Publicity administration will take this a move additional to include facts property, person identities, and cloud account configuration, which aids you realize your publicity and cut down it where essential.
Here the attack floor contains any of the SaaS goods you use. If 1 of these receives compromised or a single of your accounts in your SaaS provider receives compromised, they have facts that can be made use of to aid other attacks. So it shouldn’t be overlooked when evaluating risk to the small business.
Visualize and decrease your publicity with Intruder
Bear in mind what was reported about a huge attack surface becoming more difficult to defend? You can decrease yours by constantly monitoring for changes with an automatic vulnerability management tool like Intruder. Get entire management of your vulnerability management to:
- Find property: when new cloud services are spun up and uncovered to the internet, Intruder will kick off a scan to obtain any vulnerabilities so you can repair them faster
- Know what is actually exposed: get full visibility of your network perimeter, observe lively and unresponsive targets, discover modifications, check expiring certificates, and see any ports, solutions or protocols that should not be uncovered to the internet
- Detect more: Intruder takes advantage of several scanners to identify vulnerabilities and exposures throughout your attack floor providing you the biggest visibility
- Target on the significant issues: get effects prioritized primarily based on context, so you can concentrate on the most urgent problems devoid of squandering time sifting via the noise
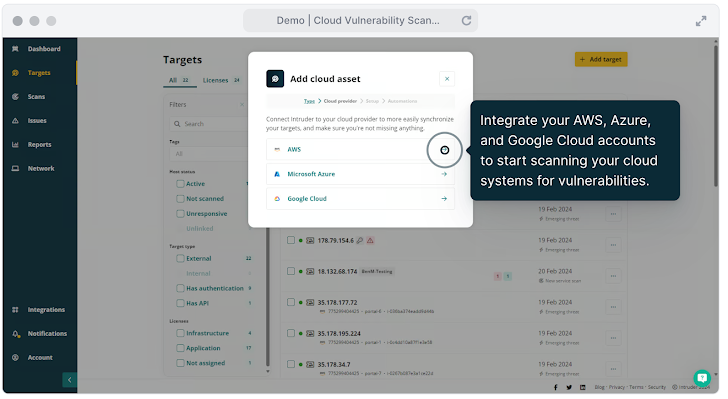 Intruder repeatedly displays and automatically scans your environments as new vulnerabilities emerge
Intruder repeatedly displays and automatically scans your environments as new vulnerabilities emerge
High quality and Vanguard prospects can also increase their publicity management with bug looking, exactly where Intruder’s testers look for the weaknesses and exposures that automatic scanners can miss. Get started with a 14-working day totally free trial nowadays.
Found this article interesting? Adhere to us on Twitter and LinkedIn to examine extra exceptional content material we publish.
Some components of this short article are sourced from:
thehackernews.com

 Cybercriminals Using Novel DNS Hijacking Technique for Investment Scams
Cybercriminals Using Novel DNS Hijacking Technique for Investment Scams