A reputable Windows resource used for developing program packages named Innovative Installer is staying abused by danger actors to fall cryptocurrency-mining malware on infected devices given that at the very least November 2021.
“The attacker makes use of State-of-the-art Installer to bundle other authentic application installers, this sort of as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, with destructive scripts and takes advantage of Innovative Installer’s Custom Actions feature to make the software program installers execute the destructive scripts,” Cisco Talos researcher Chetan Raghuprasad mentioned in a complex report.
The character of the applications trojanized signifies that the victims most likely span architecture, engineering, design, production, and enjoyment sectors. The program installers predominantly use the French language, a indication that French-speaking consumers are becoming singled out.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This marketing campaign is strategic in that these industries count on personal computers with higher Graphics Processing Unit (GPU) electricity for their day-to-working day functions, generating them rewarding targets for cryptojacking.

Cisco’s examination of the DNS request knowledge despatched to the attacker’s infrastructure exhibits that the victimology footprint spans France and Switzerland, followed by sporadic bacterial infections in the U.S., Canada, Algeria, Sweden, Germany, Tunisia, Madagascar, Singapore, and Vietnam.
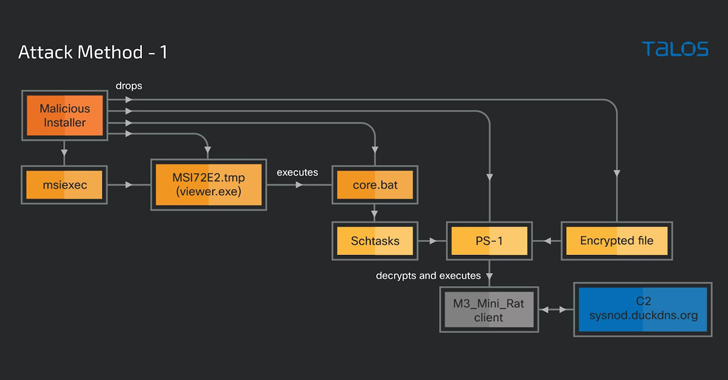
The attacks culminate in the deployment of an M3_Mini_Rat, a PowerShell script that very likely functions as a backdoor to download and execute supplemental threats, as properly as several cryptocurrency-mining malware families these types of as PhoenixMiner and lolMiner.
As for the preliminary access vector, it truly is suspected that search motor optimization (Web optimization) poisoning strategies may have been utilized to deliver the rigged software installers to the victim’s devices.

The installer, at the time released, activates a multi-phase attack chain that drops the M3_Mini_Rat client stub and the miner binaries.
“M3_Mini_Rat customer is a PowerShell script with distant administration capabilities that mostly focuses on carrying out program reconnaissance and downloading and executing other destructive binaries,” Raghuprasad stated.
The trojan is designed to speak to a remote server, even though it’s at the moment unresponsive, building it difficult to identify the exact character of malware that could have been dispersed as a result of this approach.
Approaching WEBINARWay Too Vulnerable: Uncovering the State of the Identity Attack Surface area
Achieved MFA? PAM? Company account defense? Locate out how very well-equipped your group definitely is from identification threats
Supercharge Your Abilities
The two other malicious payloads are employed to illicitly mine cryptocurrency using the machine’s GPU assets. PhoenixMiner is an Ethereum cryptocurrency-mining malware, although lolMiner is an open up-resource mining software program that can be used to mine two virtual currencies at the exact same time.
In yet a further situation of reputable instrument abuse, Look at Issue is warning of a new form of phishing attack that leverages Google Looker Studio to generate bogus cryptocurrency phishing web pages in an endeavor to sidestep protections.
“Hackers are making use of it to create phony crypto internet pages that are made to steal funds and credentials,” security researcher Jeremy Fuchs said.
“This is a very long way of saying that hackers are leveraging Google’s authority. An email security assistance will glance at all these things and have a excellent deal of self confidence that it is not a phishing email, and that it will come from Google.”
Discovered this post attention-grabbing? Comply with us on Twitter and LinkedIn to go through extra unique material we submit.
Some areas of this post are sourced from:
thehackernews.com

 U.K. and U.S. Sanction 11 Russia-based Trickbot Cybercrime Gang Members
U.K. and U.S. Sanction 11 Russia-based Trickbot Cybercrime Gang Members