Cybersecurity researchers have printed the interior workings of a new wiper known as Azov Ransomware which is deliberately created to corrupt facts and “inflict impeccable problems” to compromised programs.
Distributed as a result of an additional malware loader acknowledged as SmokeLoader, the malware has been described as an “effective, rapidly, and however unrecoverable facts wiper,” by Israeli cybersecurity enterprise Examine Point. Its origins have yet to be identified.
The wiper program is established to overwrite a file’s contents in alternating 666-byte chunks with random sounds, a technique referred to as intermittent encryption which is staying more and more leveraged by ransomware operators to evade detection and encrypt victims’ data files more rapidly.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“One factor that sets Azov aside from your back garden-range ransomware is its modification of specified 64-little bit executables to execute its personal code,” menace researcher Jiří Vinopal stated. “The modification of executables is finished making use of polymorphic code, so as not to be perhaps foiled by static signatures.”
Azov Ransomware also incorporates a logic bomb – a established of problems that ought to be fulfilled prior to activating a destructive motion – to detonate the execution of the wiping and backdooring capabilities at a predetermined time.
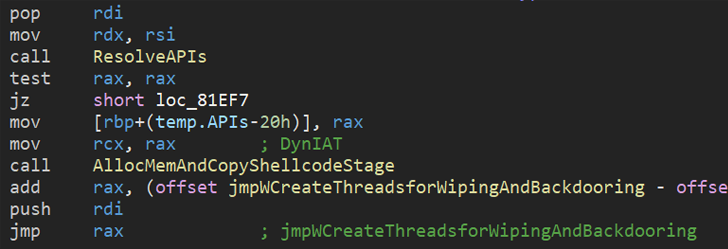
“Even though the Azov sample was thought of skidsware when very first encountered […], when probed more a single finds really state-of-the-art approaches — manually crafted assembly, injecting payloads into executables in get to backdoor them, and a number of anti-analysis tricks usually reserved for security textbooks or higher-profile model-title cybercrime resources,” Vinopal additional.
The improvement will come amid a profusion of damaging wiper attacks given that the start out of the calendar year. This involves WhisperGate, HermeticWiper, AcidRain, IsaacWiper, CaddyWiper, Industroyer2, DoubleZero, RURansom, and CryWiper.
Very last week, security business ESET disclosed a further previously unseen wiper known as Fantasy that’s unfold utilizing a provide chain attack concentrating on an Israeli software program business to concentrate on prospects in the diamond industry. The malware has been linked to a risk actor called Agrius.
Uncovered this posting exciting? Follow us on Twitter and LinkedIn to study much more exceptional material we post.
Some parts of this post are sourced from:
thehackernews.com


 Malware Strains Targeting Python and JavaScript Developers Through Official Repositories
Malware Strains Targeting Python and JavaScript Developers Through Official Repositories