An lively malware campaign is targeting the Python Package Index (PyPI) and npm repositories for Python and JavaScript with typosquatted and faux modules that deploy a ransomware pressure, marking the newest security issue to have an impact on software provide chains.
The typosquatted Python deals all impersonate the well known requests library: dequests, fequests, gequests, rdquests, reauests, reduests, reeuests, reqhests, reqkests, requesfs, requesta, requeste, requestw, requfsts, resuests, rewuests, rfquests, rrquests, rwquests, telnservrr, and tequests.
In accordance to Phylum, the rogue deals embed supply code that retrieves Golang-dependent ransomware binary from a distant server depending on the victim’s operating process and microarchitecture.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

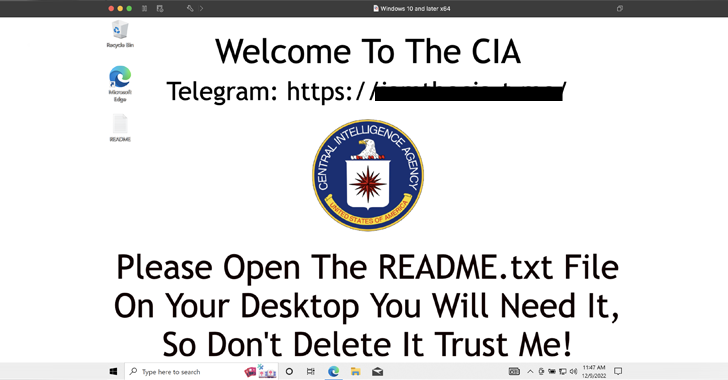
Thriving execution causes the victim’s desktop background to be changed to an actor-controlled image that statements to the U.S. Central Intelligence Company (CIA). It can be also made to encrypt files and need a $100 ransom in cryptocurrency.
In a indicator that the attack is not restricted to PyPI, the adversary has been noticed publishing five unique modules in npm: discordallintsbot, discordselfbot16, discord-all-intents-bot, discors.jd, and telnservrr.
“The attacker has also revealed many npm packages that behave in a very similar method,” Phylum CTO Louis Lang explained, adding just about every of the libraries consist of the JavaScript equal of the exact code to deploy the ransomware.
The conclusions come as ReversingLabs uncovered a tranche of 10 added PyPI offers pushing modified versions of the W4SP Stealer malware as section of an ongoing source chain attack aimed at software program builders which is considered to have begun around September 25, 2022.
That’s not all. Earlier this month, Israel-centered application provide chain security firm Legit Security demonstrated a new attack procedure versus a Rust repository (“rust-lang”) that abuses GitHub Actions to poison authentic artifacts.
Establish artifacts are the files made by the create procedure, this kind of as distribution deals, WAR documents, logs, and stories. By changing the precise modules with trojanized versions, an actor could steal sensitive info or deliver more payloads to all its downstream people.
“The vulnerability was located in a workflow named ‘ci.yml’ which is liable for setting up and screening the repository’s code,” Legit Security researcher Noam Dotan explained in a technical generate-up.
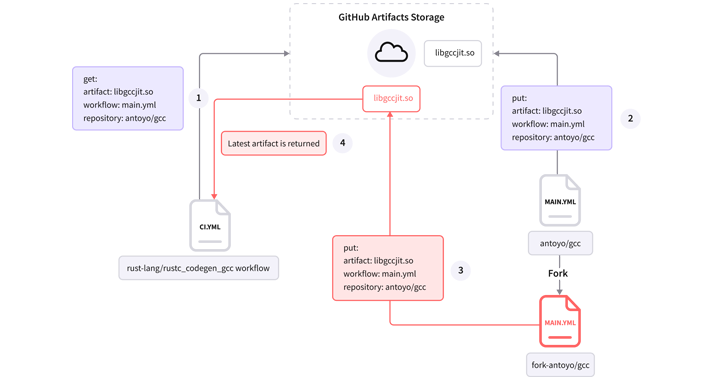
By exploiting this weak point, an attacker could trick the GitHub workflow into executing a malware-laced artifact, proficiently making it feasible to tamper with repository branches, pull requests, issues, and releases.
The maintainers of the Rust programming language dealt with the issue on September 26, 2022, pursuing responsible disclosure on September 15, 2022.
Uncovered this short article interesting? Adhere to us on Twitter and LinkedIn to go through a lot more special articles we submit.
Some areas of this article are sourced from:
thehackernews.com

 Fortinet Warns of Active Exploitation of New SSL-VPN Pre-auth RCE Vulnerability
Fortinet Warns of Active Exploitation of New SSL-VPN Pre-auth RCE Vulnerability