Fortinet on Monday issued emergency patches for a extreme security flaw affecting its FortiOS SSL-VPN products that it stated is remaining actively exploited in the wild.
Tracked as CVE-2022-42475 (CVSS rating: 9.3), the critical bug relates to a heap-dependent buffer overflow vulnerability that could permit an unauthenticated attacker to execute arbitrary code by using specifically crafted requests.
The firm mentioned it can be “aware of an instance where by this vulnerability was exploited in the wild,” urging customers to shift rapidly to use the updates.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The following solutions are impacted by the issue –
- FortiOS version 7.2. by 7.2.2
- FortiOS model 7.. by 7..8
- FortiOS edition 6.4. by 6.4.10
- FortiOS model 6.2. by way of 6.2.11
- FortiOS-6K7K edition 7.. by 7..7
- FortiOS-6K7K variation 6.4. through 6.4.9
- FortiOS-6K7K model 6.2. as a result of 6.2.11
- FortiOS-6K7K version 6.. by 6..14
Patches are out there in FortiOS versions 7.2.3, 7..9, 6.4.11, and 6.2.12 as very well as FortiOS-6K7K variations 7..8, 6.4.10, 6.2.12, and 6..15.
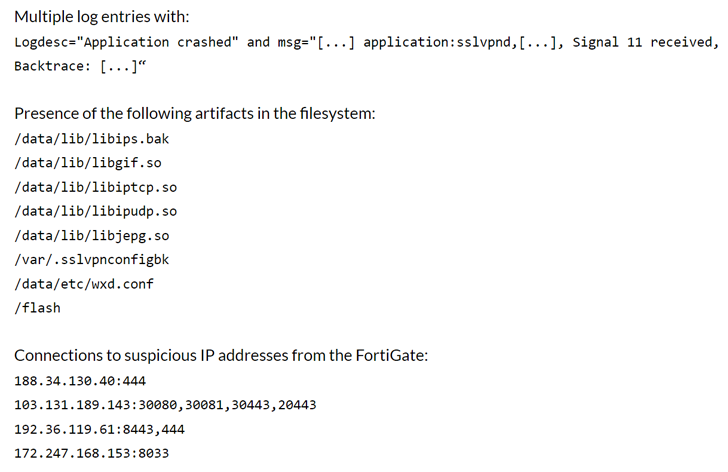
The American network security business has also posted indicators of compromise (IoCs) affiliated with the exploitation attempts, like the IP addresses and the artifacts that are current in the file system article a successful attack.
The advisory arrives two months after Fortinet warned of energetic weaponization of one more critical authentication bypass bug in FortiOS, FortiProxy, and FortiSwitchManager (CVE-2022-40684, CVSS rating: 9.6).
Discovered this article attention-grabbing? Stick to us on Twitter and LinkedIn to browse a lot more exclusive articles we put up.
Some elements of this article are sourced from:
thehackernews.com


 HSE Cyber-Attack Costs Ireland $83m So Far
HSE Cyber-Attack Costs Ireland $83m So Far