The Internet of Factors (IoT) is transforming efficiency in different sectors like health care and logistics but has also launched new security challenges, specially IoT-pushed DDoS attacks. This short article explores how these attacks function, why they’re uniquely problematic, and how to mitigate them.
What Is IoT?
IoT (Internet of Issues) refers to on the internet, interconnected products that gather and exchange information. This broad category of gadgets consists of sensors, cameras, network routers, and state-of-the-art equipment, and their integration into day-to-day daily life and work procedures outcomes in an ecosystem that can automate functions, strengthen decision-producing, and greatly enhance consumer practical experience.
IoT: A Breeding Ground for Botnets
IoT’s speedy adoption amplifies its vulnerability, as improperly secured products turn into quick prey for attackers and could become portion of a botnet. Managed by attackers, botnets can scale and rapidly execute numerous attacks, including DDoS, data theft, ad fraud, cryptocurrency mining, spam and phishing, data harvesting, and snooping—without system owners’ information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Why are IoT Botnets a Increasing Worry?
Botnets are absolutely nothing new, but IoT botnets pose a precise risk. The quantity of IoT gadgets attained 16 billion in 2022 and is envisioned to exceed 30 billion by 2025. These units typically go through from infrequent updates or insecure default configurations, or are basically left unattended, generating them significantly less protected than classic personal computers and are at risk of currently being hijacked with relative ease to form potent botnets.
The scale and complexity of IoT-pushed attacks are set to increase owing to their expanding use. Among these pitfalls, distributed denial-of-assistance (DDoS) attacks stand out as specifically hard to mitigate. The distributed nature of IoT gadgets renders them perfect platforms for these attacks, building it complicated to recognize and block destructive targeted visitors and thereby compounding the problems of DDoS mitigation.
Anatomy of IoT-Pushed botnet DDoS Attacks
Let’s discuss how IoT DDoS attacks happen and how new IoT products join the ranks of bots.
How Are IoT DDoS Attacks Released?
There are numerous crucial entities involved in a DDoS botnet attack:
- The attacker is the man or woman who controls the botnet. They are also known as the bot herder or botmaster.
- A command-and-command (C&C) server is a computer controlled by the attacker and utilised to connect with the infected equipment. The C&C orchestrates the botnet’s actions, sending out global instructions for tasks like initiating an attack or scanning a new device for vulnerabilities.
- A botnet is a network of gadgets that have been infected with malware and are controlled by a single attacker.
- The sufferer or target is the concentrate of a particular botnet-driven attack.
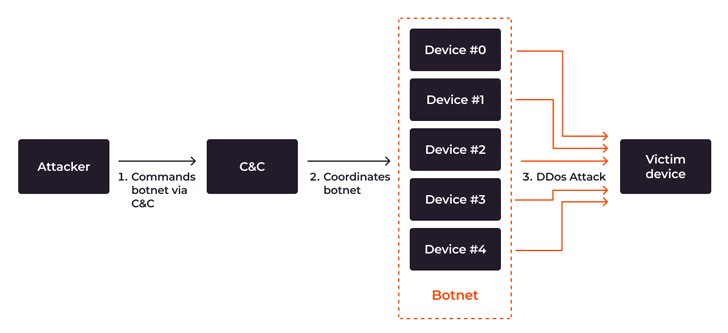 DDoS botnet assault flow from attacker’s command to DDoS attack
DDoS botnet assault flow from attacker’s command to DDoS attack
The attack approach is relatively uncomplicated:
When the botnet floods the focus on with abnormal requests, assistance failures manifest which jeopardize the availability of the specific system and even set the integrity of the whole infrastructure at risk. When aimed against crucial infrastructures this sort of as health care or transportation, the hazards go outside of monetary and reputational harm to endangering people’s life.
Incorporating IoT Products into Botnets
IoT devices that are unpatched, unattended, or misconfigured, or are now beneath botnet DDoS attack, are at risk of becoming included into a botnet. To expand the botnet, an attacker hacks new IoT equipment. This process requires two entities: the botnet itself and the loader server, a exclusive server that infects other products.
In brief, the process goes like this: The botnet hacks the unit and gains accessibility, and then the loader server installs malware on it. The attacker then gains permanent access to the machine and attaches it to the botnet. Here are the levels of infecting IoT products and connecting them to a botnet based mostly the Mirai circumstance:
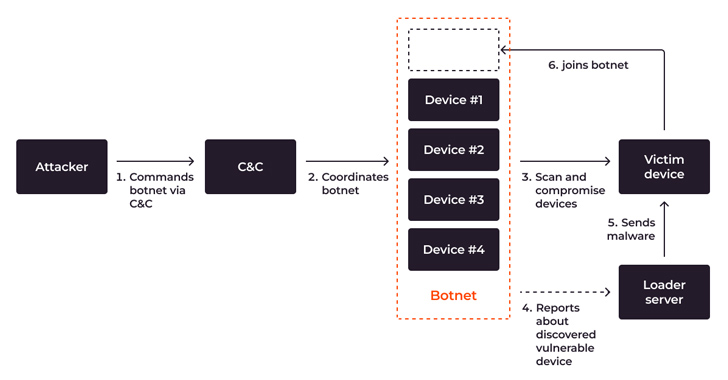 System stream, demonstrating scanning, compromising, infecting and joining a new device to a botnet
System stream, demonstrating scanning, compromising, infecting and joining a new device to a botnet
Highly developed botnets can self-propagate, compromising much more units autonomously, bringing extra and a lot more devices into the botnet, growing the botnet’s size and amplifying the scale of long run attacks.
How Risky Is the Present-day IoT DDoS Menace?
IoT-driven DDoS attacks greater by 300% in the to start with 50 percent of 2023 alone, leading to an believed worldwide money loss of $2.5 billion. In 2023, 90% of intricate, multi-vector DDoS attacks were centered on botnets. The development exhibits no symptoms of slowing down: the quantity of IoT units engaged in botnet-driven DDoS attacks rose from close to 200,000 a 12 months back to close to 1 million units, although there are two times as several vulnerabilities currently being targeted by botnet malware.
Overall, DDoS attack capability is on the increase. In accordance to Gcore’s Radar 2023, the prime electrical power of a singular DDoS attack arrived at a staggering 800 Gbps in the 1st 50 percent of 2023. Just two several years before, it peaked at 300 Gbps. Even though most attacks hit 1–2 Tbps speeds, the most potent can arrive at 100 Tbps.
Alarming Projections for 2023–2024
We are witnessing a important enhance in distinct DDoS attack vectors, such as UDP reflection and HTTP request flooding, generally focusing on the technology and financial industries. Sectors heavily reliant on on line services and authentic-time info processing are the most beautiful targets, facing quick economic losses and long-term reputational problems.
IoT’s development, whilst driving innovation, also provides alarming potential trends in cybersecurity: it fuels innovation but also raises major cybersecurity concerns. With an expected 18% progress in IoT devices to 14.4 billion in 2023, and a projected boost to 27 billion by 2025, gurus foresee a corresponding surge in botnet attacks. With both of those IoT and DDoS on the increase, IoT DDoS are posed to turn out to be an significantly significant threat in the rapid long run.
Defensive Measures: Techniques and Best Tactics
The increase of extra refined and impressive attacks will make fast focus to security critical. Here is how a variety of stakeholders can lead to a more secure digital ecosystem:
1. Safeguard your IoT from being contaminated.
- Teach on protected IoT practices: Encourage house and corporate customers to adjust default passwords, update firmware, and adhere to best techniques to avert devices from becoming compromised. Lots of businesses, like SANS Institute, give schooling on IoT security and penetration testing.
- Collaborate and menace share: Initiatives like the Cyber Danger Alliance and the Joint Cyber Protection Collaborative unite governments, tech businesses, and cybersecurity companies to quickly detect and neutralize rising threats, strengthening collective international defenses.
- Regularly update devices: Guarantee IoT products are up to date with the latest firmware and patches to avoid identified vulnerabilities from currently being exploited.
2. Safeguard in opposition to IoT-driven botnet DDoS attacks.
- Apply multi-layer security protocols: Deploy a in depth security system, from firewalls and intrusion detection techniques to web software security solutions.
- Invest in Specialised DDoS Defense Answers: Firms like Gcore have developed remedies explicitly created to combat even significant, IoT-pushed DDoS attacks. These DDoS protection solutions have been pivotal in lessening risks by leveraging genuine-time analytics.
Conclusion
The challenge of defending versus IoT-driven DDoS attacks is an ongoing fight. By knowing existing solutions, investing in specialised technologies like Gcore’s DDoS safety, and fostering a culture of vigilance and collaboration, you can drastically minimize organizational pitfalls and aid pave the way for a additional protected electronic landscape in the encounter of escalating threats.
Identified this post intriguing? Abide by us on Twitter and LinkedIn to go through more unique content material we put up.
Some elements of this write-up are sourced from:
thehackernews.com

 Cybercriminals Combine Phishing and EV Certificates to Deliver Ransomware Payloads
Cybercriminals Combine Phishing and EV Certificates to Deliver Ransomware Payloads