The menace actors guiding RedLine and Vidar information stealers have been observed pivoting to ransomware via phishing strategies that unfold first payloads signed with Extended Validation (EV) code signing certificates.
“This implies that the risk actors are streamlining functions by building their approaches multipurpose,” Trend Micro researchers stated in a new investigation revealed this week.
In the incident investigated by the cybersecurity firm, an unnamed victim is explained to have initial acquired a piece of data stealer malware with EV code signing certificates, adopted by ransomware using the similar supply method.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In the previous, QakBot infections have leveraged samples signed with valid code signing certificates to bypass security protections.
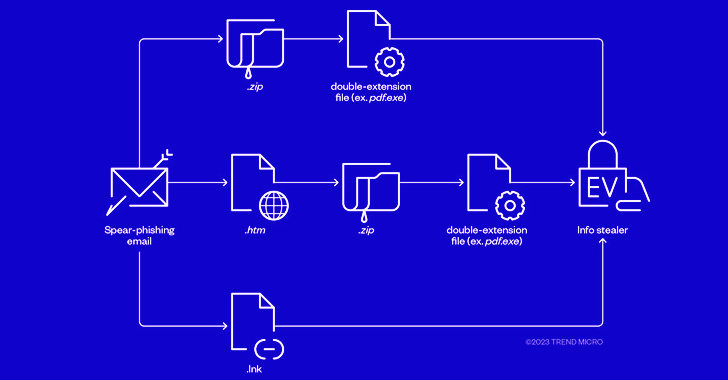
The attacks start out with phishing email messages that hire properly-worn lures to trick victims into managing malicious attachments that masquerade as PDF or JPG pictures but are essentially executables that leap-commence the compromise on working.

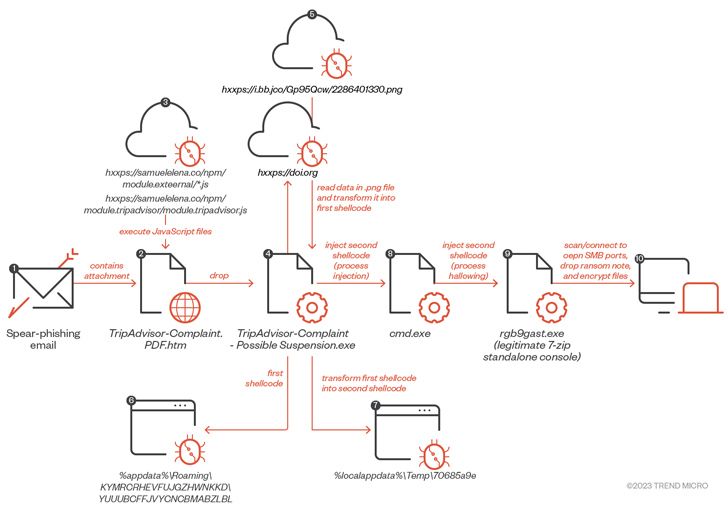
Whilst the campaign concentrating on the sufferer sent stealer malware in July, a ransomware payload designed its way in early August immediately after getting an email message that contains a bogus TripAdvisor criticism email attachment (“TripAdvisor-Complaint.pdf.htm”), triggering a sequence of actions that culminated in the deployment of ransomware.
“At this point, it is really worth noting that not like the samples of the data stealer we investigated, the data files utilised to fall the ransomware payload did not have EV certificates,” the researchers explained.
“Even so, the two originate from the exact menace actor and are spread utilizing the exact shipping approach. We can as a result believe a division of labor in between the payload provider and the operators.”
The development arrives as IBM X-Pressure found new phishing campaigns spreading an enhanced edition of a malware loader named DBatLoader, which was made use of as a conduit to distribute FormBook and Remcos RAR earlier this year.
DBatLoader’s new abilities facilitate UAC bypass, persistence, and course of action injection, indicating that it’s becoming actively maintained to drop malicious systems that can gather sensitive details and empower remote regulate of units.
The the latest established of attacks, detected given that late June, are engineered to also provide commodity malware these as Agent Tesla and Warzone RAT. A vast majority of the email messages have singled out English speakers, despite the fact that emails in Spanish and Turkish have also been spotted.
“In many observed campaigns the risk actors leveraged ample control around the email infrastructure to allow malicious e-mail to move SPF, DKIM, and DMARC email authentication methods,” the business mentioned.
“A the greater part of strategies leveraged OneDrive to phase and retrieve more payloads, with a little fraction if not making use of transfer[.]sh or new/compromised domains.”
Approaching WEBINARIdentity is the New Endpoint: Mastering SaaS Security in the Contemporary Age
Dive deep into the long term of SaaS security with Maor Bin, CEO of Adaptive Shield. Uncover why identity is the new endpoint. Protected your location now.
Supercharge Your Abilities
In related news, Malwarebytes exposed that a new malvertising campaign is concentrating on customers who are exploring for Cisco’s Webex movie conferencing application on search engines like Google to redirect them to a fake web page that propagates the BATLOADER malware.
BATLOADER, for its component, establishes make contact with with a remote server to down load a 2nd-phase encrypted payload, which is yet another known stealer and keylogger malware referred to as DanaBot.
A novel method adopted by the risk actor is the use of tracking template URLs as a filtering and redirection system to fingerprint and ascertain probable victims of desire. Readers who don’t fulfill the conditions (e.g., requests originating from a sandboxed environment) are directed to the genuine Webex internet site.
“Simply because the ads glimpse so reputable, there is little doubt individuals will click on on them and check out unsafe websites,” Jérôme Segura, director of threat intelligence at Malwarebytes, stated.
“The type of computer software becoming employed in people ads suggest that risk actors are intrigued in company victims that will offer them with qualifications handy for additional network ‘pentesting’ and, in some circumstances, ransomware deployment.”
Found this short article interesting? Comply with us on Twitter and LinkedIn to examine more unique content we submit.
Some elements of this posting are sourced from:
thehackernews.com

 Iranian Nation-State Actors Employ Password Spray Attacks Targeting Multiple Sectors
Iranian Nation-State Actors Employ Password Spray Attacks Targeting Multiple Sectors