Iranian nation-point out actors have been conducting password spray attacks in opposition to hundreds of corporations globally concerning February and July 2023, new results from Microsoft expose.
The tech huge, which is tracking the exercise underneath the name Peach Sandstorm (previously Holmium), stated the adversary pursued businesses in the satellite, protection, and pharmaceutical sectors to very likely facilitate intelligence assortment in help of Iranian condition interests.
Really should the authentication to an account be profitable, the threat actor has been noticed utilizing a combination of publicly obtainable and custom made applications for discovery, persistence, and lateral movement, adopted by info exfiltration in restricted conditions.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Peach Sandstorm, also identified by the names APT33, Elfin, and Refined Kitten, has been linked to spear-phishing attacks towards aerospace and electricity sectors in the earlier, some of which have entailed the use of the SHAPESHIFT wiper malware. It is claimed to be active because at the very least 2013.

“In the preliminary period of this campaign, Peach Sandstorm executed password spray campaigns from 1000’s of organizations throughout a number of sectors and geographies,” the Microsoft Danger Intelligence group mentioned, noting some of the exercise is opportunistic.
Password spraying refers to a technique whereby a destructive actor makes an attempt to authenticate to lots of distinct accounts utilizing a one password or a checklist of typically-utilised passwords. It can be various from brute-drive attacks in which a single account is qualified with lots of credential combinations.
“Action noticed in this marketing campaign aligned with an Iranian sample of daily life, particularly in late May perhaps and June, exactly where exercise happened practically solely amongst 9:00 AM and 5:00 PM Iran Conventional Time (IRST),” Microsoft further more additional.
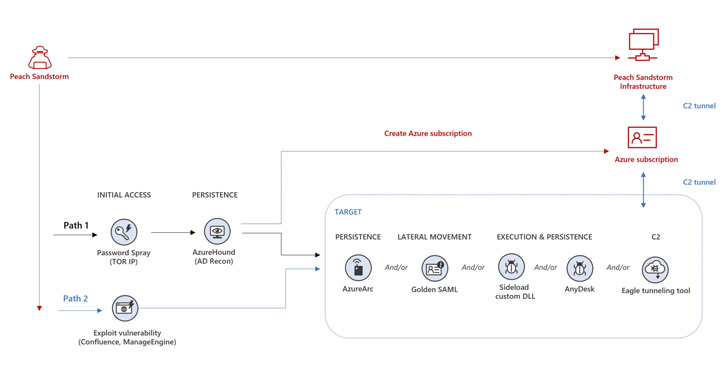
Intrusions are characterised by the use of open-resource red team instruments such as AzureHound, a Golang binary to perform reconnaissance, and ROADtools to accessibility knowledge in a target’s cloud surroundings. The attacks even more have been noticed working with Azure Arc to create persistence by connecting to an Azure membership controlled by the menace actor.
Alternate attack chains mounted by Peach Sandstorm have entailed the exploitation of security flaws in Atlassian Confluence (CVE-2022-26134) or Zoho ManageEngine (CVE-2022-47966) to get original access.
Approaching WEBINARIdentity is the New Endpoint: Mastering SaaS Security in the Contemporary Age
Dive deep into the long run of SaaS security with Maor Bin, CEO of Adaptive Shield. Explore why identification is the new endpoint. Protected your location now.
Supercharge Your Expertise
Some other notable facets of the publish-compromise exercise problem the deployment of AnyDesk distant checking and management tool to sustain accessibility, EagleRelay to tunnel visitors again to their infrastructure, and leveraging Golden SAML attack tactics for lateral motion.
“Peach Sandstorm also designed new Azure subscriptions and leveraged the entry these subscriptions offered to carry out added attacks in other organizations’ environments,” Microsoft claimed.
“As Peach Sandstorm ever more develops and utilizes new capabilities, businesses should establish corresponding defenses to harden their attack surfaces and increase expenses for these attacks.”
Observed this write-up exciting? Comply with us on Twitter and LinkedIn to read through additional distinctive content material we post.
Some pieces of this article are sourced from:
thehackernews.com

 Microsoft Uncovers Flaws in ncurses Library Affecting Linux and macOS Systems
Microsoft Uncovers Flaws in ncurses Library Affecting Linux and macOS Systems