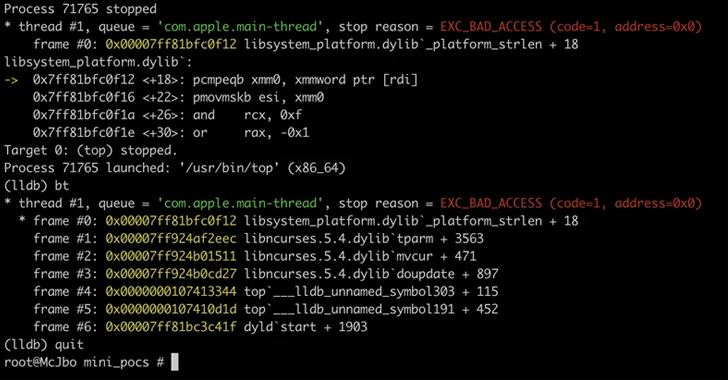
A established of memory corruption flaws have been uncovered in the ncurses (shorter for new curses) programming library that could be exploited by threat actors to run destructive code on vulnerable Linux and macOS programs.
“Using environment variable poisoning, attackers could chain these vulnerabilities to elevate privileges and run code in the targeted program’s context or conduct other destructive actions,” Microsoft Threat Intelligence scientists Jonathan Bar Or, Emanuele Cozzi, and Michael Pearse reported in a technical report posted today.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The vulnerabilities, collectively tracked as CVE-2023-29491 (CVSS score of 7.8), have been dealt with as of April 2023. Microsoft claimed it also worked with Apple on addressing the macOS-distinct issues similar to these flaws.
Natural environment variables are user-defined values that can be made use of by many plans on a process and can have an affect on the manner in which they behave on the technique. Manipulating the variables can result in apps to execute in any other case unauthorized functions.
Microsoft’s code auditing and fuzzing found that the ncurses library queries for quite a few surroundings variables, together with TERMINFO, which could be poisoned and blended with the determined flaws to attain privilege escalation. Terminfo is a databases that enables plans to use exhibit terminals in a machine-unbiased method.
Upcoming WEBINARIdentity is the New Endpoint: Mastering SaaS Security in the Modern day Age
Dive deep into the upcoming of SaaS security with Maor Bin, CEO of Adaptive Shield. Explore why identification is the new endpoint. Protected your spot now.
Supercharge Your Expertise
The flaws encompass a stack data leak, a parameterized string variety confusion, an off-by-one mistake, a heap out-of-bounds all through terminfo database file parsing, and a denial-of-provider with canceled strings.
“The learned vulnerabilities could have been exploited by attackers to elevate privileges and run code within a focused program’s context,” the scientists reported. “Nevertheless, attaining command of a software as a result of exploiting memory corruption vulnerabilities requires a multi-stage attack.”
“The vulnerabilities may well have required to be chained with each other for an attacker to elevate privileges, these types of as exploiting the stack facts leak to acquire arbitrary study primitives alongside with exploiting the heap overflow to attain a produce primitive.”
Observed this report interesting? Adhere to us on Twitter and LinkedIn to read through a lot more exclusive information we put up.
Some areas of this write-up are sourced from:
thehackernews.com

 Free Download Manager Site Compromised to Distribute Linux Malware to Users for 3+ Years
Free Download Manager Site Compromised to Distribute Linux Malware to Users for 3+ Years