Phishing, the theft of users’ credentials or delicate info utilizing social engineering, has been a sizeable threat due to the fact the early days of the internet – and carries on to plague companies now, accounting for a lot more than 30% of all known breaches. And with the mass migration to distant performing all through the pandemic, hackers have ramped up their attempts to steal login qualifications as they consider advantage of the chaos and lack of in-particular person user verification.
This has led to the revival of the previous-university strategy of vishing, which, like phishing on the web, entails employing social engineering in excess of the phone to steal delicate information. Vishing attacks have been on the increase as a final result, with 69% of providers encountering them in 2021, up from 54% in 2020. These attacks often take the sort of career or tech assist cons and can be exceptionally convincing. In August 2020, the FBI alongside with the CISA issued a warning regarding remote end users remaining specific by attackers spoofing organizations’ organization figures and impersonating the IT support desk.
Vishing bypassing 2FA
Just one of the most concerning facets of vishing is the attackers’ ability to bypass two-factor authentication (2FA) security steps. 2FA is a popular kind of multi-factor authentication that necessitates users to present two varieties of details: a password and a 1-time code despatched through SMS.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Attackers accomplish this by impersonating a assistance agent and requesting the victim’s 2FA code more than the phone. If the target supplies the code, the attacker can get whole entry to their account, possibly foremost to financial or private information and facts becoming compromised.
Attackers impersonating as assist desk assist
A frequent instance is when folks receive a pop-up warn boasting that their system has been breached or contaminated with malware and that qualified phone assist is essential to fix the issue. Alternatively, victims might receive a connect with from an alleged tech aid representative from a respected software program supplier, professing that malware has been detected on their device. The attacker will check out to influence the consumer to obtain remote obtain computer software below the pretext of corporate IT assist desk representatives. This is the last stage of the fraud, right after which it’s checkmate for the unsuspecting victims and a potential payday for the attackers.
Attackers impersonating the assistance desk is clearly operating: in July 2020, Twitter experienced a key security breach when hackers used a vishing fraud to properly access dozens of higher-profile accounts, including people of Barack Obama, Joe Biden, Jeff Bezos, and Elon Musk. The attackers made use of these accounts to tweet a bitcoin rip-off, ensuing in the swift theft of about $100,000. As opposed to standard ripoffs, these attacks goal very carefully selected folks by gathering comprehensive information about them from social media and other public sources. This information is then utilized to recognize staff members who are most probable to cooperate and have access to the wanted methods, at which level attackers are primed and ready to wreak havoc.
A twist as attackers get in touch with the help desk & impersonate finish-buyers
Social engineering attacks are cautiously fabricated with gathered information and can be made use of to impersonate an conclusion-user on a call to the support desk. An seasoned attacker can very easily obtain responses to security queries from numerous sources, in particular understanding stop-end users set far too considerably particular details on social media and the web.
Microsoft reported that LAPSUS$, a regarded risk group, phone calls on a qualified organization’s enable desk and tries to encourage support staff to reset a privileged account’s qualifications. The group would use formerly collected details, have an English-talking caller converse with the aid desk. They would be ready to solution popular recovery prompts this kind of as “first street you lived on” or “mother’s maiden identify” from data gathered to persuade assist desk personnel of authenticity.
In an additional endeavor to achieve the help desk, slack was utilized. Digital Arts had 780GB of supply code downloaded by hackers presumed to also be LAPSUS$. The danger actors applied the authentication cookies to impersonate an by now-logged-in employee’s account and access EA’s Slack channel, then certain an IT assistance personnel into granting them access to the firm’s inner network.
How can your Assist Desk know who’s really calling
Verifying user identity in the vishing age is extra critical than ever. With the increase of cyber-attacks and social engineering, it’s very important for companies to have security actions in position to safeguard their workers, secure their delicate info, and protect against unauthorized access.
One particular effective way to safeguard towards these sorts of attacks is to put into practice a protected service desk option, which permits for the verification of consumer accounts with current facts beyond just understanding-primarily based authentication. This can be accomplished by sending a just one-time code to the cellular quantity linked with the user’s account or using present authentication products and services to verify callers.
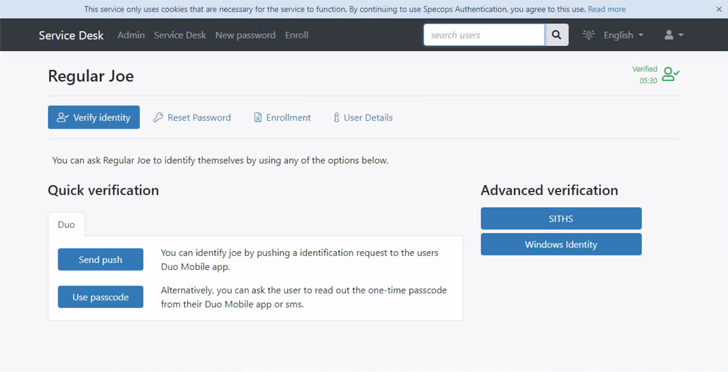
Imposing person authentication is a further essential facet of Specops Protected Provider Desk. This makes sure that data and password resets are only made available to approved end users, which is vital for preserving higher-security accounts and adhering to regulatory specifications. With a Secure Provider Desk, you can clear away the opportunity for user impersonation by demanding verification with one thing the person has and not just relying on a little something the person – or an attacker – might know.
In addition to verifying and enforcing consumer authentication, a protected service desk also allows for the protected reset or unlocking of user accounts. This is completed only right after the user has been properly confirmed and can be blended with a self-service password reset software to assist with account unlocks and the password reset course of action.
With vishing frauds showing no indicators of slowing down, investing in Specops Secure Service Desk solution could be a critical move for corporations seeking to safeguard their people from even the subtlest of social engineering attempts. By instilling a complete and powerful way to confirm consumer identification, enforce consumer authentication, and reset or unlock person accounts, would-be victims can relaxation certain that they will generally know who’s truly contacting.
Discovered this post attention-grabbing? Adhere to us on Twitter and LinkedIn to browse a lot more exclusive written content we publish.
Some elements of this write-up are sourced from:
thehackernews.com


 Four-year-old iframe flaw allows hackers to steal Bitwarden passwords
Four-year-old iframe flaw allows hackers to steal Bitwarden passwords